Exam 22: Computer Benefits and Risks
Exam 1: Computer Hardware75 Questions
Exam 2: Peripheral Devices75 Questions
Exam 3: System and Application Software75 Questions
Exam 4: Installing Software75 Questions
Exam 5: Getting Started With Windows 775 Questions
Exam 6: Working With Windows Settings and Accounts75 Questions
Exam 7: Working With Files75 Questions
Exam 8: Getting Started With Application Software75 Questions
Exam 9: Creating a Document75 Questions
Exam 10: Formatting a Document75 Questions
Exam 11: Finalizing a Document75 Questions
Exam 12: Creating a Worksheet75 Questions
Exam 13: Formatting a Worksheet75 Questions
Exam 14: Finalizing a Worksheet75 Questions
Exam 15: Creating a Presentation75 Questions
Exam 16: Finalizing a Presentation75 Questions
Exam 17: Creating a Database75 Questions
Exam 18: Finalizing a Database75 Questions
Exam 19: Networks75 Questions
Exam 20: Working With E-Mail75 Questions
Exam 21: Browsing the Web75 Questions
Exam 22: Computer Benefits and Risks75 Questions
Select questions type
You can violate your own privacy by unintentionally releasing information about yourself that can be exploited by aggressive marketing companies, hackers, and criminals.
Free
(True/False)
4.8/5  (44)
(44)
Correct Answer:
True
A ____ is a snapshot of your computer settings and are essentially backups of the Windows Registry.
Free
(Multiple Choice)
4.8/5  (38)
(38)
Correct Answer:
D
Small ____ tags sewn into clothing communicate with inventory tracking systems.
Free
(Multiple Choice)
4.7/5  (31)
(31)
Correct Answer:
A
A(n) ____________________ is issued by a certificate authority that essentially vouches for the certificate holder's identity.
(Short Answer)
4.9/5  (29)
(29)
The original wireless encryption was called ____ and was designed to provide a level of confidentiality similar to that of a wired network.
(Multiple Choice)
4.8/5  (31)
(31)
Coded software scrambles your data by using a multi-digit key._________________________
(True/False)
4.7/5  (35)
(35)
A typical ____ scam begins with a faked e-mail message that seems to be an official notice from a trusted source, such as a credit card company, online payment service, software vendor, or bank.
(Multiple Choice)
5.0/5  (35)
(35)
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
-A professor contacts Genevieve saying that he thinks he has a computer virus, but he has been on vacation for a month, and has not used his computer.Genevieve explains that ____.
(Multiple Choice)
4.8/5  (33)
(33)
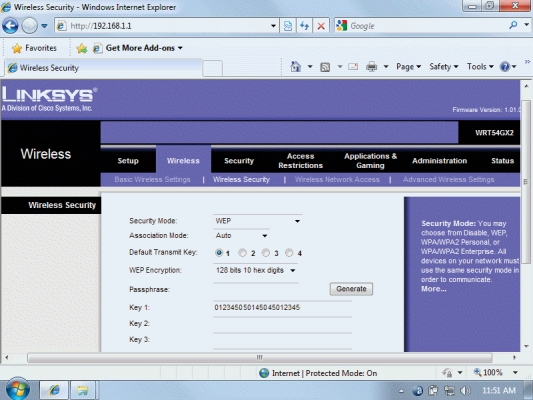 -In the figure above, the "Key 1:" that is shown is also referred to as a(n) ____ key.
-In the figure above, the "Key 1:" that is shown is also referred to as a(n) ____ key.
(Multiple Choice)
4.7/5  (36)
(36)
____ typically protect works such as software, photos, movies, and music.
(Multiple Choice)
4.8/5  (37)
(37)
____________________ refers to any physical method used to prevent works from being copied.
(Short Answer)
4.8/5  (41)
(41)
Most malicious code is stored in executable files, usually with ____ file name extensions.
(Multiple Choice)
4.8/5  (38)
(38)
A ____ worm makes use of information on an infected computer to mail itself to everyone listed in the e-mail address book.
(Multiple Choice)
4.8/5  (44)
(44)
A ____ uses a home-based computer and telecommunications equipment to perform work-related tasks.
(Multiple Choice)
4.8/5  (38)
(38)
Legitimate macros are used to automate common word processing or spreadsheet tasks.
(True/False)
4.8/5  (28)
(28)
Personal information can be defined as any data that is associated with you as an individual.
(True/False)
4.9/5  (30)
(30)
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
-Genevieve has received three reports today, from students, about a computer virus that is spreading from one computer to another automatically with the name "Hello Friend." Genevieve knows the problem is not a virus because computer viruses ____.
(Multiple Choice)
4.8/5  (35)
(35)
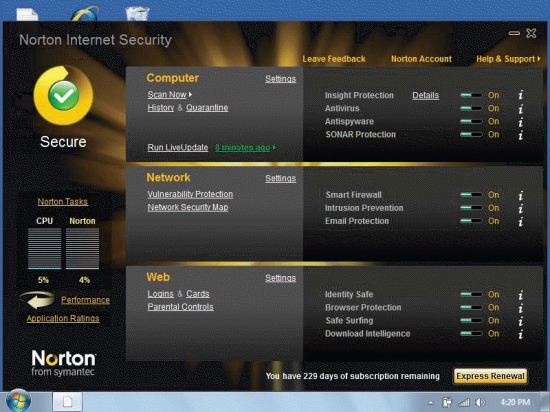 -In the figure above, the Norton Smart firewall is marked on.If Windows Firewall is also turned on, you would ____.
-In the figure above, the Norton Smart firewall is marked on.If Windows Firewall is also turned on, you would ____.
(Multiple Choice)
4.9/5  (27)
(27)
____ use allows you to insert fragments of literary works in research papers without first gaining permission from their authors.
(Multiple Choice)
4.8/5  (37)
(37)
Showing 1 - 20 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)