Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following is the correct port number for NTP?
(Multiple Choice)
4.8/5  (40)
(40)
A new application is being deployed. The application team has asked the network team to monitor network performance and create alerts if fluctuations in the round-trip time for that traffic occur. Which of the following should the network team monitor to meet this requirement?
(Multiple Choice)
4.9/5  (37)
(37)
The IT manager at a small firm is in the process of renegotiating an SLA with the organization's ISP. As part of the agreement, the organization will agree to a dynamic bandwidth plan to provide 150Mbps of bandwidth. However, if the ISP determines that a host on the organization's internal network produces malicious traffic, the ISP reserves the right to reduce available bandwidth to 1.5 Mbps. Which of the following policies is being agreed to in the SLA?
(Multiple Choice)
4.8/5  (27)
(27)
A network technician is repurposing a switch that has been in storage for some time. The device has been wiped to factory defaults. Which of the following should be done FIRST to ensure the device has been hardened before configuration?
(Multiple Choice)
5.0/5  (35)
(35)
A network technician has discovered a rogue access point placed under an empty cubicle desk. Which of the following should the technician perform to ensure another cannot be placed on the network?
(Multiple Choice)
4.8/5  (29)
(29)
After setting up in a temporary office, Joe tries to access the company's wireless network. Following several attempts, Joe is able to get an IP, but cannot access network resources. Which of the following is the MOST likely cause of this error when trying to connect to the company's wireless network?
(Multiple Choice)
4.7/5  (34)
(34)
Which of the following is a vulnerable system designed to detect and log unauthorized access?
(Multiple Choice)
4.8/5  (39)
(39)
Which of the following use cases would justify the deployment of an mGRE hub-and-spoke topology?
(Multiple Choice)
5.0/5  (39)
(39)
A company's Chief Information Security Officer (CISO) has decided to increase overall network security by implementing two-factor authentication. All users already have username/password combinations and require an additional factor of authentication. Which of the following would satisfy the requirements?
(Multiple Choice)
4.7/5  (33)
(33)
A website administrator is concerned the company's static website could be defaced by hacktivists or used as a pivot point to attack internal systems. Which of the following should a network security administrator recommend to assist with detecting these activities?
(Multiple Choice)
4.8/5  (31)
(31)
A user no longer has access to network resources after a recent office move, but all other users in the building are able to connect at 100MB connections. After further investigation, a network technician notices the following information: 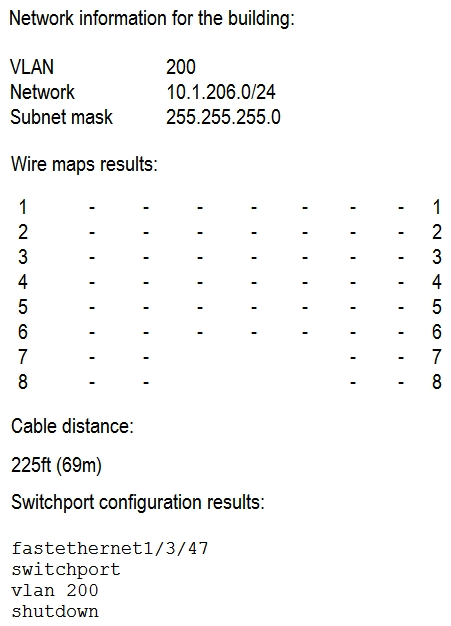 Which of the following is causing the network connection issues?
Which of the following is causing the network connection issues?
(Multiple Choice)
4.7/5  (35)
(35)
Which of the following is a network device that is responsible for separating collision domains?
(Multiple Choice)
4.9/5  (35)
(35)
Two buildings used to be connected by a wireless bridge, but they are upgrading to fiber. Which of the following new devices would be required at the demarcation points?
(Multiple Choice)
5.0/5  (42)
(42)
A network administrator is responding to a help desk ticket, which states an unknown wireless access point is broadcasting in a specific area. Upon investigation, the administrator finds that a user brought a wireless access point from home and plugged it into the corporate network. This resulted in an attacker using the unsecured wireless LAN to gain access to the network. Which of the following should the network administrator have done to BEST prevent this problem?
(Multiple Choice)
4.7/5  (38)
(38)
Which of the following manages the delegation of physical equipment to the virtual components?
(Multiple Choice)
4.7/5  (36)
(36)
A company deploys many workers in the field who remotely access files from a server at headquarters. Leadership is concerned about the risks posed when field workers update these files from unsecured networks. Which of the following policy changes can the company make to MOST improve the confidentiality of connections when connecting remotely? (Choose two.)
(Multiple Choice)
4.9/5  (36)
(36)
A technician is replacing a failed SOHO router for a customer who has an existing switch, cable modem, and static IP address. The user has a web server that faces the Internet so users can visit and leave comments. Which of the following BEST describes the correct configuration for this customer's requirements?
(Multiple Choice)
4.8/5  (44)
(44)
A network administrator needs to implement a new IP subnet containing 29 hosts. It is possible that the number of hosts in that subnet could eventually double. The company only has a single, unused public IP network left to work with: 164.10.12.0/24. Which of the following would be the BEST way to divide this network without wasting addresses?
(Multiple Choice)
4.8/5  (43)
(43)
Joe, a user, reports intermittent connectivity issues, but a technician notices that the only time Joe has issues is when he is logged into the database. Losing connection after authenticating to a database, but still having access to network resources such as file/print services and email, would MOST likely be caused by:
(Multiple Choice)
4.8/5  (36)
(36)
A network engineer wants to change how employees authenticate to the wireless network. Rather than providing a pre-shared key, the engineer wants employees to be able to authenticate with the same unique company user ID and password they use for accessing other services, such as email and document sharing. The engineer also wants to receive daily reports of login attempts on the wireless network. Which of the following should be installed to achieve this goal?
(Multiple Choice)
4.7/5  (36)
(36)
Showing 281 - 300 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)