Exam 10: CompTIA Network+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following components can be used to manage network traffic to all nodes in a hypervisor?
(Multiple Choice)
4.7/5  (36)
(36)
A malicious user sent double-tagged frames on an 802.1Q-enabled port and immediately gained access to additional network resources. Which of the following attacks did the malicious user successfully execute?
(Multiple Choice)
4.8/5  (29)
(29)
A technician is installing a SOHO router. Which of the following should be performed on every installation and periodically maintained to prevent unauthorized access? (Choose two.)
(Multiple Choice)
4.7/5  (28)
(28)
A technician has designed a LAN with redundant switches. Which of the following should be configured to ensure network availability?
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following allows for file-level network storage?
(Multiple Choice)
4.8/5  (29)
(29)
A Chief Information Officer (CIO) wants to move some IT services to a cloud service offering. However, the network administrator still wants to be able to control some parts of the cloud service's networking components. Which of the following should be leveraged to complete this task?
(Multiple Choice)
4.8/5  (27)
(27)
Which of the following protocols is used to transport outgoing mail across networks?
(Multiple Choice)
4.9/5  (40)
(40)
A technician is asked to provide centralized SSID management across the entire WAN. The BEST solution would be to:
(Multiple Choice)
4.9/5  (35)
(35)
A customer wants a technician to implement a solution that will allow its critical on-site servers to continue to function in the event of an extended power outage. Which of the following should the technician recommend?
(Multiple Choice)
4.9/5  (39)
(39)
After a server outage, a technician discovers that a physically damaged fiber cable appears to be the problem. After replacing the cable, the server will still not connect to the network. Upon inspecting the cable at the server end, the technician discovers light can be seen through one of the two fiber strands. Which of the following should the technician do FIRST to reconnect the server to the network?
(Multiple Choice)
4.8/5  (38)
(38)
A company is redesigning its office to remove the divider walls between desks and create an open collaboration area. All network cables are run through the divider walls, and a new wireless network will be installed. Which of the following sets of documents will need to be revised based on the new configuration?
(Multiple Choice)
4.9/5  (31)
(31)
A network technician is troubleshooting a problem with a user's client-to-site VPN connection. The user is unable to establish a connection to the server, but the error message that appears on screen does not contain useful information. Which of the following should the technician do NEXT to troubleshoot the issue?
(Multiple Choice)
4.9/5  (46)
(46)
A network technician is installing a new network switch is looking for an appropriate fiber optic patch cable. The fiber optic patch panel uses a twist-style connector. The switch uses a SFP module. Which of the following connector types should the fiber patch cable have?
(Multiple Choice)
4.9/5  (39)
(39)
A network administrator is going to be performing a major upgrade to the network. Which of the following should the administrator use in case of a failure?
(Multiple Choice)
5.0/5  (25)
(25)
Which of the following BEST explains why a firewall would be subject to international export controls?
(Multiple Choice)
4.9/5  (33)
(33)
A Chief Information Officer (CIO) wants to control the category of sites that employees access when using the Internet web browser. This objective must be achieved to be compliant with corporate policy and avoid some security and legal risks. Which of the following devices would BEST accomplish this task? (Choose two.)
(Multiple Choice)
4.9/5  (29)
(29)
Log files show the admin user has logged into a public-facing device on several occasions in the evening. None of the technicians admit to doing any after-hours work, and the password has been changed several times but failed to prevent the logins. Which of the following should be the NEXT step to attempt to harden the device?
(Multiple Choice)
4.9/5  (32)
(32)
A system administrator receives reports from users of odd behavior in regard to a recently installed server. While reviewing the server network configuration, the systems administrator does both a forward and a reverse DNS lookup on the host, along with the network adapter configuration. 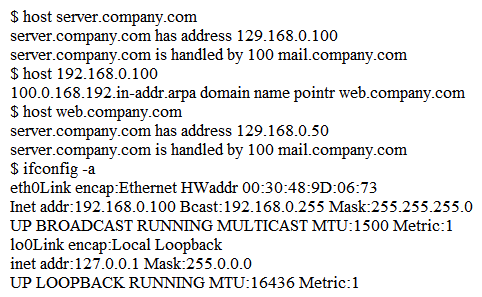 Which of the following is the problem identified in the output above?
Which of the following is the problem identified in the output above?
(Multiple Choice)
4.9/5  (43)
(43)
A technician is connecting a router directly to a PC using the G1/0/1 interface. Without the use of auto-sensing ports, which of the following cables should be used?
(Multiple Choice)
4.9/5  (33)
(33)
Which of the following is BEST for providing real-time equipment theft alerts to the security staff?
(Multiple Choice)
4.7/5  (39)
(39)
Showing 581 - 600 of 829
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)