Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
(Multiple Choice)
4.7/5  (28)
(28)
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
(Multiple Choice)
4.9/5  (32)
(32)
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
(Multiple Choice)
4.8/5  (37)
(37)
In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT
(Multiple Choice)
4.8/5  (40)
(40)
Which message indicates IKE Phase 2 has completed successfully?
(Multiple Choice)
4.8/5  (30)
(30)
What happens when you run the command: fw sam -J src [Source IP Address] ?
(Multiple Choice)
4.9/5  (38)
(38)
Joey wants to configure NTP on R80 Security Management Server. He decided to do this via WebUI. What is the correct address to access the Web UI for Gaia platform via browser?
(Multiple Choice)
4.7/5  (35)
(35)
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
(Multiple Choice)
4.9/5  (39)
(39)
Which of these attributes would be critical for a site-to-site VPN?
(Multiple Choice)
4.9/5  (43)
(43)
What Identity Agent allows packet tagging and computer authentication?
(Multiple Choice)
4.8/5  (40)
(40)
Fill in the blanks: The _________ collects logs and sends them to the _________ .
(Multiple Choice)
4.8/5  (32)
(32)
Provide very wide coverage for all products and protocols, with noticeable performance impact. 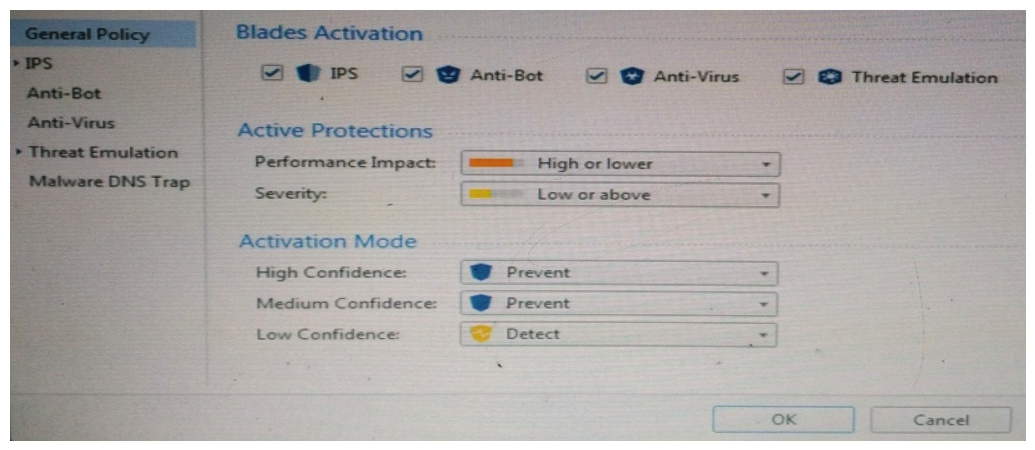 How could you tune the profile in order to lower the CPU load still maintaining security at good level?
How could you tune the profile in order to lower the CPU load still maintaining security at good level?
(Multiple Choice)
4.9/5  (29)
(29)
Which Check Point software blade monitors Check Point devices and provides a picture of network and security performance?
(Multiple Choice)
4.9/5  (34)
(34)
Default port numbers for an LDAP server is ______ for standard connections and _______ SSL connections.
(Multiple Choice)
4.8/5  (37)
(37)
Customer's R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
(Multiple Choice)
4.9/5  (35)
(35)
In a Network policy with Inline layers, the default action for the Implied last rule is ________ all traffic. However, in the Application Control policy layer, the default action is ________ all traffic.
(Multiple Choice)
4.7/5  (39)
(39)
Showing 121 - 140 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)