Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
After an employee was terminated, the company discovered the employee still had access to emails and attached content that should have been destroyed during the off-boarding. The employee's laptop and cell phone were confiscated and accounts were disabled promptly. Forensic investigation suggests the company's DLP was effective, and the content in question was not sent outside of work or transferred to removable media. Personality owned devices are not permitted to access company systems or information. Which of the following would be the MOST efficient control to prevent this from occurring in the future?
(Multiple Choice)
4.9/5  (40)
(40)
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization's existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:
(Multiple Choice)
4.9/5  (38)
(38)
A government entity is developing requirements for an RFP to acquire a biometric authentication system. When developing these requirements, which of the following considerations is MOST critical to the verification and validation of the SRTM?
(Multiple Choice)
4.9/5  (35)
(35)
An administrator has noticed mobile devices from an adjacent company on the corporate wireless network. Malicious activity is being reported from those devices. To add another layer of security in an enterprise environment, an administrator wants to add contextual authentication to allow users to access enterprise resources only while present in corporate buildings. Which of the following technologies would accomplish this?
(Multiple Choice)
4.7/5  (36)
(36)
A company recently experienced a security incident in which its domain controllers were the target of a DoS attack. In which of the following steps should technicians connect domain controllers to the network and begin authenticating users again?
(Multiple Choice)
4.8/5  (36)
(36)
One of the objectives of a bank is to instill a security awareness culture. Which of the following are techniques that could help to achieve this? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
Following the successful response to a data-leakage incident, the incident team lead facilitates an exercise that focuses on continuous improvement of the organization's incident response capabilities. Which of the following activities has the incident team lead executed?
(Multiple Choice)
4.9/5  (40)
(40)
Ann, a security manager, is reviewing a threat feed that provides information about attacks that allow a malicious user to gain access to private contact lists. Ann receives a notification that the vulnerability can be exploited within her environment. Given this information, Ann can anticipate an increase in:
(Multiple Choice)
4.8/5  (34)
(34)
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization's systems to the greatest extent possible. Which of the following principles is being demonstrated?
(Multiple Choice)
4.8/5  (32)
(32)
A security engineer has been hired to design a device that will enable the exfiltration of data from within a well-defended network perimeter during an authorized test. The device must bypass all firewalls and NIDS in place, as well as allow for the upload of commands from a centralized command and control server . The total cost of the device must be kept to a minimum in case the device is discovered during an assessment. Which of the following tools should the engineer load onto the device being designed?
(Multiple Choice)
4.8/5  (35)
(35)
A large company with a very complex IT environment is considering a move from an on-premises, internally managed proxy to a cloud-based proxy solution managed by an external vendor. The current proxy provides caching, content filtering, malware analysis, and URL categorization for all staff connected behind the proxy. Staff members connect directly to the Internet outside of the corporate network. The cloud-based version of the solution would provide content filtering, TLS decryption, malware analysis, and URL categorization. After migrating to the cloud solution, all internal proxies would be decommissioned. Which of the following would MOST likely change the company's risk profile?
(Multiple Choice)
4.7/5  (37)
(37)
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website. 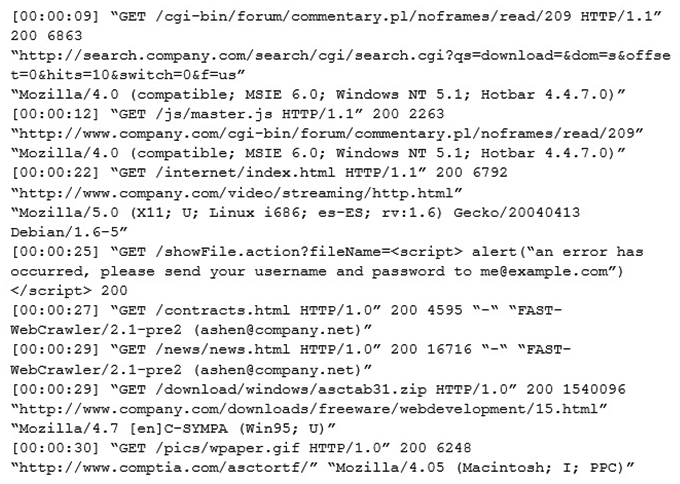 Which of the following types of attack vector did the penetration tester use?
Which of the following types of attack vector did the penetration tester use?
(Multiple Choice)
4.9/5  (31)
(31)
A network printer needs Internet access to function. Corporate policy states all devices allowed on the network must be authenticated. Which of the following is the MOST secure method to allow the printer on the network without violating policy?
(Multiple Choice)
4.8/5  (40)
(40)
The board of a financial services company has requested that the senior security analyst acts as a cybersecurity advisor in order to comply with recent federal legislation. The analyst is required to give a report on current cybersecurity and threat trends in the financial services industry at the next board meeting. Which of the following would be the BEST methods to prepare this report? (Choose two.)
(Multiple Choice)
4.9/5  (28)
(28)
A security analyst is attempting to break into a client's secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst's NEXT step is to perform:
(Multiple Choice)
4.9/5  (32)
(32)
Two competing companies experienced similar attacks on their networks from various threat actors. To improve response times, the companies wish to share some threat intelligence about the sources and methods of attack. Which of the following business documents would be BEST to document this engagement?
(Multiple Choice)
4.9/5  (31)
(31)
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs, the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
(Multiple Choice)
4.8/5  (32)
(32)
Users have reported that an internally developed web application is acting erratically, and the response output is inconsistent. The issue began after a web application dependency patch was applied to improve security. Which of the following would be the MOST appropriate tool to help identify the issue?
(Multiple Choice)
4.9/5  (37)
(37)
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
(Multiple Choice)
4.9/5  (27)
(27)
A recent security assessment revealed a web application may be vulnerable to clickjacking. According to the application developers, a fix may be months away. Which of the following should a security engineer configure on the web server to help mitigate the issue?
(Multiple Choice)
4.8/5  (25)
(25)
Showing 141 - 160 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)