Exam 40: Implementing and Operating Cisco Security Core Technologies
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
A customer reports Fibre Channel login requests to a Cisco MDS 9000 Series Switch from an unauthorized source. The customer requires a feature that will allow all devices already logged in and learned to be added to the Fibre Channel active database. Which two features must be enabled to accomplish this goal? (Choose two.)
(Multiple Choice)
4.9/5  (38)
(38)
Which behavior defines streaming telemetry as a push model in Cisco devices?
(Multiple Choice)
4.9/5  (34)
(34)
A network engineer repeatedly saves a configuration on Catalyst switches to NVRAM using the write memory command. Which action should be taken to implement the same action on Nexus switches?
(Multiple Choice)
4.8/5  (41)
(41)
An engineer is using REST API calls to configure the Cisco APIC. Which data structure must be used within a POST message to receive a login token?
(Multiple Choice)
4.8/5  (32)
(32)
An engineer configures an Intersight Virtual Appliance and must claim over 200 targets. The engineer starts the Claim New Target Procedure. The engineer has prepared this initial comma-separated value file to provision the targets: UCSFI,10.1.1.3,user-1,pwd5516b917 IMC,10.1.1.5/26,user-2,pwdc65b1c43f HX,10.1.2.1/30,user-3,pwd39913690 UCSD,1.1.1.1.user-4,pwd5003e9d5 Which information must be included in the comma-separated value file to provision the targets?
(Multiple Choice)
4.8/5  (38)
(38)
A network engineer must perform a backup and restore of the Cisco Nexus 5000 Series Switch configuration. The backup must be made to an external backup server. The only protocol permitted between the Cisco Nexus switch and the backup server is UDP. The backup must be used when the current working configuration of the switch gets corrupted. Which set of steps must be taken to meet these requirements?
(Multiple Choice)
4.8/5  (35)
(35)
An engineer is asked to use SaaS to manage Cisco computing. Which two items are needed to accomplish the task? (Choose two.)
(Multiple Choice)
4.8/5  (28)
(28)
Refer to the exhibit. 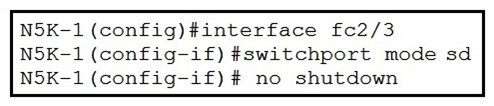 What is the result of implementing this configuration?
What is the result of implementing this configuration?
(Multiple Choice)
4.7/5  (40)
(40)
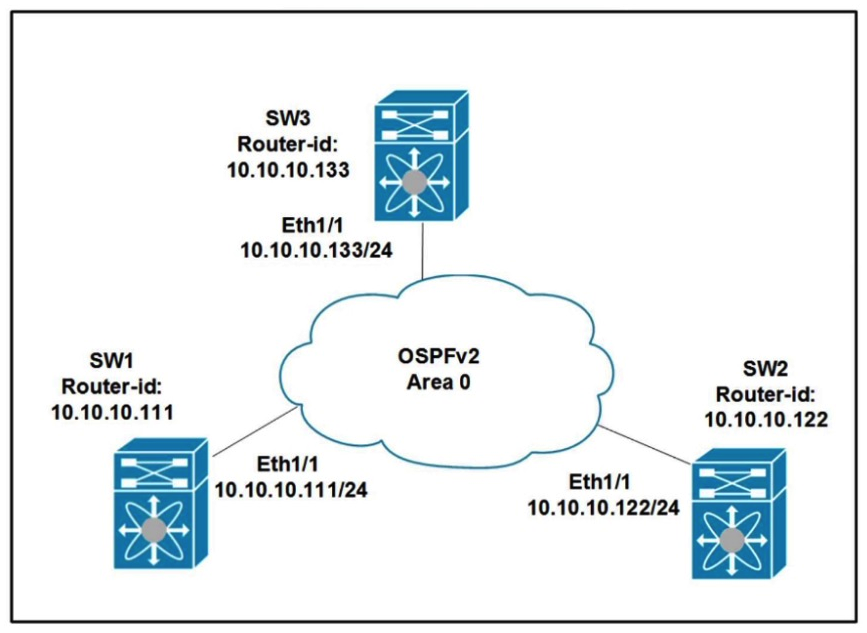 Refer to the exhibit. All switches are configured with the default OSPF priority. Which configuration should be applied to ensure that the SW2 Cisco Nexus switch controls the LSA floods and advertises the network to the remaining nodes in the OSPFv2 area?
Refer to the exhibit. All switches are configured with the default OSPF priority. Which configuration should be applied to ensure that the SW2 Cisco Nexus switch controls the LSA floods and advertises the network to the remaining nodes in the OSPFv2 area?
(Multiple Choice)
4.7/5  (31)
(31)
Refer to the exhibit.  What is the result of running the command presented?
What is the result of running the command presented?
(Multiple Choice)
4.9/5  (32)
(32)
Refer to the exhibit. 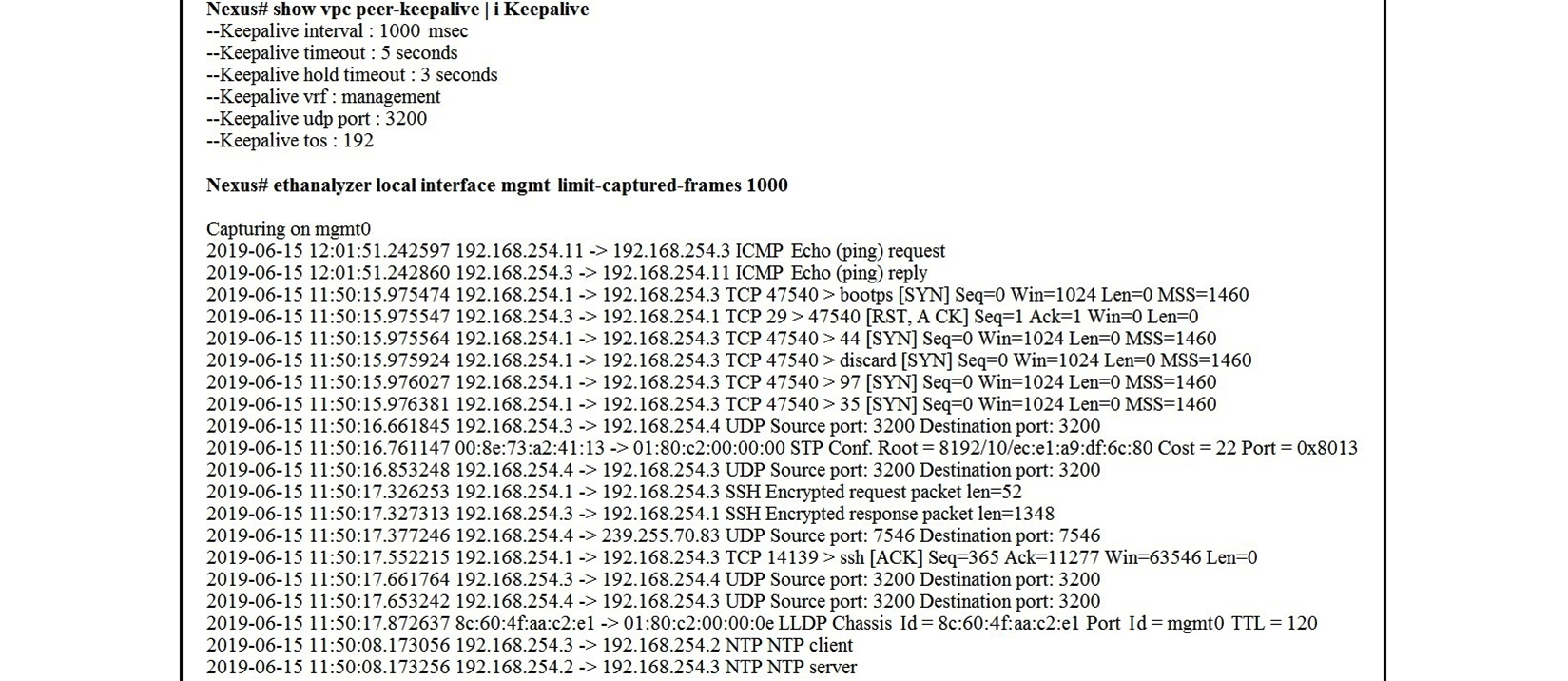 A flapping link issue has been reported on the vPC keepalive link. A packet capture has been activated on the Cisco Nexus switch. What is the destination IP address of the vPC keepalive packets that are sent by the switch?
A flapping link issue has been reported on the vPC keepalive link. A packet capture has been activated on the Cisco Nexus switch. What is the destination IP address of the vPC keepalive packets that are sent by the switch?
(Multiple Choice)
4.8/5  (42)
(42)
Where is the witness deployed in a two-node Cisco HyperFlex Edge deployment?
(Multiple Choice)
4.8/5  (28)
(28)
An engineer is configuring AAA authentication on a Cisco MDS 9000 Series switch. The LDAP server is located under the IP 10.10.2.2. The data sent to the LDAP server should be encrypted. Which command should be used to meet these requirements?
(Multiple Choice)
4.8/5  (31)
(31)
Port security is statically configured on a Cisco Nexus 7700 Series switch and F3 line card. The switch is configured with an Advanced Services license. Which two actions delete secured MAC addresses from the interface? (Choose two.)
(Multiple Choice)
4.9/5  (37)
(37)
Which statement about the impact of a rolling EPLD upgrade on a Cisco MDS 9000 Series Switch is true?
(Multiple Choice)
4.8/5  (37)
(37)
Refer to the exhibit. 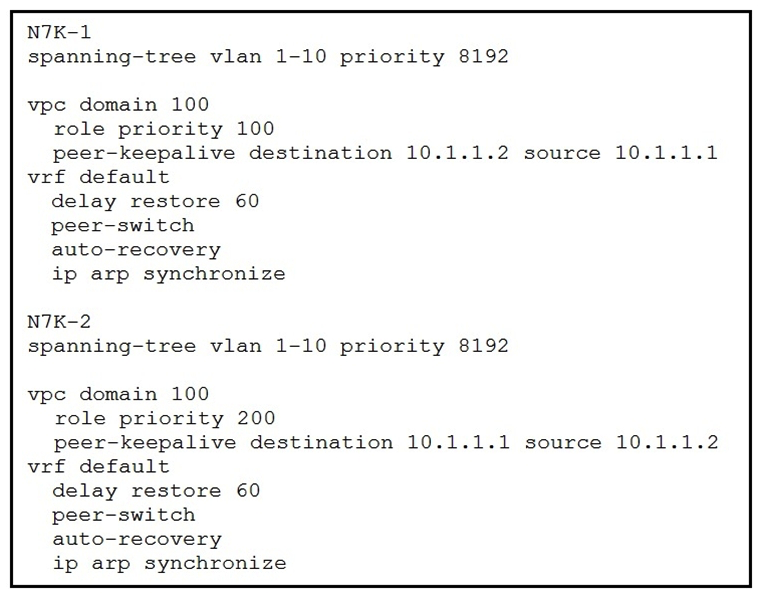 The STP priority of N7K-1 and N7K-2 are the lowest in the network. Which statement describes STP on the vPC?
The STP priority of N7K-1 and N7K-2 are the lowest in the network. Which statement describes STP on the vPC?
(Multiple Choice)
4.7/5  (33)
(33)
Which two components should be checked when a Cisco Nexus 9000 Series Switch fails to boot using POAP? (Choose two.)
(Multiple Choice)
4.9/5  (33)
(33)
An engineer needs to make an XML backup of Cisco UCS Manager. The backup should be transferred using an authenticated and encrypted tunnel, and it should contain all system and service profiles configuration. Which command must be implemented to meet these requirements?
(Multiple Choice)
4.9/5  (40)
(40)
A Cisco MDS 9000 Series Switch is configured for SAN Analytics and SAN Telemetry Streaming. An engineer must enable analytics for NVMe on interfaces in the range of fc1/1-12. Due to a large amount of traffic generated in the SAN environment, the data must be collected at regular intervals of 60 seconds from ports fc1/1-12 and then for ports fc1/13-24 for the next 60 seconds. Ports in the range fc1/13-24 were already enabled for analytics. Which set of commands must be used to meet these requirements?
(Multiple Choice)
4.9/5  (35)
(35)
An engineer need to implement a solution that prevents loops from occurring accidentally by connecting a switch to interface Ethernet1/1. The port is designated to be used for host connectivity. Which configuration should be implemented?
(Multiple Choice)
4.9/5  (29)
(29)
Showing 101 - 120 of 208
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)