Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Given the following: 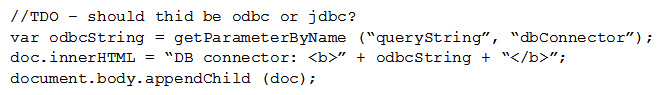 Which of the following vulnerabilities is present in the above code snippet?
Which of the following vulnerabilities is present in the above code snippet?
(Multiple Choice)
4.7/5  (31)
(31)
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot. 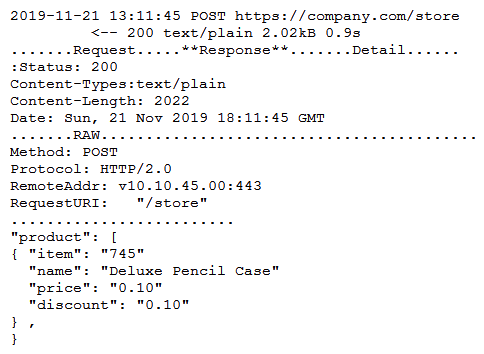 Which of the following tools was MOST likely used to exploit the application?
Which of the following tools was MOST likely used to exploit the application?
(Multiple Choice)
4.8/5  (35)
(35)
An internal penetration tester finds a legacy application that takes measurement input made in a text box and outputs a specific string of text related to industry requirements. There is no documentation about how this application works, and the source code has been lost. Which of the following would BEST allow the penetration tester to determine the input and output relationship?
(Multiple Choice)
4.8/5  (38)
(38)
To meet an SLA, which of the following document should be drafted, defining the company's internal interdependent unit responsibilities and delivery timelines.
(Multiple Choice)
4.8/5  (29)
(29)
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
(Multiple Choice)
4.8/5  (29)
(29)
Which of the following may indicate a configuration item has reached end-of-life?
(Multiple Choice)
4.9/5  (28)
(28)
A security architect has been assigned to a new digital transformation program. The objectives are to provide better capabilities to customers and reduce costs. The program has highlighted the following requirements: Long-lived sessions are required, as users do not log in very often. The solution has multiple SPs, which include mobile and web applications. A centralized IdP is utilized for all customer digital channels. The applications provide different functionality types such as forums and customer portals. The user experience needs to be the same across both mobile and web-based applications. Which of the following would BEST improve security while meeting these requirements?
(Multiple Choice)
4.9/5  (36)
(36)
A company is the victim of a phishing and spear-phishing campaign. Users are clicking on website links that look like common bank sites and entering their credentials accidentally. A security engineer decides to use a layered defense to prevent the phishing or lessen its impact. Which of the following should the security engineer implement? (Choose two.)
(Multiple Choice)
4.9/5  (39)
(39)
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system. Which of the following is MOST likely to be reviewed during the assessment? (Select two.)
(Multiple Choice)
4.8/5  (37)
(37)
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The assessor has been handed a package of definitions provided in XML format, and many of the files have two common tags within them: "<object object_ref=… />" and "<state state_ref=… />". Which of the following tools BEST supports the use of these definitions?
(Multiple Choice)
4.9/5  (36)
(36)
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices. 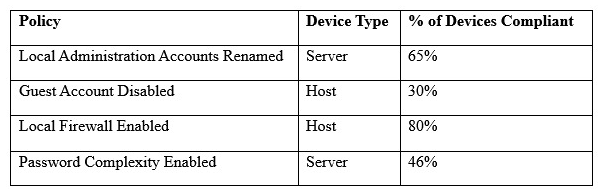 Which of the following tools is the security engineer using to produce the above output?
Which of the following tools is the security engineer using to produce the above output?
(Multiple Choice)
4.8/5  (34)
(34)
A security analyst who is concerned about sensitive data exfiltration reviews the following: 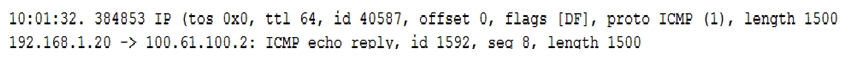 Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
(Multiple Choice)
4.7/5  (33)
(33)
During the decommissioning phase of a hardware project, a security administrator is tasked with ensuring no sensitive data is released inadvertently. All paper records are scheduled to be shredded in a crosscut shredder, and the waste will be burned. The system drives and removable media have been removed prior to e-cycling the hardware. Which of the following would ensure no data is recovered from the system drives once they are disposed of?
(Multiple Choice)
4.9/5  (27)
(27)
A product owner is reviewing the output of a web-application penetration test and has identified an application that is presenting sensitive information in cleartext on a page. Which of the following code snippets would be BEST to use to remediate the vulnerability?
(Multiple Choice)
4.9/5  (34)
(34)
A company is moving all of its web applications to an SSO configuration using SAML. Some employees report that when signing in to an application, they get an error message on the login screen after entering their username and password, and are denied access. When they access another system that has been converted to the new SSO authentication model, they are able to authenticate successfully without being prompted for login. Which of the following is MOST likely the issue?
(Multiple Choice)
4.7/5  (24)
(24)
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?
(Multiple Choice)
4.8/5  (30)
(30)
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiation, there are a number of outstanding issues, including: 1. Indemnity clauses have identified the maximum liability. 2. The data will be hosted and managed outside of the company's geographical location. The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant of the project, which of the following should the project's security consultant recommend as the NEXT step?
(Multiple Choice)
4.7/5  (33)
(33)
An organization has established the following controls matrix: 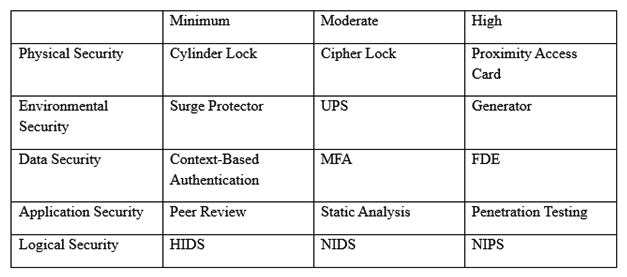 The following control sets have been defined by the organization and are applied in aggregate fashion: Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level. The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
The following control sets have been defined by the organization and are applied in aggregate fashion: Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level. The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
(Multiple Choice)
4.8/5  (35)
(35)
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues. Which of the following is the MOST important information to reference in the letter?
(Multiple Choice)
4.8/5  (24)
(24)
Given the following information about a company's internal network: User IP space: 192.168.1.0/24 Server IP space: 192.168.192.0/25 A security engineer has been told that there are rogue websites hosted outside of the proper server space, and those websites need to be identified. Which of the following should the engineer do?
(Multiple Choice)
4.8/5  (34)
(34)
Showing 421 - 440 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)