Exam 6: DevNet Associate (DEVASC)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Refer to the exhibit. 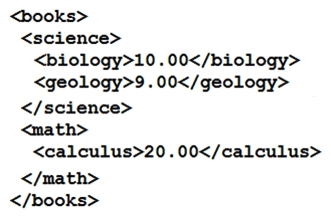 Which JSON is equivalent to the XML-encoded data?
Which JSON is equivalent to the XML-encoded data?
(Multiple Choice)
4.9/5  (29)
(29)
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
(Multiple Choice)
4.8/5  (33)
(33)
A company has written a script that creates a log bundle from the Cisco DNA Center every day. The script runs without error and the log bundles are produced. However, when the script is run during business hours, people report poor voice quality of phone calls. What explains this behavior?
(Multiple Choice)
4.9/5  (35)
(35)
Refer to the exhibit. 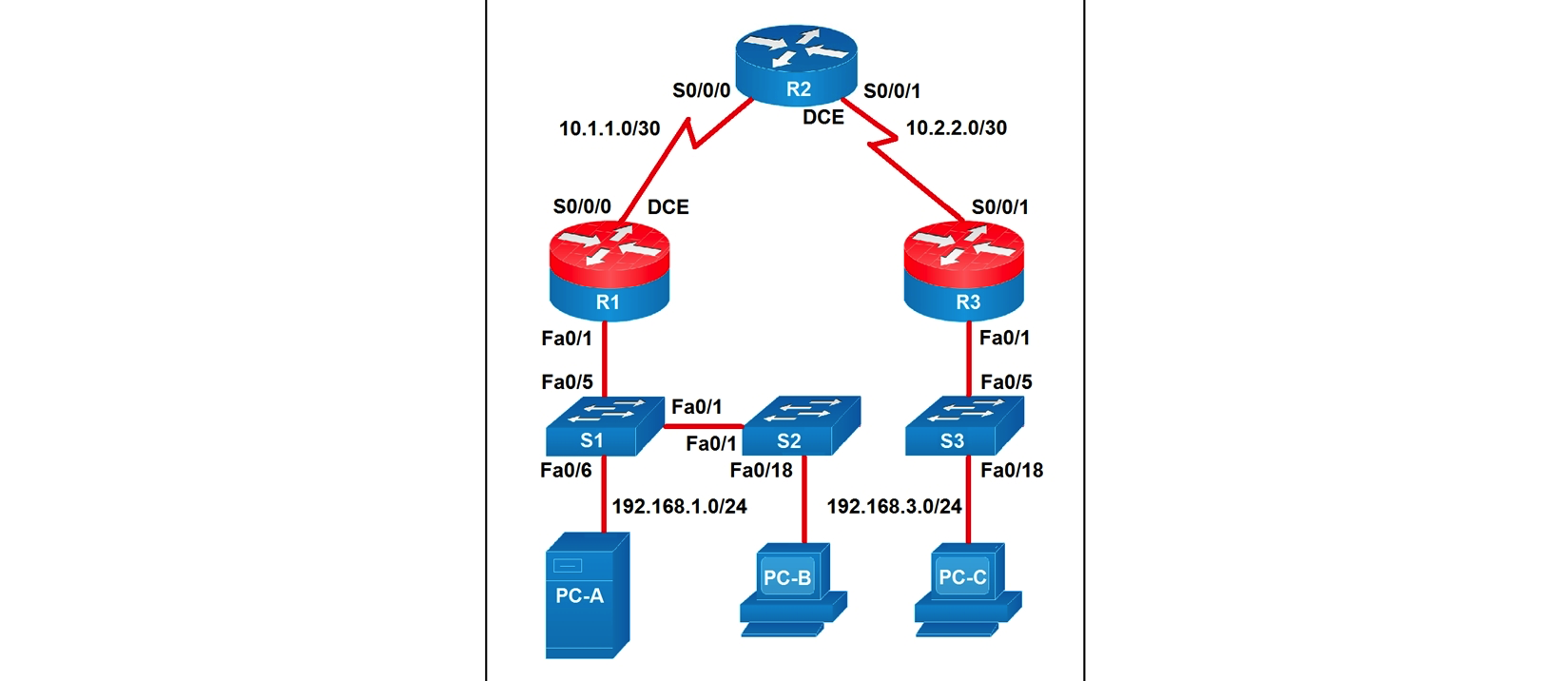 Which two statements about the network diagram are true? (Choose two.)
Which two statements about the network diagram are true? (Choose two.)
(Multiple Choice)
4.9/5  (29)
(29)
Which type of threat occurs when an attacker can send hostile data to an interpreter within an application?
(Multiple Choice)
4.8/5  (41)
(41)
Refer to the exhibit. 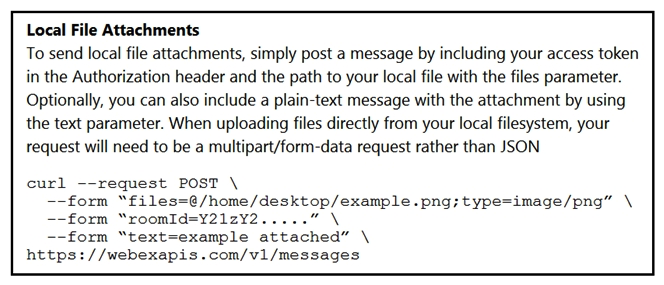 A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get a valid response?
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get a valid response?
(Multiple Choice)
4.8/5  (38)
(38)
Which two statements about JSON and XML are true? (Choose two.)
(Multiple Choice)
4.9/5  (45)
(45)
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?
(Multiple Choice)
4.9/5  (37)
(37)
Which action does the Git command git merge allow the developer to perform?
(Multiple Choice)
4.9/5  (31)
(31)
Which mechanism is used to consume a RESTful API design when large amounts of data are returned?
(Multiple Choice)
4.7/5  (47)
(47)
Which two elements are foundational principles of DevOps? (Choose two.)
(Multiple Choice)
4.9/5  (44)
(44)
What are two security benefits of a Docker-based application? (Choose two.)
(Multiple Choice)
4.8/5  (26)
(26)
Which task is performed because the test-driven development approach is being used?
(Multiple Choice)
4.9/5  (35)
(35)
Refer to the exhibit. 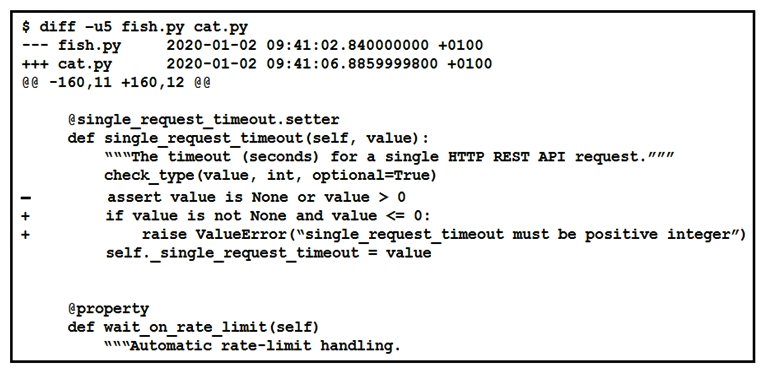 The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)
The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)
(Multiple Choice)
4.9/5  (24)
(24)
An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API?
(Multiple Choice)
4.8/5  (34)
(34)
What is a benefit of using edge computing in an IoT implementation?
(Multiple Choice)
4.7/5  (33)
(33)
What is the purpose of a firewall in application deployment?
(Multiple Choice)
4.7/5  (29)
(29)
Showing 61 - 80 of 134
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)