Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
(Multiple Choice)
5.0/5  (31)
(31)
Which deployment model is the most secure when considering risks to cloud adoption?
(Multiple Choice)
4.8/5  (27)
(27)
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2?
(Multiple Choice)
4.8/5  (37)
(37)
Which benefit does endpoint security provide the overall security posture of an organization?
(Multiple Choice)
4.9/5  (34)
(34)
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
(Multiple Choice)
4.8/5  (40)
(40)
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the "Chat and Instant Messaging" category. Which reputation score should be selected to accomplish this goal?
(Multiple Choice)
4.8/5  (32)
(32)
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
(Multiple Choice)
4.8/5  (32)
(32)
An engineer has enabled LDAP accept queries on a listener. Malicious actors must be prevented from quickly identifying all valid recipients. What must be done on the Cisco ESA to accomplish this goal?
(Multiple Choice)
4.8/5  (32)
(32)
With which components does a southbound API within a software-defined network architecture communicate?
(Multiple Choice)
5.0/5  (44)
(44)
What provides visibility and awareness into what is currently occurring on the network?
(Multiple Choice)
4.9/5  (38)
(38)
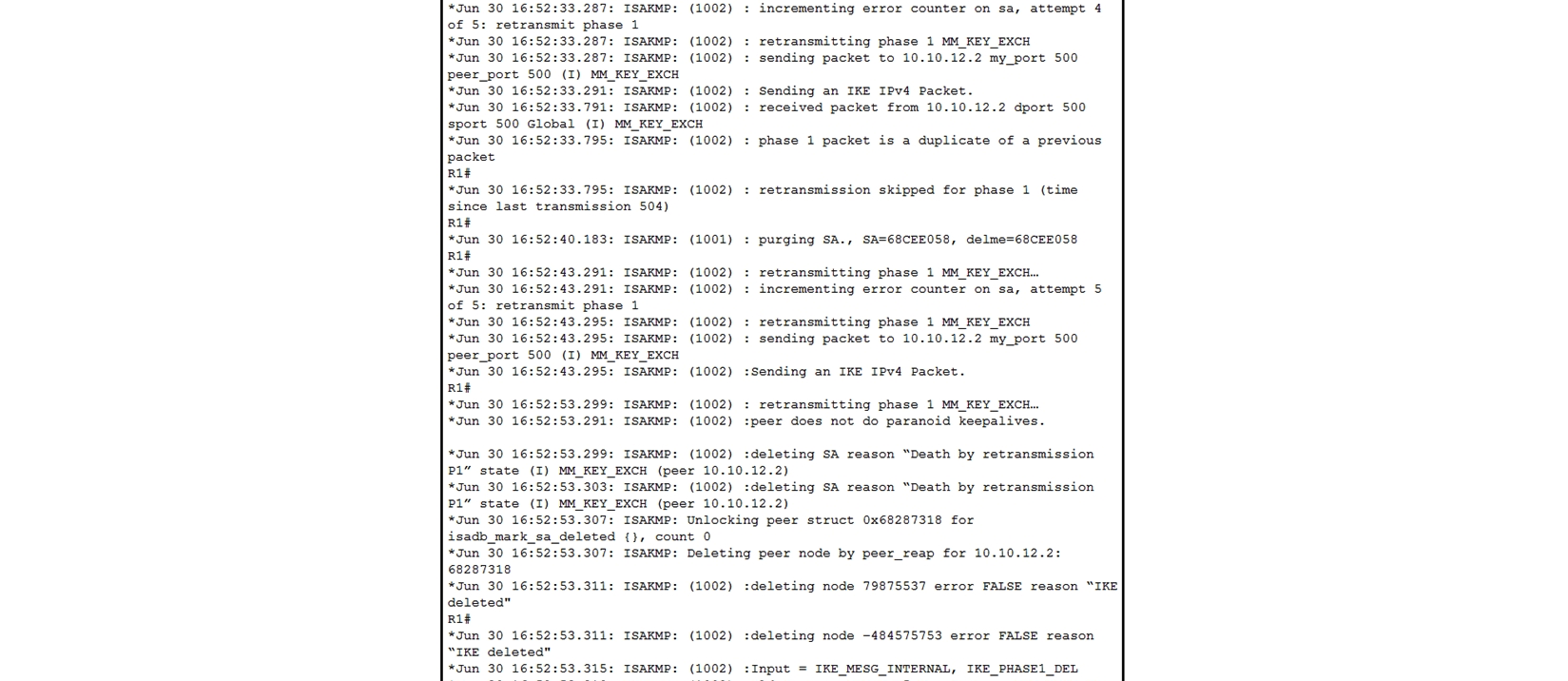 Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
(Multiple Choice)
4.8/5  (42)
(42)
A Cisco FirePower administrator needs to configure a rule to allow a new application that has never been seen on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose two.)
(Multiple Choice)
4.8/5  (43)
(43)
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
(Multiple Choice)
4.9/5  (32)
(32)
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network. What action will resolve this issue?
(Multiple Choice)
4.9/5  (33)
(33)
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
(Multiple Choice)
4.8/5  (34)
(34)
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the Interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
(Multiple Choice)
4.8/5  (22)
(22)
What must be used to share data between multiple security products?
(Multiple Choice)
4.8/5  (36)
(36)
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
(Multiple Choice)
4.9/5  (28)
(28)
What is a characteristic of Firepower NGIPS inline deployment mode?
(Multiple Choice)
4.9/5  (37)
(37)
Showing 161 - 180 of 213
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)