Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network. Which testing method did the intruder use?
(Multiple Choice)
4.9/5  (30)
(30)
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
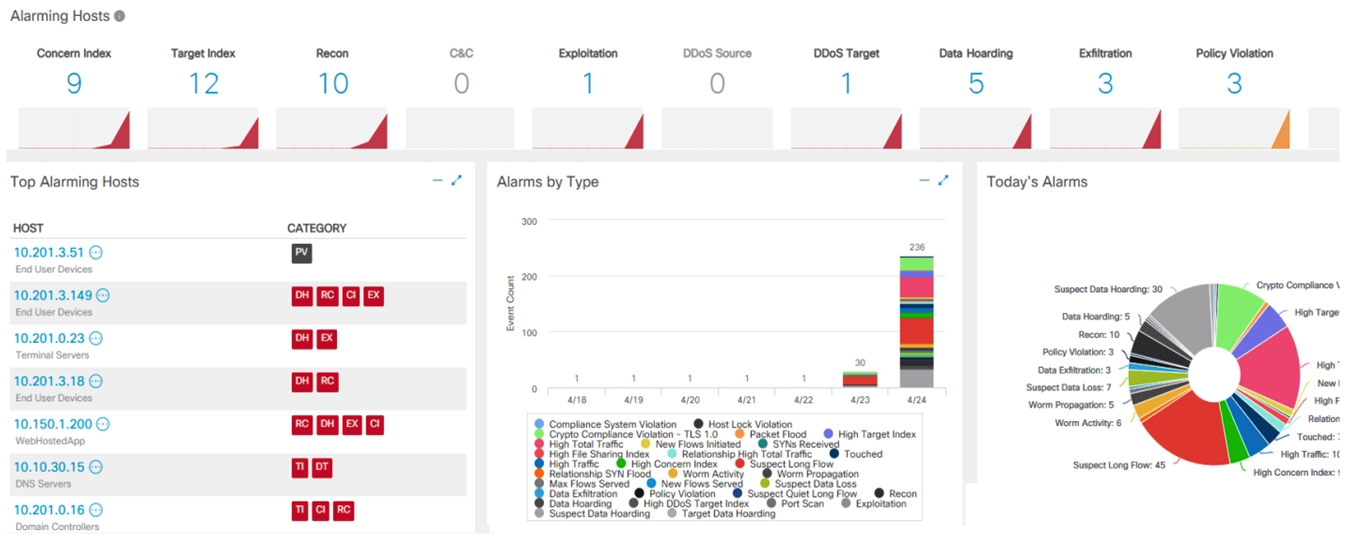 Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
(Multiple Choice)
5.0/5  (35)
(35)
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
(Multiple Choice)
4.7/5  (33)
(33)
Which process is used when IPS events are removed to improve data integrity?
(Multiple Choice)
4.8/5  (40)
(40)
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
(Multiple Choice)
4.8/5  (34)
(34)
Which security monitoring data type requires the largest storage space?
(Multiple Choice)
4.8/5  (41)
(41)
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which technology makes this behavior possible?
(Multiple Choice)
4.8/5  (32)
(32)
What is rule-based detection when compared to statistical detection?
(Multiple Choice)
4.7/5  (28)
(28)
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
(Multiple Choice)
4.8/5  (32)
(32)
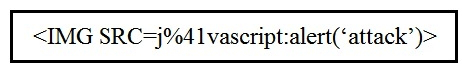 Refer to the exhibit. Which kind of attack method is depicted in this string?
Refer to the exhibit. Which kind of attack method is depicted in this string?
(Multiple Choice)
4.8/5  (38)
(38)
Which type of evidence supports a theory or an assumption that results from initial evidence?
(Multiple Choice)
4.9/5  (34)
(34)
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
(Multiple Choice)
4.7/5  (34)
(34)
Which attack method intercepts traffic on a switched network?
(Multiple Choice)
4.9/5  (37)
(37)
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
(Multiple Choice)
4.9/5  (38)
(38)
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
(Multiple Choice)
4.9/5  (27)
(27)
Which security principle requires more than one person is required to perform a critical task?
(Multiple Choice)
4.9/5  (36)
(36)
Showing 81 - 100 of 141
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)