Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Ann, a retiring employee, cleaned out her desk. The next day, Ann's manager notices company equipment that was supposed to remain at her desk is now missing. Which of the following would reduce the risk of this occurring in the future?
(Multiple Choice)
4.8/5  (36)
(36)
A Chief Information Security Officer (CISO) is creating a security committee involving multiple business units of the corporation. Which of the following is the BEST justification to ensure collaboration across business units?
(Multiple Choice)
5.0/5  (41)
(41)
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website. 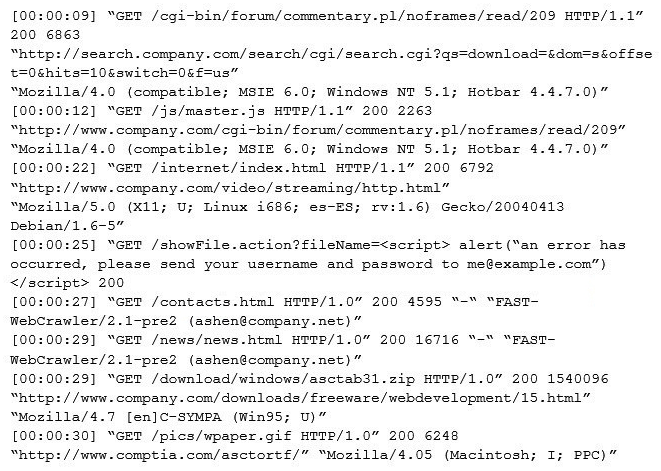 Which of the following types of attack vectors did the penetration tester use?
Which of the following types of attack vectors did the penetration tester use?
(Multiple Choice)
4.7/5  (28)
(28)
Following a merger, the number of remote sites for a company has doubled to 52. The company has decided to secure each remote site with an NGFW to provide web filtering, NIDS/NIPS, and network antivirus. The Chief Information Officer (CIO) has requested that the security engineer provide recommendations on sizing for the firewall with the requirements that it be easy to manage and provide capacity for growth. The tables below provide information on a subset of remote sites and the firewall options: 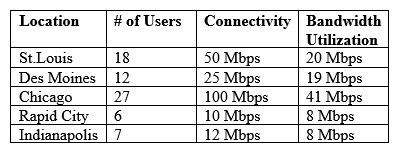
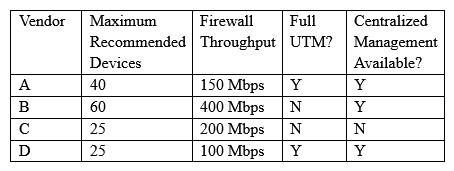 Which of the following would be the BEST option to recommend to the CIO?
Which of the following would be the BEST option to recommend to the CIO?
(Multiple Choice)
4.7/5  (32)
(32)
A technician is validating compliance with organizational policies. The user and machine accounts in the AD are not set to expire, which is non-compliant. Which of the following network tools would provide this type of information?
(Multiple Choice)
4.9/5  (34)
(34)
A security architect has been assigned to a new digital transformation program. The objectives are to provide better capabilities to customers and reduce costs. The program has highlighted the following requirements: Long-lived sessions are required, as users do not log in very often. The solution has multiple SPs, which include mobile and web applications. A centralized IdP is utilized for all customer digital channels. The applications provide different functionality types such as forums and customer portals. The user experience needs to be the same across both mobile and web-based applications. Which of the following would BEST improve security while meeting these requirements?
(Multiple Choice)
4.9/5  (41)
(41)
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured. 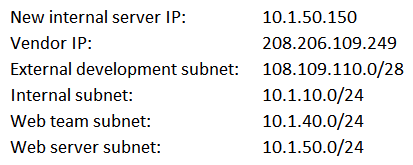 Below is a snippet from the firewall related to that server (access is provided in a top-down model):
Below is a snippet from the firewall related to that server (access is provided in a top-down model): 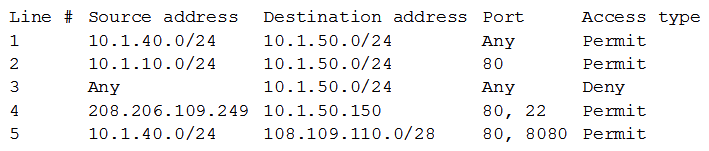 Which of the following lines should be configured to allow the proper access? (Choose two.)
Which of the following lines should be configured to allow the proper access? (Choose two.)
(Multiple Choice)
4.7/5  (33)
(33)
Following a recent outage, a systems administrator is conducting a study to determine a suitable bench stock on server hard drives. Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep-on hand?
(Multiple Choice)
4.8/5  (35)
(35)
A company uses an enterprise desktop imaging solution to manage deployment of its desktop computers. Desktop computer users are only permitted to use software that is part of the baseline image. Which of the following technical solutions was MOST likely deployed by the company to ensure only known-good software can be installed on corporate desktops?
(Multiple Choice)
4.9/5  (45)
(45)
An international e-commerce company has identified attack traffic originating from a whitelisted third party's IP address used to mask the third party's internal network. The security team needs to block the attack traffic without impacting the vendor's services. Which of the following is the BEST approach to identify the threat?
(Multiple Choice)
4.8/5  (33)
(33)
While attending a meeting with the human resources department, an organization's information security officer sees an employee using a username and password written on a memo pad to log into a specific service. When the information security officer inquires further as to why passwords are being written down, the response is that there are too many passwords to remember for all the different services the human resources department is required to use. Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
(Multiple Choice)
4.9/5  (38)
(38)
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below: 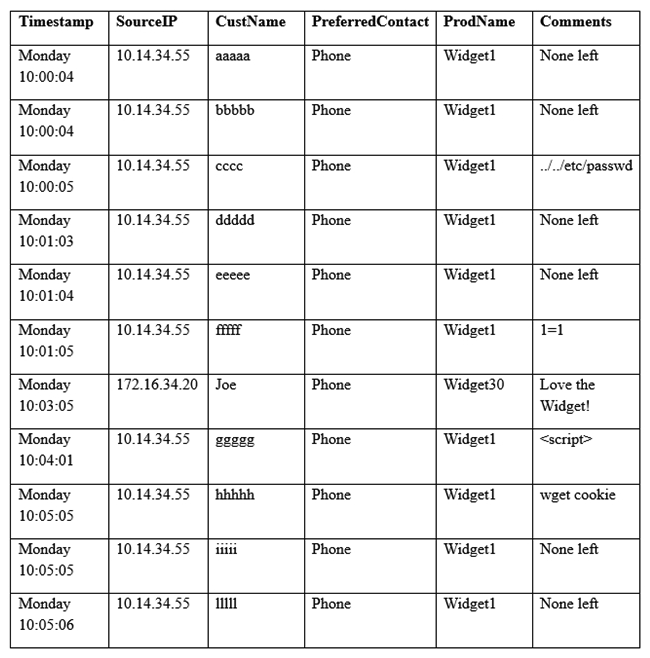 Which of the following is the MOST likely type of activity occurring?
Which of the following is the MOST likely type of activity occurring?
(Multiple Choice)
4.8/5  (35)
(35)
A deployment manager is working with a software development group to assess the security of a new version of the organization's internally developed ERP tool. The organization prefers to not perform assessment activities following deployment, instead focusing on assessing security throughout the life cycle. Which of the following methods would BEST assess the security of the product?
(Multiple Choice)
4.8/5  (31)
(31)
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
(Multiple Choice)
4.8/5  (38)
(38)
A team is at the beginning stages of designing a new enterprise-wide application. The new application will have a large database and require a capital investment in hardware. The Chief Information Officer (?IO) has directed the team to save money and reduce the reliance on the datacenter, and the vendor must specialize in hosting large databases in the cloud. Which of the following cloud-hosting options would BEST meet these needs?
(Multiple Choice)
4.9/5  (42)
(42)
Several recent ransomware outbreaks at a company have cost a significant amount of lost revenue. The security team needs to find a technical control mechanism that will meet the following requirements and aid in preventing these outbreaks: Stop malicious software that does not match a signature Report on instances of suspicious behavior Protect from previously unknown threats Augment existing security capabilities Which of the following tools would BEST meet these requirements?
(Multiple Choice)
4.9/5  (28)
(28)
The audit team was only provided the physical and logical addresses of the network without any type of access credentials. Which of the following methods should the audit team use to gain initial access during the security assessment? (Choose two.)
(Multiple Choice)
4.7/5  (30)
(30)
A network administrator is concerned about a particular server that is attacked occasionally from hosts on the Internet. The server is not critical; however, the attacks impact the rest of the network. While the company's current ISP is cost effective, the ISP is slow to respond to reported issues. The administrator needs to be able to mitigate the effects of an attack immediately without opening a trouble ticket with the ISP. The ISP is willing to accept a very small network route advertised with a particular BGP community string. Which of the following is the BEST way for the administrator to mitigate the effects of these attacks?
(Multiple Choice)
4.7/5  (32)
(32)
A Chief Information Security Officer (CISO) is working with a consultant to perform a gap assessment prior to an upcoming audit. It is determined during the assessment that the organization lacks controls to effectively assess regulatory compliance by third-party service providers. Which of the following should be revised to address this gap?
(Multiple Choice)
5.0/5  (40)
(40)
An engineer is assisting with the design of a new virtualized environment that will house critical company services and reduce the datacenter's physical footprint. The company has expressed concern about the integrity of operating systems and wants to ensure a vulnerability exploited in one datacenter segment would not lead to the compromise of all others. Which of the following design objectives should the engineer complete to BEST mitigate the company's concerns? (Choose two.)
(Multiple Choice)
4.8/5  (33)
(33)
Showing 181 - 200 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)