Exam 22: Computer Benefits and Risks
Exam 1: Computer Hardware75 Questions
Exam 2: Peripheral Devices75 Questions
Exam 3: System and Application Software75 Questions
Exam 4: Installing Software75 Questions
Exam 5: Getting Started With Windows 775 Questions
Exam 6: Working With Windows Settings and Accounts75 Questions
Exam 7: Working With Files75 Questions
Exam 8: Getting Started With Application Software75 Questions
Exam 9: Creating a Document75 Questions
Exam 10: Formatting a Document75 Questions
Exam 11: Finalizing a Document75 Questions
Exam 12: Creating a Worksheet75 Questions
Exam 13: Formatting a Worksheet75 Questions
Exam 14: Finalizing a Worksheet75 Questions
Exam 15: Creating a Presentation75 Questions
Exam 16: Finalizing a Presentation75 Questions
Exam 17: Creating a Database75 Questions
Exam 18: Finalizing a Database75 Questions
Exam 19: Networks75 Questions
Exam 20: Working With E-Mail75 Questions
Exam 21: Browsing the Web75 Questions
Exam 22: Computer Benefits and Risks75 Questions
Select questions type
The information that your antivirus software uses to identify and eradicate malicious code is stored in one or more files usually referred to as "virus ____."
(Multiple Choice)
4.8/5  (28)
(28)
The term ____ refers to any program or set of program instructions designed to surreptitiously enter a computer and disrupt its normal operations.
(Multiple Choice)
4.9/5  (38)
(38)
A computer ____ is a set of program instructions that can attach itself to a file, reproduce itself, and spread to other files.
(Multiple Choice)
4.9/5  (41)
(41)
HIPAA helps keep your medical information private and prevents abusive practices, such as when a cash-strapped health care organization sells a list of its pregnant patients to a baby-formula marketing company._________________________
(True/False)
4.9/5  (35)
(35)
You can check the list of cookies on your computer to look for ad-serving cookies.They are typically generated by sites you have never visited and sometimes contain the word "ad" or "____."
(Multiple Choice)
4.7/5  (33)
(33)
In the United States, the Digital Millennium Copyright Act of ____ updated many key aspects of intellectual property law to meet the challenges of new digital realities.
(Multiple Choice)
4.8/5  (36)
(36)
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
-Genevieve drafts a letter to the student body saying to be careful about opening executable files.Genevieve also states that malicious code can be included in ____ files.
(Multiple Choice)
4.7/5  (35)
(35)
When you publish your own material online, it is automatically covered by ____.
(Multiple Choice)
4.9/5  (34)
(34)
____ makes it possible for shoppers to purchase merchandise using their computers.
(Multiple Choice)
4.8/5  (26)
(26)
A copyright notice, such as "Copyright 2010 eCourse Inc." is required by law in order to be protected by copyright.
(True/False)
4.7/5  (48)
(48)
Some Web sites feature banner ads supplied by third-party marketing firms.If you click the ad, this third party can create an ad-serving virus and use it to track your activities at any site containing banner ads from that third party._________________________
(True/False)
4.8/5  (31)
(31)
Often hackers transmit ____ that circulate over the Internet looking for unsecured computer systems.
(Multiple Choice)
5.0/5  (35)
(35)
Unfortunately, there is no software available to block banner and pop-up ads altogether.
(True/False)
4.8/5  (30)
(30)
The Software Information Industry Association (SIIA) is trying to stop illegal software ____.
(Multiple Choice)
4.8/5  (41)
(41)
A data file with a .doc or .xls extension can sometimes contain a ____ virus.
(Multiple Choice)
4.8/5  (36)
(36)
The material published on Web sites, in blogs, and in other online forums is protected by copyright.
(True/False)
4.7/5  (28)
(28)
Several software publishers offer tools that filter out inappropriate Web sites.____ typically comes pre-loaded with a long list of sites that are not child-friendly.
(Multiple Choice)
4.9/5  (26)
(26)
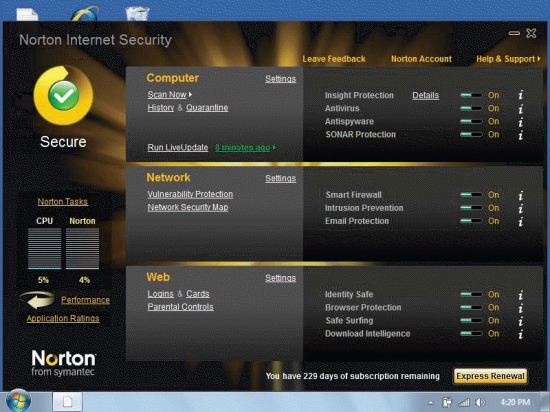 -Referring to the figure above, you have 229 days of the Norton subscription remaining, and LiveUpdate was run eight minutes ago.To stay current, always make sure your ____ is/are up-to-date.
-Referring to the figure above, you have 229 days of the Norton subscription remaining, and LiveUpdate was run eight minutes ago.To stay current, always make sure your ____ is/are up-to-date.
(Multiple Choice)
4.9/5  (36)
(36)
____ usually protect inventions from being used without permission from the inventor.
(Multiple Choice)
4.9/5  (32)
(32)
A(n) ____________________ or "Web bug" is a 1x1 pixel graphic on a Web page.
(Short Answer)
4.9/5  (36)
(36)
Showing 41 - 60 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)