Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Which policy type is used to enforce bandwidth and traffic control rules?
(Multiple Choice)
4.8/5  (43)
(43)
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted communication. Which of the following methods is BEST to accomplish this task?
(Multiple Choice)
4.7/5  (29)
(29)
Fill in the blank: Service blades must be attached to a ______________.
(Multiple Choice)
4.9/5  (40)
(40)
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem? Choose the BEST answer. 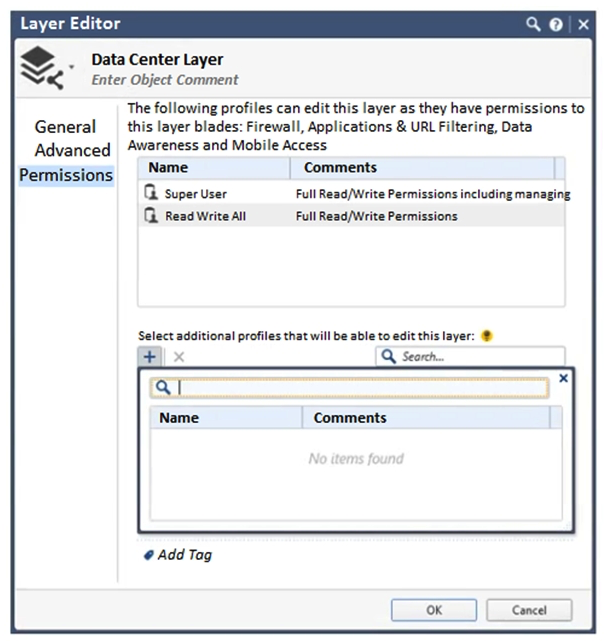
(Multiple Choice)
4.9/5  (29)
(29)
Which one of the following is true about Threat Extraction?
(Multiple Choice)
4.8/5  (33)
(33)
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
(Multiple Choice)
4.8/5  (42)
(42)
How do you configure the Security Policy to provide uses access to the Captive Portal through an external (Internet) interface?
(Multiple Choice)
4.8/5  (36)
(36)
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
(Multiple Choice)
4.8/5  (40)
(40)
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
(Multiple Choice)
4.8/5  (29)
(29)
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
(Multiple Choice)
4.8/5  (28)
(28)
The R80 feature ________ permits blocking specific IP addresses for a specified time period.
(Multiple Choice)
4.9/5  (39)
(39)
The _________ software blade enables Application Security policies to allow, block, or limit website access based on user, group, and machine identities.
(Multiple Choice)
4.7/5  (36)
(36)
Which of the following is TRUE regarding Gaia command line?
(Multiple Choice)
4.9/5  (35)
(35)
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
(Multiple Choice)
4.8/5  (41)
(41)
Which icon indicates in the WebUI that read/write access is enabled?
(Multiple Choice)
4.9/5  (37)
(37)
Showing 201 - 220 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)