Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A large, multinational company currently has two separate databases. One is used for ERP, while the second is used for CRM. To consolidate services and infrastructure, it is proposed to combine the databases. The company's compliance manager is asked to review the proposal and is concerned about this integration. Which of the following would pose the MOST concern to the compliance manager?
(Multiple Choice)
4.8/5  (28)
(28)
An enterprise's Chief Technology Officer (CTO) and Chief Information Security Officer (CISO) are meeting to discuss ongoing capacity and resource planning issues. The enterprise has experienced rapid, massive growth over the last 12 months, and the technology department is stretched thin for resources. A new accounting service is required to support the enterprise's growth, but the only available compute resources that meet the accounting service requirements are on the virtual platform, which is hosting the enterprise's website. Which of the following should the CISO be MOST concerned about?
(Multiple Choice)
4.8/5  (31)
(31)
A security engineer is attempting to convey the importance of including job rotation in a company's standard security policies. Which of the following would be the BEST justification?
(Multiple Choice)
4.9/5  (35)
(35)
The Chief Information Security Officer (CISO) suspects that a database administrator has been tampering with financial data to the administrator's advantage. Which of the following would allow a third-party consultant to conduct an on-site review of the administrator's activity?
(Multiple Choice)
4.9/5  (30)
(30)
A corporate forensic investigator has been asked to acquire five forensic images of an employee database application. There are three images to capture in the United States, one in the United Kingdom, and one in Germany. Upon completing the work, the forensics investigator saves the images to a local workstation. Which of the following types of concerns should the forensic investigator have about this work assignment?
(Multiple Choice)
4.8/5  (32)
(32)
A company's Chief Operating Officer (COO) is concerned about the potential for competitors to infer proprietary information gathered from employees' social media accounts. Which of the following methods should the company use to gauge its own social media threat level without targeting individual employees?
(Multiple Choice)
4.8/5  (30)
(30)
An enterprise is trying to secure a specific web-based application by forcing the use of multifactor authentication. Currently, the enterprise cannot change the application's sign-in page to include an extra field. However, the web-based application supports SAML. Which of the following would BEST secure the application?
(Multiple Choice)
4.9/5  (29)
(29)
The Chief Information Security Officer (CISO) of an established security department, identifies a customer who has been using a fraudulent credit card. The CISO calls the local authorities, and when they arrive on-site, the authorities ask a security engineer to create a point-in-time copy of the running database in their presence. This is an example of:
(Multiple Choice)
4.8/5  (35)
(35)
A company wants to perform analysis of a tool that is suspected to contain a malicious payload. A forensic analyst is given the following snippet: ^32^[34fda19(fd^43gfd/home / user/lib/module.so.343jk^rfw(342fds43g Which of the following did the analyst use to determine the location of the malicious payload?
(Multiple Choice)
4.7/5  (37)
(37)
A security engineer is working with a software development team. The engineer is tasked with ensuring all security requirements are adhered to by the developers. Which of the following BEST describes the contents of the supporting document the engineer is creating?
(Multiple Choice)
4.8/5  (24)
(24)
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet: 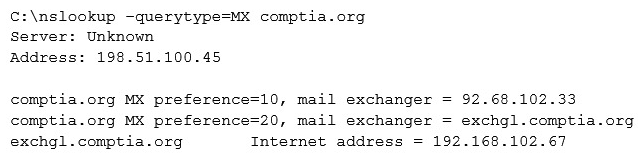 Which of the following should the penetration tester conclude about the command output?
Which of the following should the penetration tester conclude about the command output?
(Multiple Choice)
4.9/5  (38)
(38)
A security engineer discovers a PC may have been breached and accessed by an outside agent. The engineer wants to find out how this breach occurred before remediating the damage. Which of the following should the security engineer do FIRST to begin this investigation?
(Multiple Choice)
4.9/5  (40)
(40)
A Chief Security Officer (CSO) is reviewing the organization's incident response report from a recent incident. The details of the event indicate: A user received a phishing email that appeared to be a report from the organization's CRM tool. The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool. The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials. Several weeks later, the user reported anomalous activity within the CRM tool. Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool. Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO. Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
(Multiple Choice)
4.9/5  (36)
(36)
A security engineer is employed by a hospital that was recently purchased by a corporation. Throughout the acquisition process, all data on the virtualized file servers must be shared by departments within both organizations. The security engineer considers data ownership to determine:
(Multiple Choice)
4.9/5  (41)
(41)
Given the code snippet below: 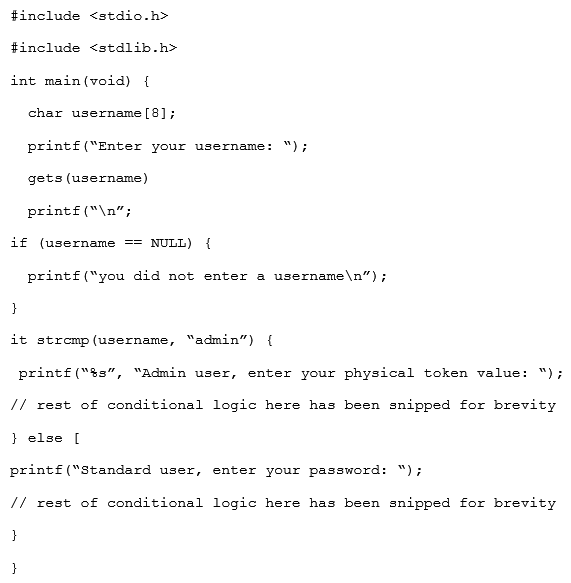 Which of the following vulnerability types in the MOST concerning?
Which of the following vulnerability types in the MOST concerning?
(Multiple Choice)
4.8/5  (35)
(35)
An information security manager is concerned that connectivity used to configure and troubleshoot critical network devices could be attacked. The manager has tasked a network security engineer with meeting the following requirements: Encrypt all traffic between the network engineer and critical devices. Segregate the different networking planes as much as possible. Do not let access ports impact configuration tasks. Which of the following would be the BEST recommendation for the network security engineer to present?
(Multiple Choice)
4.8/5  (29)
(29)
As part of the asset management life cycle, a company engages a certified equipment disposal vendor to appropriately recycle and destroy company assets that are no longer in use. As part of the company's vendor due diligence, which of the following would be MOST important to obtain from the vendor?
(Multiple Choice)
4.8/5  (34)
(34)
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages: 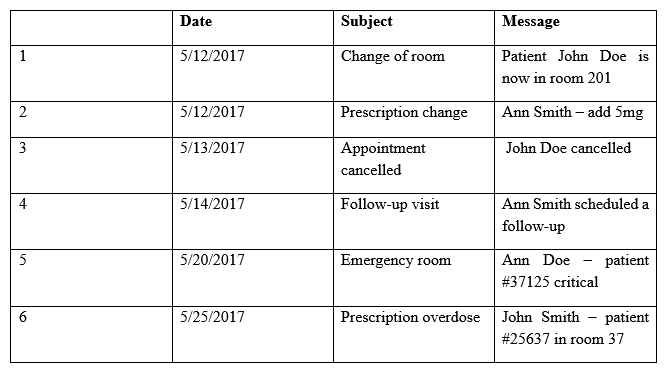 Which of the following represents the BEST solution for preventing future fines?
Which of the following represents the BEST solution for preventing future fines?
(Multiple Choice)
4.8/5  (33)
(33)
A company has created a policy to allow employees to use their personally owned devices. The Chief Information Officer (CISO) is getting reports of company data appearing on unapproved forums and an increase in theft of personal electronic devices. Which of the following security controls would BEST reduce the risk of exposure?
(Multiple Choice)
4.8/5  (28)
(28)
A company uses an application in its warehouse that works with several commercially available tablets and can only be accessed inside the warehouse. The support department would like the selection of tablets to be limited to three models to provide better support and ensure spares are on hand. Users often keep the tablets after they leave the department, as many of them store personal media items. Which of the following should the security engineer recommend to meet these requirements?
(Multiple Choice)
5.0/5  (38)
(38)
Showing 201 - 220 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)