Exam 28: Implementing Cisco Collaboration Applications (CLICA)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which two APIs are available from Cisco ThreatGRID? (Choose two.)
(Multiple Choice)
4.8/5  (33)
(33)
What are two capabilities of Cisco Firepower Management Center eStreamer? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
 Refer to the exhibit. Which expression prints the text "802.1x"?
Refer to the exhibit. Which expression prints the text "802.1x"?
(Multiple Choice)
4.9/5  (39)
(39)
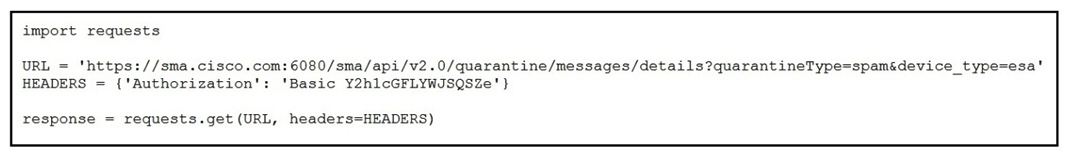 Refer to the exhibit. A security engineer attempts to query the Cisco Security Management appliance to retrieve details of a specific message. What must be added to the script to achieve the desired result?
Refer to the exhibit. A security engineer attempts to query the Cisco Security Management appliance to retrieve details of a specific message. What must be added to the script to achieve the desired result?
(Multiple Choice)
4.7/5  (34)
(34)
Which API is designed to give technology partners the ability to send security events from their platform/service/appliance within a mutual customer's environment to the Umbrella cloud for enforcement?
(Multiple Choice)
4.8/5  (38)
(38)
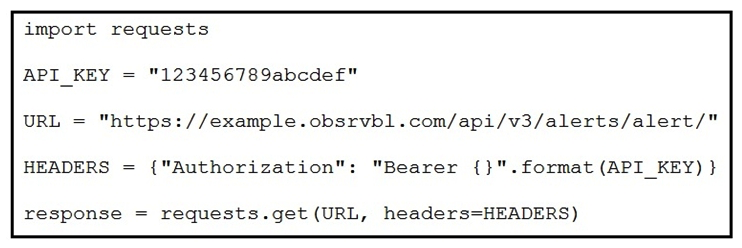 Refer to the exhibit. A security engineer created a script and successfully executed it to retrieve all currently open alerts. Which print command shows the first returned alert?
Refer to the exhibit. A security engineer created a script and successfully executed it to retrieve all currently open alerts. Which print command shows the first returned alert?
(Multiple Choice)
4.8/5  (39)
(39)
In Cisco AMP for Endpoints, which API queues to find the list of endpoints in the group "Finance Hosts," which has a GUID of 6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03 ?
(Multiple Choice)
4.7/5  (39)
(39)
Which two statements describe the characteristics of API styles for REST and RPC? (Choose two.)
(Multiple Choice)
4.9/5  (37)
(37)
Which request searches for a process window in Cisco ThreatGRID that contains the word "secret"?
(Multiple Choice)
4.8/5  (42)
(42)
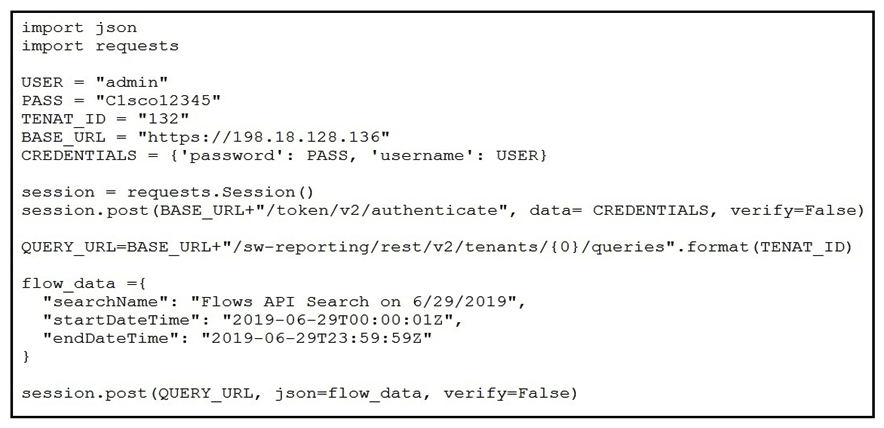 Refer to the exhibit. A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information. Which two actions enable the operator to limit returned data? (Choose two.)
Refer to the exhibit. A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information. Which two actions enable the operator to limit returned data? (Choose two.)
(Multiple Choice)
4.8/5  (27)
(27)
Which query parameter is required when using the reporting API of Cisco Security Management Appliances?
(Multiple Choice)
4.9/5  (27)
(27)
Which two URI parameters are needed for the Cisco Stealthwatch Top Alarm Host v1 API? (Choose two.)
(Multiple Choice)
4.9/5  (42)
(42)
A security network engineer must implement intrusion policies using the Cisco Firepower Management Center API. Which action does the engineer take to achieve the goal?
(Multiple Choice)
4.7/5  (30)
(30)
Which API capability is available on Cisco Firepower devices?
(Multiple Choice)
4.8/5  (38)
(38)
Which URI string is used to create a policy that takes precedence over other applicable policies that are configured on Cisco Stealthwatch?
(Multiple Choice)
4.8/5  (36)
(36)
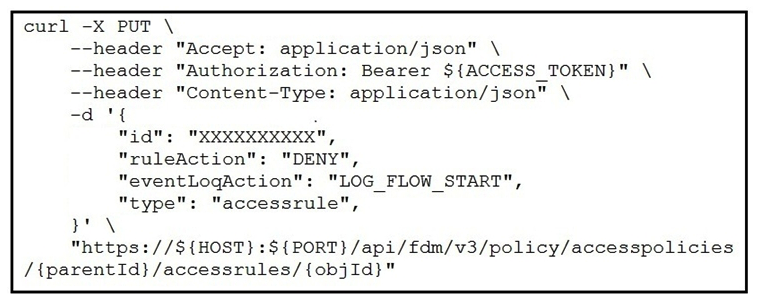 Refer to the exhibit. The security administrator must temporarily disallow traffic that goes to a production web server using the Cisco FDM REST API. The administrator sends an API query as shown in the exhibit. What is the outcome of that action?
Refer to the exhibit. The security administrator must temporarily disallow traffic that goes to a production web server using the Cisco FDM REST API. The administrator sends an API query as shown in the exhibit. What is the outcome of that action?
(Multiple Choice)
4.8/5  (42)
(42)
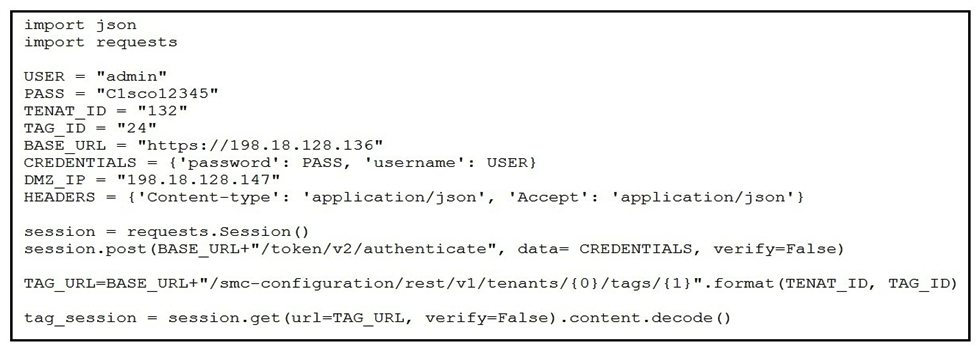 Refer to the exhibit. A network operator wants to add a certain IP to a DMZ tag. Which code segment completes the script and achieves the goal?
Refer to the exhibit. A network operator wants to add a certain IP to a DMZ tag. Which code segment completes the script and achieves the goal?
(Multiple Choice)
4.8/5  (38)
(38)
Which two destinations are supported by the Cisco Security Management Appliance reporting APIs? (Choose two.)
(Multiple Choice)
4.8/5  (37)
(37)
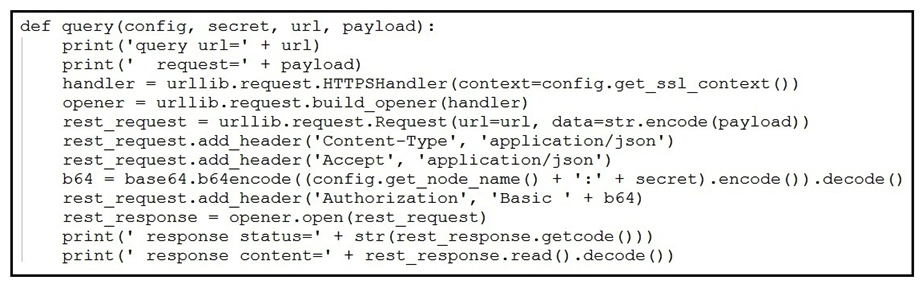 Refer to the exhibit. A Python function named "query" has been developed and the goal is to use it to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs. How is the function called, if the goal is to identify the sessions that are associated with the IP address 10.0.0.50?
Refer to the exhibit. A Python function named "query" has been developed and the goal is to use it to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs. How is the function called, if the goal is to identify the sessions that are associated with the IP address 10.0.0.50?
(Multiple Choice)
4.9/5  (34)
(34)
Showing 21 - 39 of 39
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)