Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A network service on a production system keeps crashing at random times. The systems administrator suspects a bug in the listener is causing the service to crash, resulting in a DoS. When the service crashes, a core dump is left in the /tmp directory. Which of the following tools can the systems administrator use to reproduce these symptoms?
(Multiple Choice)
4.7/5  (40)
(40)
Given the following code snippet: 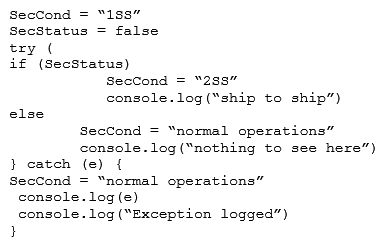 Which of the following failure modes would the code exhibit?
Which of the following failure modes would the code exhibit?
(Multiple Choice)
4.8/5  (36)
(36)
After multiple service interruptions caused by an older datacenter design, a company decided to migrate away from its datacenter. The company has successfully completed the migration of all datacenter servers and services to a cloud provider. The migration project includes the following phases: Selection of a cloud provider Architectural design Microservice segmentation Virtual private cloud Geographic service redundancy Service migration The Chief Information Security Officer (CISO) is still concerned with the availability requirements of critical company applications. Which of the following should the company implement NEXT?
(Multiple Choice)
4.7/5  (43)
(43)
A security administrator is concerned about the increasing number of users who click on malicious links contained within phishing emails. Although the company has implemented a process to block these links at the network perimeter, many accounts are still becoming compromised. Which of the following should be implemented for further reduce the number of account compromises caused by remote users who click these links?
(Multiple Choice)
4.8/5  (27)
(27)
A large, public university has recently been experiencing an increase in ransomware attacks against computers connected to its network. Security engineers have discovered various staff members receiving seemingly innocuous files in their email that are being run. Which of the following would BEST mitigate this attack method?
(Multiple Choice)
4.9/5  (40)
(40)
The government is concerned with remote military missions being negatively being impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following: End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families. Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications A host-based whitelist of approved websites and applications that only allow mission-related tools and sites The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
(Multiple Choice)
4.8/5  (32)
(32)
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses "Number of successful phishing attacks" as a KRI, but it does not show an increase. Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
(Multiple Choice)
4.9/5  (35)
(35)
While investigating suspicious activity on a server, a security administrator runs the following report: 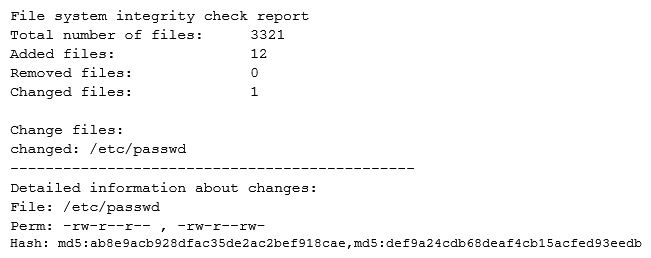 In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
(Multiple Choice)
4.8/5  (28)
(28)
A new database application was added to a company's hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company's cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data. Which of the following should the security team do to help mitigate future attacks within the VM environment? (Choose two.)
(Multiple Choice)
4.8/5  (36)
(36)
A security administrator adding a NAC requirement for all VPN users to ensure the connecting devices are compliant with company policy. Which of the following items provides the HIGHEST assurance to meet this requirement?
(Multiple Choice)
4.8/5  (45)
(45)
A security administrator is troubleshooting RADIUS authentication issues from a newly implemented controller-based wireless deployment. The RADIUS server contains the following information in its logs: 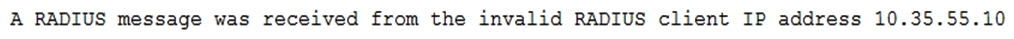 Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:
Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:  To correct this error message, the administrator makes an additional change to the RADIUS server. Which of the following did the administrator reconfigure on the RADIUS server? (Choose two.)
To correct this error message, the administrator makes an additional change to the RADIUS server. Which of the following did the administrator reconfigure on the RADIUS server? (Choose two.)
(Multiple Choice)
4.9/5  (39)
(39)
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS. Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
(Multiple Choice)
4.8/5  (35)
(35)
A hospital is using a functional magnetic resonance imaging (fMRI) scanner, which is controlled by a legacy desktop connected to the network. The manufacturer of the fMRI will not support patching of the legacy system. The legacy desktop needs to be network accessible on TCP port 445. A security administrator is concerned the legacy system will be vulnerable to exploits. Which of the following would be the BEST strategy to reduce the risk of an outage while still providing for security?
(Multiple Choice)
4.8/5  (35)
(35)
Several days after deploying an MDM for smartphone control, an organization began noticing anomalous behavior across the enterprise. Security analysts observed the following: Unauthorized certificate issuance Access to mutually authenticated resources utilizing valid but unauthorized certificates Granted access to internal resources via the SSL VPN To address the immediate problem, security analysts revoked the erroneous certificates. Which of the following describes the MOST likely root cause of the problem and offers a solution?
(Multiple Choice)
4.9/5  (30)
(30)
A security engineer is attempting to increase the randomness of numbers used in key generation in a system. The goal of the effort is to strengthen the keys against predictive analysis attacks. Which of the following is the BEST solution?
(Multiple Choice)
4.9/5  (31)
(31)
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
(Multiple Choice)
4.8/5  (29)
(29)
Which of the following attacks can be used to exploit a vulnerability that was created by untrained users?
(Multiple Choice)
4.7/5  (29)
(29)
A manufacturing company's security engineer is concerned a remote actor may be able to access the ICS that is used to monitor the factory lines. The security engineer recently proposed some techniques to reduce the attack surface of the ICS to the Chief Information Security Officer (CISO). Which of the following would BEST track the reductions to show the CISO the engineer's plan is successful during each phase?
(Multiple Choice)
5.0/5  (27)
(27)
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements: Support server, laptop, and desktop infrastructure Due to limited security resources, implement active protection capabilities Provide users with the ability to self-service classify information and apply policies Protect data-at-rest and data-in-use Which of the following endpoint capabilities would BEST meet the above requirements? (Select two.)
(Multiple Choice)
4.8/5  (41)
(41)
A security administrator wants to allow external organizations to cryptographically validate the company's domain name in email messages sent by employees. Which of the following should the security administrator implement?
(Multiple Choice)
4.9/5  (38)
(38)
Showing 341 - 360 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)