Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
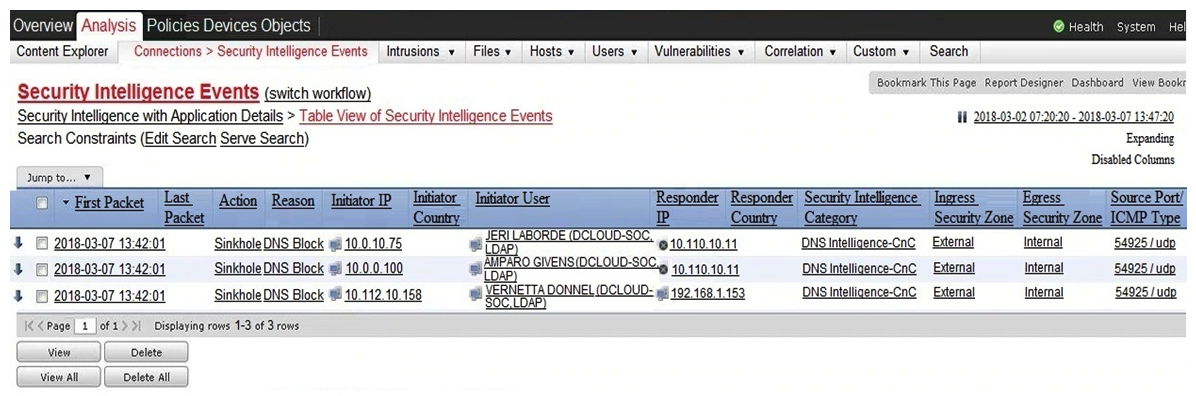 Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)
Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)
Free
(Multiple Choice)
4.9/5  (36)
(36)
Correct Answer:
D,E
What is the difference between statistical detection and rule-based detection models?
Free
(Multiple Choice)
4.9/5  (46)
(46)
Correct Answer:
B
Which metric is used to capture the level of access needed to launch a successful attack?
Free
(Multiple Choice)
5.0/5  (40)
(40)
Correct Answer:
A
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
(Multiple Choice)
4.8/5  (30)
(30)
What is personally identifiable information that must be safeguarded from unauthorized access?
(Multiple Choice)
4.8/5  (34)
(34)
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise. Which kind of evidence is this IP address?
(Multiple Choice)
4.8/5  (33)
(33)
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
(Multiple Choice)
4.7/5  (32)
(32)
Which incidence response step includes identifying all hosts affected by an attack?
(Multiple Choice)
4.7/5  (43)
(43)
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
(Multiple Choice)
4.8/5  (41)
(41)
Which HTTP header field is used in forensics to identify the type of browser used?
(Multiple Choice)
4.7/5  (27)
(27)
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
(Multiple Choice)
4.9/5  (31)
(31)
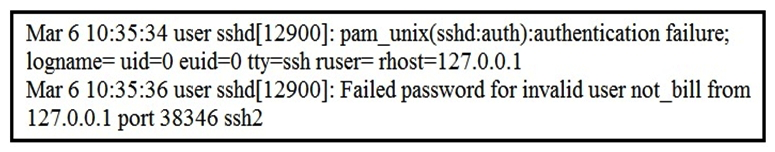 Refer to the exhibit. In which Linux log file is this output found?
Refer to the exhibit. In which Linux log file is this output found?
(Multiple Choice)
4.9/5  (40)
(40)
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
(Multiple Choice)
4.9/5  (42)
(42)
How does an attacker observe network traffic exchanged between two users?
(Multiple Choice)
4.9/5  (36)
(36)
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
(Multiple Choice)
4.9/5  (32)
(32)
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
(Multiple Choice)
4.7/5  (37)
(37)
Which artifact is used to uniquely identify a detected file?
(Multiple Choice)
4.9/5  (25)
(25)
What is the relationship between a vulnerability and a threat?
(Multiple Choice)
4.9/5  (29)
(29)
Showing 1 - 20 of 141
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)