Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
(Multiple Choice)
4.8/5  (37)
(37)
An engineer detects an intrusion event inside an organization's network and becomes aware that files that contain personal data have been accessed. Which action must be taken to contain this attack?
(Multiple Choice)
4.9/5  (34)
(34)
Where do threat intelligence tools search for data to identify potential malicious IP addresses, domain names, and URLs?
(Multiple Choice)
4.9/5  (40)
(40)
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization's service area. What are the next steps the engineer must take?
(Multiple Choice)
4.8/5  (35)
(35)
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability. Which step was missed according to the NIST incident handling guide?
(Multiple Choice)
4.9/5  (44)
(44)
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks. Which standard must the architect apply?
(Multiple Choice)
4.9/5  (29)
(29)
An engineer is going through vulnerability triage with company management because of a recent malware outbreak from which 21 affected assets need to be patched or remediated. Management decides not to prioritize fixing the assets and accepts the vulnerabilities. What is the next step the engineer should take?
(Multiple Choice)
4.8/5  (33)
(33)
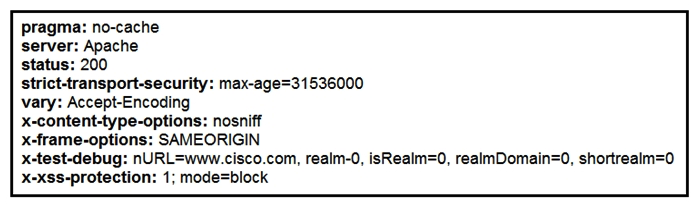 Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?
Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?
(Multiple Choice)
4.8/5  (25)
(25)
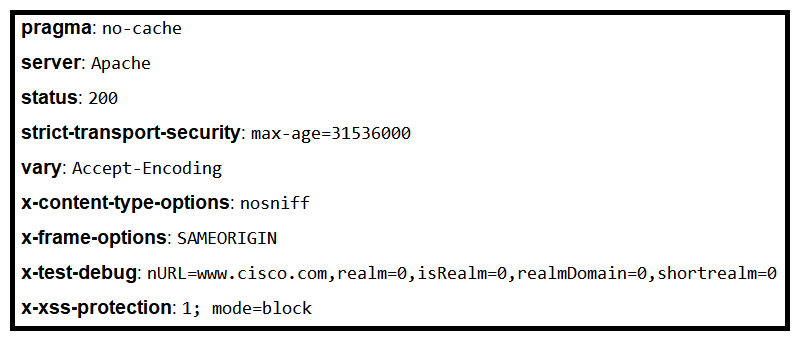 Refer to the exhibit. Where is the MIME type that should be followed indicated?
Refer to the exhibit. Where is the MIME type that should be followed indicated?
(Multiple Choice)
4.7/5  (38)
(38)
An organization had an incident with the network availability during which devices unexpectedly malfunctioned. An engineer is investigating the incident and found that the memory pool buffer usage reached a peak before the malfunction. Which action should the engineer take to prevent this issue from reoccurring?
(Multiple Choice)
4.7/5  (33)
(33)
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
(Multiple Choice)
4.9/5  (41)
(41)
A SOC engineer discovers that the organization had three DDOS attacks overnight. Four servers are reported offline, even though the hardware seems to be working as expected. One of the offline servers is affecting the pay system reporting times. Three employees, including executive management, have reported ransomware on their laptops. Which steps help the engineer understand a comprehensive overview of the incident?
(Multiple Choice)
4.9/5  (36)
(36)
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
(Multiple Choice)
4.8/5  (35)
(35)
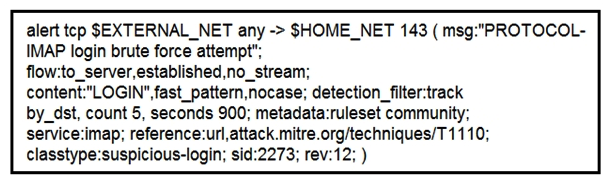 Refer to the exhibit. IDS is producing an increased amount of false positive events about brute force attempts on the organization's mail server. How should the Snort rule be modified to improve performance?
Refer to the exhibit. IDS is producing an increased amount of false positive events about brute force attempts on the organization's mail server. How should the Snort rule be modified to improve performance?
(Multiple Choice)
4.9/5  (35)
(35)
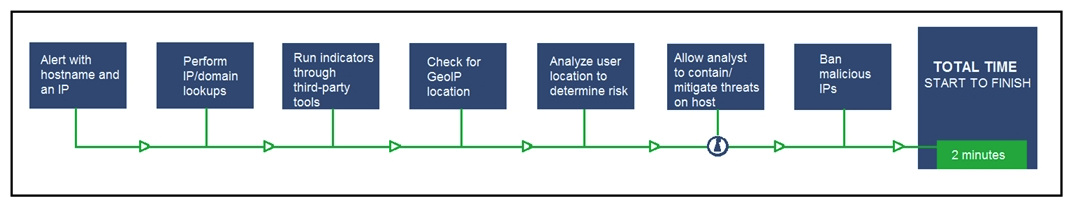 Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will accomplish this goal?
Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will accomplish this goal?
(Multiple Choice)
4.7/5  (39)
(39)
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server. Which security solution is needed at this stage to mitigate the attack?
(Multiple Choice)
4.8/5  (34)
(34)
An organization suffered a security breach in which the attacker exploited a Netlogon Remote Protocol vulnerability for further privilege escalation. Which two actions should the incident response team take to prevent this type of attack from reoccurring? (Choose two.)
(Multiple Choice)
4.7/5  (30)
(30)
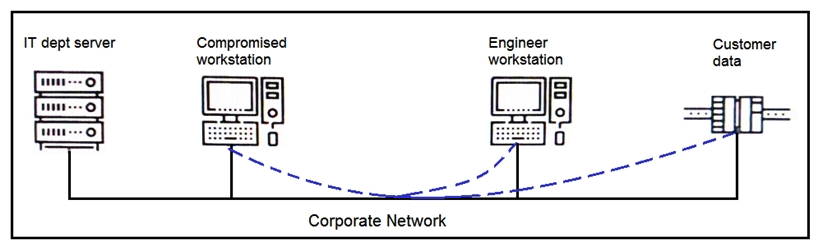 Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
(Multiple Choice)
4.8/5  (34)
(34)
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections with a possible attacker. Which tool should the analyst use to identify the source IP of the offender? 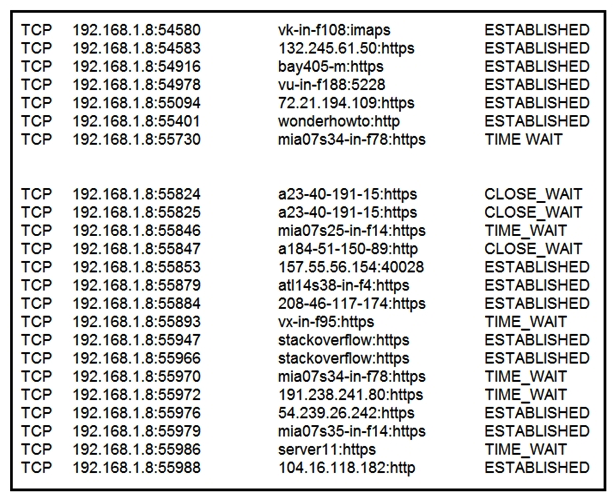
(Multiple Choice)
5.0/5  (38)
(38)
Showing 61 - 80 of 106
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)