Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following should a network administrator deploy to control all preventive security measures?
(Multiple Choice)
4.8/5  (41)
(41)
Which of the following is the MOST secure type of remote administration?
(Multiple Choice)
4.9/5  (38)
(38)
A bookstore uses a Faraday cage to comply with credit card regulations. Customers report that their cellular phones have no signal when they are in the bookstore. Which of the following is the MOST likely cause?
(Multiple Choice)
4.9/5  (43)
(43)
A new employee is unable to access any network resources. All other users are able to access the network at 100Mbps. No IP address, subnet mask, or default gateway is displayed on the new employee's workstation. The network administrator reterminates all connectors using the correct standard. Upon further investigation, the network administrator also notices the following: Wire map results from the user patch cable to the patch cable connecting to the switch: Pins 5 and 7 are short. The distance is 200ft (61m). Additional observations on the switch: The VLAN is set correctly. The port is not disabled. The duplex/speed settings are correct. Port LEDs are off for that port. The port is set to untagged. Which of the following is the MOST likely reason the new employee is having network issues?
(Multiple Choice)
4.8/5  (36)
(36)
A network administrator is redesigning network security after an attack. During the attack, an attacker used open cubicle locations to attach devices to the network. The administrator wants to be able to monitor future attacks in a safe environment and determine the method of attack. Which of the following should the administrator do to BEST meet this requirement?
(Multiple Choice)
4.9/5  (37)
(37)
A switch vendor recently released a patch to fix a critical vulnerability found in its switch OS. Which of the following should a network administrator do NEXT according to best practices?
(Multiple Choice)
4.9/5  (36)
(36)
A company has hundreds of nodes on a single subnet and has decided to implement VLANs. Which of the following BEST describes the benefit of this approach?
(Multiple Choice)
4.8/5  (37)
(37)
A technician wants to have the ability to transfer files from home to the company's network on a regular basis. Which of the following is a remote access protocol the technician can utilize to bypass interactive user authentication by using a list of known host public keys?
(Multiple Choice)
4.9/5  (35)
(35)
A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme. Which of the following has the network technician discovered?
(Multiple Choice)
4.9/5  (32)
(32)
A Chief Information Officer (CIO) wants a third party to verify the security surrounding an enterprise SQL database server. Which of the following services should the CIO implement?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following storage network technologies has the HIGHEST throughput?
(Multiple Choice)
4.9/5  (34)
(34)
A network technician needs to dedicate a range of addresses in DHCP for statically assigned servers and network devices. Which of the following should be configured to BEST accomplish this?
(Multiple Choice)
4.9/5  (37)
(37)
A network administrator is reviewing the following output from a switch: 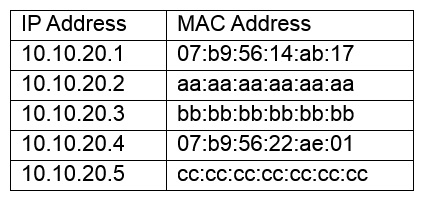 Which of the following attacks has occurred on the switch?
Which of the following attacks has occurred on the switch?
(Multiple Choice)
4.8/5  (25)
(25)
A vendor is installing an Ethernet network in a new hospital wing. The cabling is primarily run above the celling grid near air conditioning ducts and sprinkler pipes. Which of the following cable types is required for this installation?
(Multiple Choice)
4.8/5  (37)
(37)
Which of the following protocols is associated with a three-way handshake?
(Multiple Choice)
4.8/5  (33)
(33)
A company runs Linux servers in its own datacenter and also on a popular public cloud service provider. The servers hosted by the cloud provider can only be accessed with proper authorization and are only accessed by the company's datacenter. Which of the following BEST describes the type of cloud architecture being used? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
The security department is looking to install a new IP-based camera. Plugging the camera into the available Ethernet jack does not power on the camera. Upon further investigation, the cable tests fine, and it does provide power to a VoIP phone. Which of the following is MOST likely causing the issue?
(Multiple Choice)
4.9/5  (36)
(36)
A network administrator has noticed many systems on the network have traffic that is anomalous and may be part of a botnet. The administrator wants to implement an access control method that requires a computer to have antivirus software installed before being granted network access. Which of the following should the administrator deploy?
(Multiple Choice)
4.7/5  (41)
(41)
A network engineer is hardening the security of a remote office. The firewall at this location needs to remain accessible for remote management by technicians. The firewall vendor advises disabling port 443 from WAN-facing access. In addition to disabling port 443, which of the following can the engineer do to MOST effectively balance the remote connectivity and security needs for this site?
(Multiple Choice)
4.7/5  (30)
(30)
Joe, a network technician, wants to locally back up several router and switch configurations. He wants to store them on a server that can be accessed easily for recovery without authentication. Which of the following servers should Joe use?
(Multiple Choice)
4.9/5  (40)
(40)
Showing 221 - 240 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)