Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
To increase speed and availability, a high-traffic web application was split into three servers recently and moved behind a load balancer. Which of the following should be configured on the load balancer to allow for a single destination?
(Multiple Choice)
4.9/5  (28)
(28)
A customer cannot access a company's secure website. The company's network security is reviewing the firewall for the server and finds the following output: 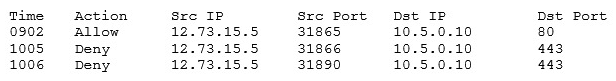 Which of the following changes should be made to allow all customers to access the company's secure website?
Which of the following changes should be made to allow all customers to access the company's secure website?
(Multiple Choice)
4.8/5  (28)
(28)
A network technician performs a wireless site survey at a company building and identifies that the cafeteria is not covered by a wireless signal. The cafeteria is located in a medium-size, square-shaped room. Which of the following types of WAP antenna should the technician install in the center of the cafeteria to provide the BEST coverage?
(Multiple Choice)
4.9/5  (29)
(29)
Which of the following is created on a 48-port switch with five active VLANs?
(Multiple Choice)
4.8/5  (36)
(36)
A network administrator has created a new VLAN for the server and clients within the accounting department and wants to outline how it integrates with the existing network. Which of the following should the administrator create?
(Multiple Choice)
4.9/5  (38)
(38)
A network technician needs to install new network cables. The technician will be running the cables in the air return space above the drop ceiling. Which of the following cable types should be installed?
(Multiple Choice)
4.8/5  (38)
(38)
Ann, a network technician, has relocated a rack that contains the networking and server equipment from the third floor to the sixth floor. To connect the rack-mounted router to the media converter in the first-floor MDF, she extended the length of the original 197ft (60m) Cat5e cable to 395ft (120m) by attaching another 197ft (60m) cable with an RJ45 coupler. After the move, users report intermittent connectivity to external websites, although connectivity to internal hosts has not changed. Which of the following is a network performance issue that is MOST likely causing this issue?
(Multiple Choice)
4.8/5  (35)
(35)
A network manager is drafting a document that outlines what employees can and cannot do when using personal tablets that are connected to the network. Which of the following is the manager drafting?
(Multiple Choice)
4.8/5  (38)
(38)
A network administrator has discovered a low-end managed switch connected to the company's LAN. While reading about the device's specifications on the manufacturer's website, the administrator discovers the switch does not support a command-line interface for administration. Which of the following remote access methods should the administrator use to log in to the switch?
(Multiple Choice)
4.9/5  (39)
(39)
A small company has decided to use a single virtual appliance to filter spam as well as reverse proxy and filter traffic to its internal web server. Which of the following has the company MOST likely deployed?
(Multiple Choice)
4.8/5  (40)
(40)
Which of the following would allow a device to maintain the same IP address lease based on the physical address of the network card?
(Multiple Choice)
4.8/5  (30)
(30)
A network administrator wants to narrow the scope of a subnet to two usable IP addresses within a class C network. Which of the following is the correct CIDR notation?
(Multiple Choice)
4.7/5  (35)
(35)
A network technician installs a web server on the firewall. Which of the following methods should the technician implement to allow access to outside users without giving access to the inside network?
(Multiple Choice)
4.7/5  (34)
(34)
An ISP technician frequently needs to administer a router remotely in the event of a configuration error or WAN outage. Which of the following technologies would facilitate the required connectivity?
(Multiple Choice)
4.8/5  (27)
(27)
A user reports network resources can no longer be accessed. The PC reports a link but will only accept static IP addresses. The technician pings other devices on the subnet, but the PC displays the message Destination unreachable . Which of the following are MOST likely the causes of this issue? (Choose two.)
(Multiple Choice)
4.8/5  (41)
(41)
To achieve a more efficient and secure work environment, a company needs a way to control what is being accessed on the Internet using corporate resources. Which of the following devices should be used to accomplish this task? (Choose two.)
(Multiple Choice)
4.8/5  (28)
(28)
A technician has been assigned to capture packets on a specific switchport. Which of the following switch features MUST be used to accomplish this?
(Multiple Choice)
4.8/5  (34)
(34)
A contractor is setting up and configuring conference rooms for a convention. The contractor sets up each room in the conference center to allow wired Internet access going to individual tables. The contractor measured the distance between the hotel's patch panel to the jack, and the distance is within Cat 5e specifications. The contractor is concerned that the room will be out of specification if cables are run in each room from the wall jacks. Which of the following actions should the contractor take to ensure the cable runs meet specifications and the network functions properly?
(Multiple Choice)
4.8/5  (36)
(36)
A telecommunications provider has just deployed a new OC-12 circuit at a customer site. While the circuit showed no errors from the provider end to the customer's demarcation point, a network administrator is trying to determine the cause of dropped packets and errors on the circuit. Which of the following should the network administrator do to rule out any problems at Layer 1? (Choose two.)
(Multiple Choice)
5.0/5  (33)
(33)
An attacker has inserted a hub into a trunk link on the local network in an attempt to access the management subnet to attack the networking devices. Which of the following attacks can be used on a trunk link to provide access to the management subnet?
(Multiple Choice)
4.9/5  (31)
(31)
Showing 501 - 520 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)