Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A network technician works in a large environment with several thousand users. Due to the needs of the organization, the network manager has asked the technician to design a solution that accommodates the data needs of all the users, while keeping all data on site. Which of the following solutions should the technician implement?
(Multiple Choice)
4.9/5  (31)
(31)
A network administrator has been directed to present the network alerts from the past week to the company's executive staff. Which of the following will provide the BEST collection and presentation of this data?
(Multiple Choice)
4.8/5  (29)
(29)
A network administrator wants to ensure all traffic is inspected and abides by the AUP, and that malicious traffic is stopped. Which of the following features should be enabled on a firewall to meet this requirement?
(Multiple Choice)
4.8/5  (31)
(31)
A network technician is investigating a device that has been reported as responding slowly. Which of the following should the technician check FIRST?
(Multiple Choice)
4.7/5  (37)
(37)
A host has an IP address of 172.28.57.144 and is on the 172.28.57.128 subnet. Which of the following is a correct subnet mask of the host?
(Multiple Choice)
4.8/5  (31)
(31)
An office user cannot access local network drives but has full access to the Internet. A technician troubleshoots the issue and observes the following output of the ipconfig command: 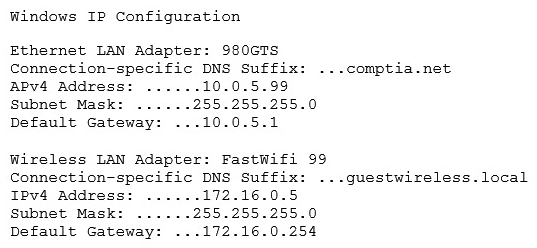 Which of the following would MOST likely allow the network drives to be accessed?
Which of the following would MOST likely allow the network drives to be accessed?
(Multiple Choice)
4.9/5  (33)
(33)
A request is made to open an additional port on a firewall. The request is approved, and the port is opened. Which of the following BEST describes this process?
(Multiple Choice)
4.9/5  (31)
(31)
A technician discovered a company computer had a virus but was unable to remove it. The technician decided to erase the hard drive to eliminate the threat. Which of the following policies did the technician violate?
(Multiple Choice)
4.9/5  (43)
(43)
Which of the following technologies can be implemented on network devices to increase throughput in network storage systems?
(Multiple Choice)
4.8/5  (36)
(36)
A network technician has deployed a new 802.11ac network and discovers some of the legacy POS equipment only supports WPA and 802.11a. Which of the following is the MOST secure method of connecting all devices while avoiding a performance impact to modern wireless devices?
(Multiple Choice)
4.8/5  (30)
(30)
A network technician configures a firewall's ACL to allow outgoing traffic for several popular services such as email and web browsing. However, after the firewall's deployment, users are still unable to retrieve their emails. Which of the following would BEST resolve this issue?
(Multiple Choice)
4.9/5  (33)
(33)
Which of the following technologies would allow a technician to install and run multiple guest operating systems on host hardware?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following would MOST likely provide continuous power during a short brownout?
(Multiple Choice)
4.8/5  (31)
(31)
A technician is investigating a server performance issue. The technician has gathered the server utilization statistics. Which of the following should the technician use to determine which statistics are not in the normal range?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following should be performed on a regular basis to prevent unauthorized access to a company network? (Choose two.)
(Multiple Choice)
4.9/5  (41)
(41)
An employee, who is using a laptop connected to the wireless network, is able to connect to the Internet but not to internal company resources. A systems administrator reviews the following information from the laptop: 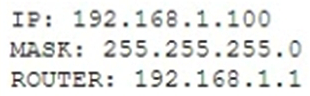 The administrator was expecting to see a network address within 10.100.0.0/23, which is consistent with the company's wireless network. The network administrator verifies the company's wireless network is configured and working properly. Which of the following is the MOST likely cause of this issue?
The administrator was expecting to see a network address within 10.100.0.0/23, which is consistent with the company's wireless network. The network administrator verifies the company's wireless network is configured and working properly. Which of the following is the MOST likely cause of this issue?
(Multiple Choice)
4.7/5  (27)
(27)
Employees at a company report that they are unable to access the Internet. A network technician notices the workstations are receiving IP addresses that do not follow the IP addressing scheme of the corporate network. Upon further inspection, the technician finds an employee has plugged a rogue wireless router into the corporate network. Which of the following settings would have prevented this situation?
(Multiple Choice)
4.8/5  (33)
(33)
A single PRI can deliver multiple voice calls simultaneously using which of the following Layer 1 technologies?
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following provides redundancy on a file server to ensure the server is still connected to a LAN even in the event of a port failure on a switch?
(Multiple Choice)
4.9/5  (29)
(29)
A technician is troubleshooting intermittent connectivity on a line-of-sight wireless bridge. Which of the following tools should the technician use to determine the cause of the packet loss?
(Multiple Choice)
4.9/5  (41)
(41)
Showing 201 - 220 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)