Exam 30: Computer Safety and Ethics
Exam 1: Computers and Computer Systems46 Questions
Exam 2: Input, Output, and Processing46 Questions
Exam 3: Computer Protection46 Questions
Exam 4: Computer Maintenance46 Questions
Exam 5: Computer-Related Issues46 Questions
Exam 6: Software and Hardware Interaction46 Questions
Exam 7: Software Fundamentals46 Questions
Exam 8: Operating Systems46 Questions
Exam 9: Windows Management46 Questions
Exam 10: Operating System Customization46 Questions
Exam 11: Exploring Microsoft Office 200746 Questions
Exam 12: Getting Started With Word Essentials46 Questions
Exam 13: Editing and Formatting Documents46 Questions
Exam 14: Sharing Documents46 Questions
Exam 15: Working With Tables46 Questions
Exam 16: Enhancing Documents46 Questions
Exam 17: Getting Started With Excel Essentials46 Questions
Exam 18: Organizing and Enhancing Worksheets46 Questions
Exam 19: Creating Formulas and Charting Data46 Questions
Exam 20: Getting Started With Powerpoint Essentials46 Questions
Exam 21: Enhancing Presentations With Multimedia Effects46 Questions
Exam 22: Getting Started With Access Essentials46 Questions
Exam 23: Managing and Reporting Database Information46 Questions
Exam 24: Network Fundamentals46 Questions
Exam 25: Communication Services46 Questions
Exam 26: Communications and Collaboration46 Questions
Exam 27: Using the Internet and the World Wide Web46 Questions
Exam 28: Web Content46 Questions
Exam 29: Technology and Society46 Questions
Exam 30: Computer Safety and Ethics46 Questions
Select questions type
The goal of ____ is to collect information about the user, the user's browsing habits, and other personal information.
(Multiple Choice)
4.8/5  (26)
(26)
Which of the following would be considered the strongest password?
(Multiple Choice)
4.8/5  (36)
(36)
To make sure your e-commerce transactions are secure and to protect your private information, you should ____.
(Multiple Choice)
4.8/5  (34)
(34)
Eavesdropping software can be downloaded free from the Internet and used by a hacker to access an unsecured wireless connection.
(True/False)
4.8/5  (36)
(36)
Before providing personal information or credit card information on an e-commerce site, first verify that the site is secure.
(True/False)
4.7/5  (44)
(44)
Case 30-1 Nelson is a graphic designer who works long hours on his computer. He tries to take precautions to avoid chronic physical maladies such as eyestrain, back problems, and repetitive strain injuries. What kind of furniture should Nelson use to help adapt his equipment and his workplace to fit himself?
(Multiple Choice)
4.8/5  (30)
(30)
FIGURE 30-2 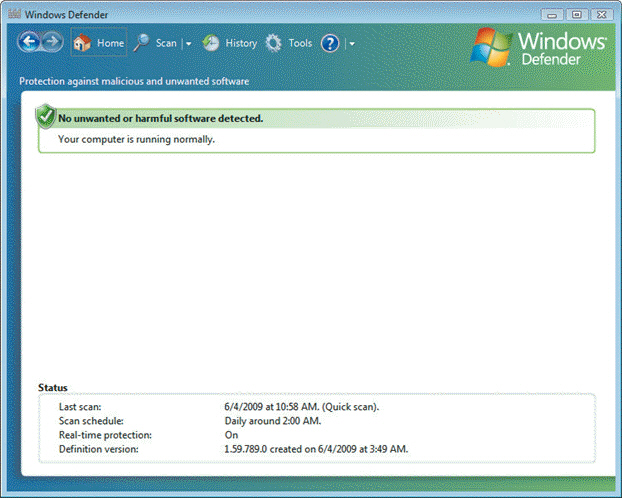 You could use the program shown in Figure 30-2 above to ____.
You could use the program shown in Figure 30-2 above to ____.
(Multiple Choice)
4.8/5  (32)
(32)
Using a notebook computer introduces risks not associated with desktop computers.
(True/False)
4.8/5  (43)
(43)
Why are passwords important? How do you maintain passwords and keep them secure? How do you create a strong password?
(Essay)
4.9/5  (30)
(30)
Hackers often use spyware to control your browser, a practice called ____________________.
(Short Answer)
4.8/5  (31)
(31)
What action might obstruct the air vents in your notebook computer and cause it to overheat?
(Multiple Choice)
4.8/5  (41)
(41)
Case 30-2 Molly has just purchased a router and is setting up a wireless network in her home office. She wants to secure it properly. If Molly does not properly secure her wireless network connection, what could happen if her neighbor uses her broadband connection?
(Multiple Choice)
5.0/5  (35)
(35)
A software firewall is more secure and easier to monitor than a hardware firewall.
(True/False)
4.9/5  (44)
(44)
____________________ are small files that are created when you visit a Web site and are stored on your computer, then accessed again the next time you visit the same site.
(Short Answer)
4.8/5  (43)
(43)
It is the responsibility of a company or individual to protect their data.
(True/False)
4.8/5  (38)
(38)
A(n) public key deciphers the encrypted information in a transmission.
(True/False)
4.9/5  (47)
(47)
Identify the letter of the choice that best matches the phrase or definition.
Correct Answer:
Premises:
Responses:
(Matching)
4.7/5  (46)
(46)
Showing 21 - 40 of 46
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)