Exam 22: Computer Benefits and Risks
Exam 1: Computer Hardware75 Questions
Exam 2: Peripheral Devices75 Questions
Exam 3: System and Application Software75 Questions
Exam 4: Installing Software75 Questions
Exam 5: Getting Started With Windows 775 Questions
Exam 6: Working With Windows Settings and Accounts75 Questions
Exam 7: Working With Files75 Questions
Exam 8: Getting Started With Application Software75 Questions
Exam 9: Creating a Document75 Questions
Exam 10: Formatting a Document75 Questions
Exam 11: Finalizing a Document75 Questions
Exam 12: Creating a Worksheet75 Questions
Exam 13: Formatting a Worksheet75 Questions
Exam 14: Finalizing a Worksheet75 Questions
Exam 15: Creating a Presentation75 Questions
Exam 16: Finalizing a Presentation75 Questions
Exam 17: Creating a Database75 Questions
Exam 18: Finalizing a Database75 Questions
Exam 19: Networks75 Questions
Exam 20: Working With E-Mail75 Questions
Exam 21: Browsing the Web75 Questions
Exam 22: Computer Benefits and Risks75 Questions
Select questions type
Virus software is a set of utility programs that looks for and eradicates viruses and worms._________________________
(True/False)
4.8/5  (32)
(32)
Although ____ property can be fixed in tangible media the underlying "property" is not necessarily tied to a particular media.
(Multiple Choice)
4.9/5  (35)
(35)
The marketing firms that distribute ad-serving cookies claim that this data is simply used to select and display ads that might interest you.
(True/False)
4.8/5  (30)
(30)
The music industry, the Recording Industry Association of America (RIAA) is attempting to stop rampant ____ music sharing on the Internet.
(Multiple Choice)
4.9/5  (41)
(41)
When setting up wireless encryption, you will create an encryption ____, which works like a password.
(Multiple Choice)
5.0/5  (37)
(37)
Information security refers to the techniques used to protect information from unauthorized access, damage, disclosure, loss, modification, or use._________________________
(True/False)
4.9/5  (28)
(28)
____ is the study of work and work environments, with the goal being to make work environments safer and healthier.
(Multiple Choice)
4.9/5  (31)
(31)
____________________ refers to intangibles, such as ideas, music, art, photos, logos, movies, and programs, that are the result of creativity and intellectual effort.
(Short Answer)
4.8/5  (35)
(35)
Copyright law makes it illegal to copy and distribute protected works without the permission of the author or the author's representative._________________________
(True/False)
4.9/5  (32)
(32)
In order to gain access to a(n) ____________________ Web site, you typically have to register for an account and password.
(Short Answer)
4.8/5  (33)
(33)
____________________ is the use of fraudulent Web sites and e-mail links to trick people into revealing sensitive, personal, and financial information.
(Short Answer)
4.8/5  (38)
(38)
Unlike a virus, which is designed to spread from file to file, a worm is designed to spread from computer to computer over ____.
(Multiple Choice)
4.7/5  (39)
(39)
____________________ occurs when someone obtains your personal information and uses it without your permission to commit fraud or other crimes.
(Short Answer)
4.9/5  (24)
(24)
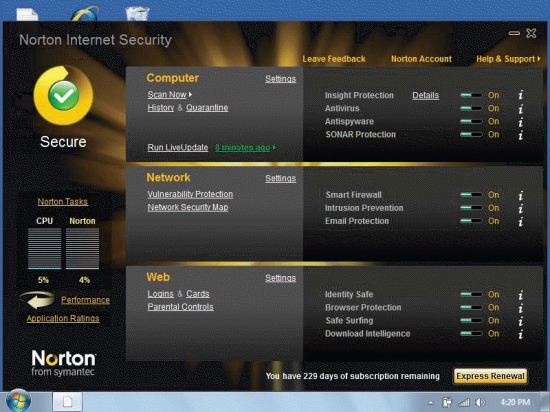 -Referring to the figure above, if these were your settings, ____ would be scanned for viruses.
-Referring to the figure above, if these were your settings, ____ would be scanned for viruses.
(Multiple Choice)
4.8/5  (35)
(35)
Showing 61 - 75 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)