Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
Free
(Multiple Choice)
4.8/5  (27)
(27)
Correct Answer:
A
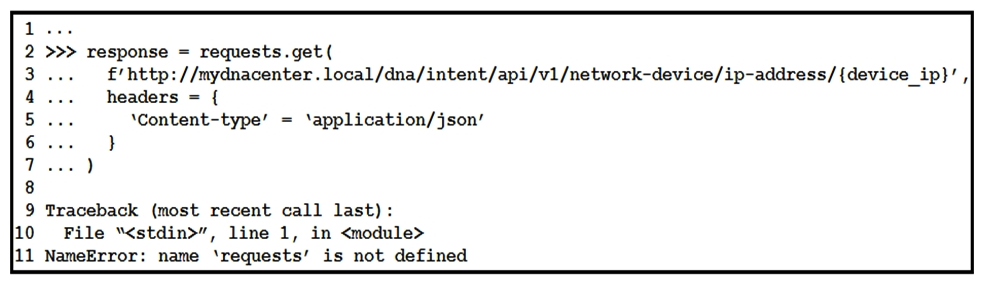 Refer to the exhibit. What is causing the requests code to fail?
Refer to the exhibit. What is causing the requests code to fail?
Free
(Multiple Choice)
4.8/5  (30)
(30)
Correct Answer:
B
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
Free
(Multiple Choice)
4.7/5  (36)
(36)
Correct Answer:
A,C
What are two advantages of using Configuration Management Tools? (Choose two.)
(Multiple Choice)
5.0/5  (35)
(35)
How does eliminating hardcoded or default passwords help to secure an environment?
(Multiple Choice)
4.8/5  (35)
(35)
A DevOps engineer is supporting a containerized application with multiple components running across the Kubernetes cluster. Metrics from the container (CPU and memory) and application (requests per second and heap size) are being collected by Prometheus and displayed with Grafana. Users report transaction timeout problems with the application, but the metric graphs all look within normal levels. Which type of failure would prevent the engineer from seeing the problem using the captured metrics?
(Multiple Choice)
5.0/5  (40)
(40)
Which step must be taken to enable centralized logging in a Kubernetes environment?
(Multiple Choice)
4.8/5  (35)
(35)
Which Kubernetes object is used to create a ClusterIP or NodePort?
(Multiple Choice)
4.9/5  (29)
(29)
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
(Multiple Choice)
4.8/5  (32)
(32)
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?
(Multiple Choice)
4.7/5  (42)
(42)
What is the effective way to manage computing costs in a public cloud?
(Multiple Choice)
4.7/5  (29)
(29)
The E-commerce application is being monitored using AppDynamics. AppDynamics has noticed that the application response has degraded and has identified some thread contention that might be the cause of the delays. Where in the interface does AppDynamics bring this to your attention?
(Multiple Choice)
4.8/5  (36)
(36)
Which interface is most commonly used to integrate logging, monitoring, and alerting applications into your CI/CD pipeline?
(Multiple Choice)
4.8/5  (31)
(31)
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
(Multiple Choice)
4.8/5  (40)
(40)
What is the purpose of using a build tool in software development?
(Multiple Choice)
5.0/5  (33)
(33)
A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
(Multiple Choice)
4.9/5  (37)
(37)
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
(Multiple Choice)
4.8/5  (25)
(25)
Which type of security testing should be performed as a part of a CI/CD pipeline by analyzing the source code itself without compiling the code into a running executable?
(Multiple Choice)
5.0/5  (27)
(27)
Which two actions help limit the attack surface of your Docker container? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
Showing 1 - 20 of 33
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)