Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Consider the Global Properties following settings: 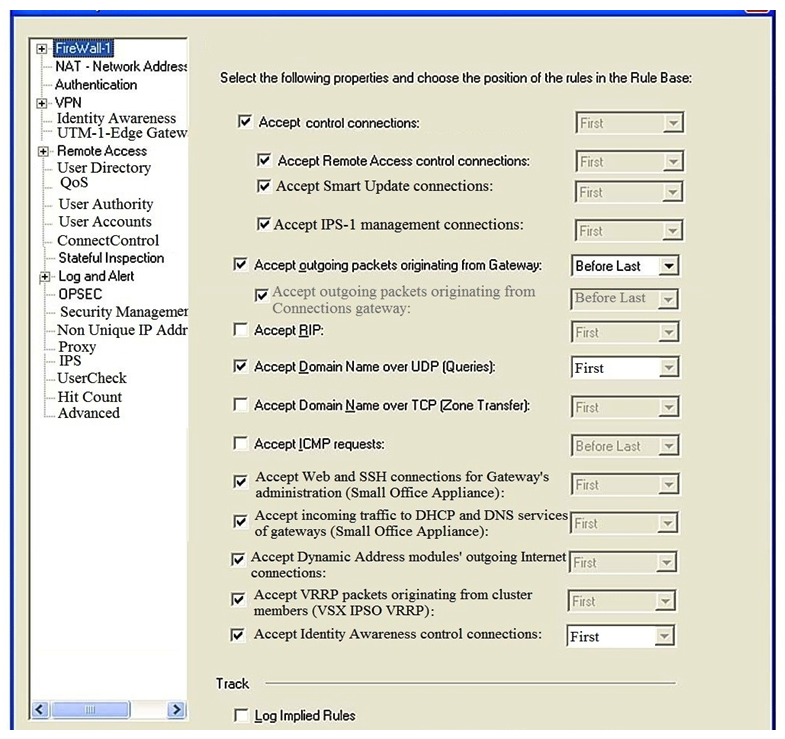 The selected option "Accept Domain Name over UDP (Queries)" means:
The selected option "Accept Domain Name over UDP (Queries)" means:
(Multiple Choice)
4.8/5  (33)
(33)
What Check Point technologies deny or permit network traffic?
(Multiple Choice)
4.8/5  (41)
(41)
Browser-based Authentication sends users to a web page to acquire identities using ________ .
(Multiple Choice)
4.8/5  (37)
(37)
Which firewall daemon is responsible for the FW CLI commands?
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following actions do NOT take place in IKE Phase 1?
(Multiple Choice)
4.9/5  (40)
(40)
With the User Directory Software Blade, you can create R80 user definitions on a(an) ___________ Server.
(Multiple Choice)
4.8/5  (41)
(41)
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?
(Multiple Choice)
4.9/5  (36)
(36)
What type of NAT is a one-to-one relationship where each host is translated to a unique address?
(Multiple Choice)
4.8/5  (43)
(43)
Packages and licenses are loaded from all of theses sources EXCEPT
(Multiple Choice)
4.7/5  (37)
(37)
Fill in the blank: The tool _______ generates a R80 Security Gateway configuration report.
(Multiple Choice)
4.9/5  (35)
(35)
Choose what BEST describes the Policy Layer Traffic Inspection.
(Multiple Choice)
4.8/5  (32)
(32)
One of major features in R80.x SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
(Multiple Choice)
4.8/5  (32)
(32)
To enforce the Security Policy correctly, a Security Gateway requires:
(Multiple Choice)
4.7/5  (31)
(31)
Which component functions as the Internal Certificate Authority for R77?
(Multiple Choice)
4.8/5  (38)
(38)
Which of these components does NOT require a Security Gateway R77 license?
(Multiple Choice)
4.7/5  (35)
(35)
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
(Multiple Choice)
4.8/5  (37)
(37)
Showing 161 - 180 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)