Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A consulting firm was hired to conduct assessment for a company. During the first stage, a penetration tester used a tool that provided the following output: TCP 80 open TCP 443 open TCP 1434 filtered The penetration tester then used a different tool to make the following requests: GET / script/login.php?token=45$MHT000MND876 GET / script/login.php?token=@#984DCSPQ%091DF Which of the following tools did the penetration tester use?
(Multiple Choice)
4.8/5  (27)
(27)
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review: Which of the following tools is the engineer utilizing to perform this assessment? 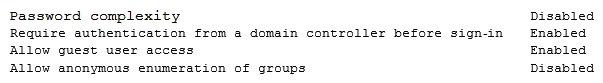
(Multiple Choice)
4.8/5  (27)
(27)
A security engineer has implemented an internal user access review tool so service teams can baseline user accounts and group memberships. The tool is functional and popular among its initial set of onboarded teams. However, the tool has not been built to cater to a broader set of internal teams yet. The engineer has sought feedback from internal stakeholders, and a list of summarized requirements is as follows: The tool needs to be responsive so service teams can query it, and then perform an automated response action. The tool needs to be resilient to outages so service teams can perform the user access review at any point in time and meet their own SLAs. The tool will become the system-of-record for approval, reapproval, and removal life cycles of group memberships and must allow for data retrieval after failure. Which of the following need specific attention to meet the requirements listed above? (Choose three.)
(Multiple Choice)
4.8/5  (27)
(27)
The legal department has required that all traffic to and from a company's cloud-based word processing and email system is logged. To meet this requirement, the Chief Information Security Officer (CISO) has implemented a next-generation firewall to perform inspection of the secure traffic and has decided to use a cloud-based log aggregation solution for all traffic that is logged. Which of the following presents a long-term risk to user privacy in this scenario?
(Multiple Choice)
4.9/5  (39)
(39)
An engineer is reviewing the security architecture for an enterprise network. During the review, the engineer notices an undocumented node on the network. Which of the following approaches can be utilized to determine how this node operates? (Choose two.)
(Multiple Choice)
4.9/5  (33)
(33)
A company's user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem. Which of the following solutions would BEST support trustworthy communication solutions?
(Multiple Choice)
4.9/5  (39)
(39)
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network. 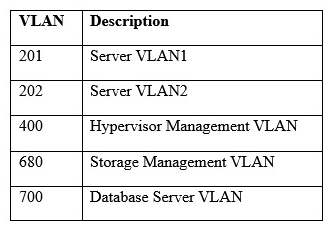 Using the above information, on which VLANs should multicast be enabled?
Using the above information, on which VLANs should multicast be enabled?
(Multiple Choice)
4.7/5  (31)
(31)
A newly hired security analyst has joined an established SOC team. Not long after going through corporate orientation, a new attack method on web-based applications was publicly revealed. The security analyst immediately brings this new information to the team lead, but the team lead is not concerned about it. Which of the following is the MOST likely reason for the team lead's position?
(Multiple Choice)
5.0/5  (35)
(35)
A company wants to extend its help desk availability beyond business hours. The Chief Information Officer (CIO) decides to augment the help desk with a third-party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance. The security administrator implements the following firewall change: 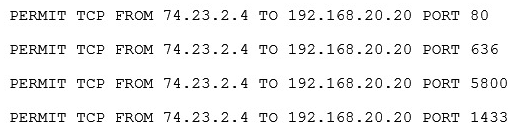 The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
(Multiple Choice)
4.8/5  (29)
(29)
A project manager is working with system owners to develop maintenance windows for system patching and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
(Multiple Choice)
4.7/5  (35)
(35)
After several industry comnpetitors suffered data loss as a result of cyebrattacks, the Chief Operating Officer (COO) of a company reached out to the information security manager to review the organization's security stance. As a result of the discussion, the COO wants the organization to meet the following criteria: Blocking of suspicious websites Prevention of attacks based on threat intelligence Reduction in spam Identity-based reporting to meet regulatory compliance Prevention of viruses based on signature Protect applications from web-based threats Which of the following would be the BEST recommendation the information security manager could make?
(Multiple Choice)
4.8/5  (44)
(44)
As a result of an acquisition, a new development team is being integrated into the company. The development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize SaaS. To have the team up and running effectively, a separate Internet connection has been procured. A stand up has identified the following additional requirements: 1. Reuse of the existing network infrastructure 2. Acceptable use policies to be enforced 3. Protection of sensitive files 4. Access to the corporate applications Which of the following solution components should be deployed to BEST meet the requirements? (Choose three.)
(Multiple Choice)
4.9/5  (32)
(32)
A security engineer is deploying an IdP to broker authentication between applications. These applications all utilize SAML 2.0 for authentication. Users log into the IdP with their credentials and are given a list of applications they may access. One of the application's authentications is not functional when a user initiates an authentication attempt from the IdP. The engineer modifies the configuration so users browse to the application first, which corrects the issue. Which of the following BEST describes the root cause?
(Multiple Choice)
4.9/5  (35)
(35)
An organization based in the United States is planning to expand its operations into the European market later in the year. Legal counsel is exploring the additional requirements that must be established as a result of the expansion. The BEST course of action would be to:
(Multiple Choice)
4.7/5  (31)
(31)
While an employee is on vacation, suspicion arises that the employee has been involved in malicious activity on the network. The security engineer is concerned the investigation may need to continue after the employee returns to work. Given this concern, which of the following should the security engineer recommend to maintain the integrity of the investigation?
(Multiple Choice)
4.8/5  (33)
(33)
A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router: 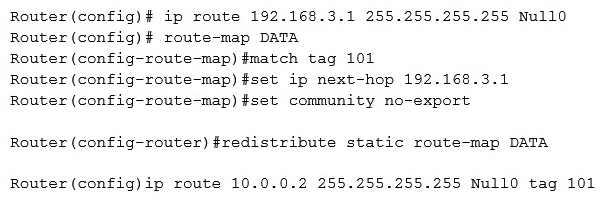 Which of the following is the engineer implementing?
Which of the following is the engineer implementing?
(Multiple Choice)
4.9/5  (25)
(25)
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix. Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Choose two.)
(Multiple Choice)
4.9/5  (32)
(32)
A Chief Information Security Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used: 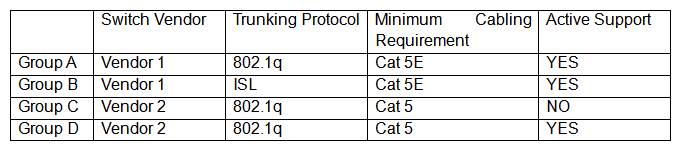 Which of the following would be the CISO's MOST immediate concern?
Which of the following would be the CISO's MOST immediate concern?
(Multiple Choice)
4.9/5  (32)
(32)
Following a recent network intrusion, a company wants to determine the current security awareness of all of its employees. Which of the following is the BEST way to test awareness?
(Multiple Choice)
4.9/5  (31)
(31)
An organization, which handles large volumes of PII, allows mobile devices that can process, store, and transmit PII and other sensitive data to be issued to employees. Security assessors can demonstrate recovery and decryption of remnant sensitive data from device storage after MDM issues a successful wipe command. Assuming availability of the controls, which of the following would BEST protect against the loss of sensitive data in the future?
(Multiple Choice)
4.7/5  (29)
(29)
Showing 241 - 260 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)