Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A network extension needs to be run to a location 500ft (152m) from the nearest switch. Which of the following solutions would work BEST? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
A user has reported an issue with wireless VoIP phones dropping calls during business hours. When working late or in the evenings, the user does not experience call drops. When the network technician investigates the issue, all WAPs have balanced the number of connections evenly and are not dropping off the network. The network technician connects to the wireless network in the user's office and starts a continuous ping to an external server. The results show a drastic and varied response time for each packet. Which of the following is the MOST likely cause of the dropped calls?
(Multiple Choice)
4.8/5  (26)
(26)
A store owner would like to have secure wireless access available for both equipment and patron use. Which of the following features should be configured to allow different wireless access through the same equipment?
(Multiple Choice)
4.8/5  (35)
(35)
A user reports a laptop wireless connection is working at the user's desk but not in a recent building addition. A network administrator logs into the wireless controller, searches for the user's MAC address, and receives the following results: 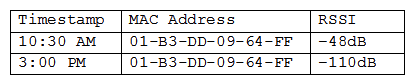 Which of the following describes the reason for the issue?
Which of the following describes the reason for the issue?
(Multiple Choice)
4.9/5  (33)
(33)
A human resources manager notifies the IT manager the night before an employee will be terminated so the employee's access rights can be removed. Which of the following policies is being exercised?
(Multiple Choice)
4.7/5  (39)
(39)
A user does not have access to network services but has Internet access. The technician notices the computer has an IP address of 192.168.1.144 when the network is 10.10.10.0. Which of the following is MOST likely the issue?
(Multiple Choice)
4.7/5  (33)
(33)
A security manager asks a technician to install a network device that will provide information about attacks against the network but will not stop them. Which of the following devices is MOST suited for this task?
(Multiple Choice)
5.0/5  (31)
(31)
Which of the following WAN technologies is MOST preferred when developing a VoIP system with 23 concurrent channels?
(Multiple Choice)
4.8/5  (44)
(44)
The corporate head office has assigned the subnet of 10.1.100.0/24 to a network technician. The technician wants to create subnets for the finance department, human resources, and IT. Given the following device counts: Finance: 70 devices Human resources: 38 devices IT: 16 devices Which of the following outlines how the technician should allocate the address space given?
(Multiple Choice)
4.9/5  (43)
(43)
A new datacenter is being created, and management is trying to control access to that area. Which of the following are the BEST choices for providing access to the new datacenter? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
A network administrator is purchasing a mobile phone for a manager who is traveling internationally. The phone needs to be able to make and receive calls in multiple countries outside of North America. Which of the following cellular technologies should the administrator look for in the phone?
(Multiple Choice)
4.8/5  (35)
(35)
A network technician is configuring a wireless network at a branch office. Users at this office work with large files and must be able to access their files on the server quickly. Which of the following 802.11 standards provides the MOST bandwidth?
(Multiple Choice)
4.8/5  (40)
(40)
A network technician has been asked to install an additional switch in an IDF, but all of the single-mode fiber is in use between the IDF and MDF. The technician has deployed new transceivers that allow for the use of a single fiber stand, providing the additional fiber needed for the new switch. Which of the following has the technician deployed?
(Multiple Choice)
4.7/5  (41)
(41)
Which of the following are characteristics of jumbo frames? (Choose two.)
(Multiple Choice)
4.8/5  (30)
(30)
A wireless technician needs to deploy a single 802.11 standard that supports both 2.4GHz and 5GHz frequencies with up to 40MHz channel widths. Which of the following wireless standards should the technician configure?
(Multiple Choice)
4.8/5  (31)
(31)
A network technician receives reports indicating some users are unable to gain access to any network resources. During troubleshooting, the technician discovers the workstations have an IP address of 169.254.x.x. Which of the following is the MOST likely cause?
(Multiple Choice)
4.8/5  (34)
(34)
A user reports that a laptop cannot connect to the Internet despite the fact the wireless Internet was functioning on it yesterday. The user did not modify the laptop in any way, and the wireless Internet is functional on other users' laptops. Which of the following issues should be reviewed to help the user to connect to the wireless network?
(Multiple Choice)
4.7/5  (26)
(26)
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
(Multiple Choice)
4.8/5  (36)
(36)
Ann, a new employee within a department, cannot print to any of the printers in the department or access any of the resources that others can. However, she can access the Internet. The network engineer has confirmed that Ann's account has been set up the same as the others. There are no access lists restricting Ann's access. Which of the following could be the issue for this lack of access?
(Multiple Choice)
4.9/5  (33)
(33)
A network technician is configuring a firewall access list to secure incoming connections to an email server. The internal address of this email server is 192.168.1.143. The firewall should allow external email servers to send email to the email server. The email server also supports client access via a web browser. Only secure protocols should be used, and only the necessary ports should be open. Which of the following ACL rules should be configured in the firewall's WAN port? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
Showing 41 - 60 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)