Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
During a security assessment, activities were divided into two phases: internal and external exploitation. The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter. Which of the following methods is the assessment team most likely to employ NEXT?
(Multiple Choice)
4.7/5  (33)
(33)
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system. Which of the following is MOST likely to be reviewed during the assessment? (Choose two.)
(Multiple Choice)
4.9/5  (35)
(35)
A medical facility wants to purchase mobile devices for doctors and nurses. To ensure accountability, each individual will be assigned a separate mobile device. Additionally, to protect patients' health information, management has identified the following requirements: Data must be encrypted at rest. The device must be disabled if it leaves the facility. The device must be disabled when tampered with. Which of the following technologies would BEST support these requirements? (Select two.)
(Multiple Choice)
4.8/5  (30)
(30)
A secure facility has a server room that currently is controlled by a simple lock and key, and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators' smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are: It cannot be invasive to the end user. It must be utilized as a second factor. Information sharing must be avoided. It must have a low false acceptance rate. Which of the following BEST meets the criteria?
(Multiple Choice)
4.7/5  (24)
(24)
A security researcher is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds. Based on the information available to the researcher, which of the following is the MOST likely threat profile?
(Multiple Choice)
4.9/5  (35)
(35)
A company has gone through a round of phishing attacks. More than 200 users have had their workstation infected because they clicked on a link in an email. An incident analysis has determined an executable ran and compromised the administrator account on each workstation. Management is demanding the information security team prevent this from happening again. Which of the following would BEST prevent this from happening again?
(Multiple Choice)
4.8/5  (30)
(30)
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
(Multiple Choice)
4.8/5  (36)
(36)
A security engineer is embedded with a development team to ensure security is built into products being developed. The security engineer wants to ensure developers are not blocked by a large number of security requirements applied at specific schedule points. Which of the following solutions BEST meets the engineer's goal?
(Multiple Choice)
4.9/5  (29)
(29)
Click on the exhibit buttons to view the four messages. 
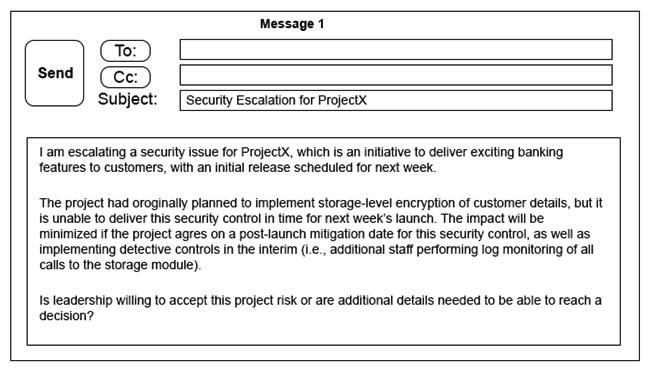
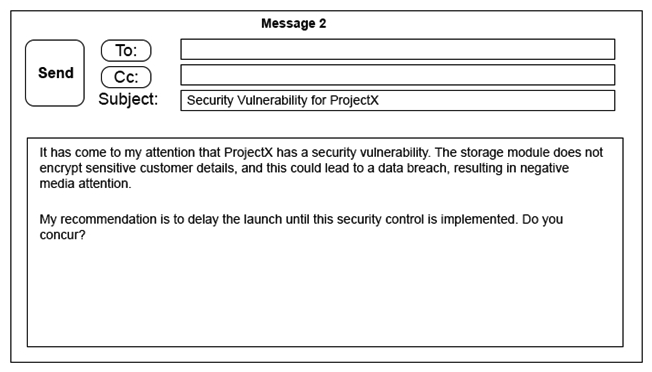
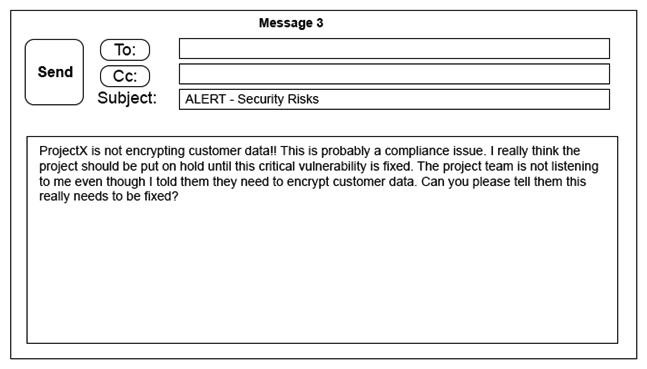
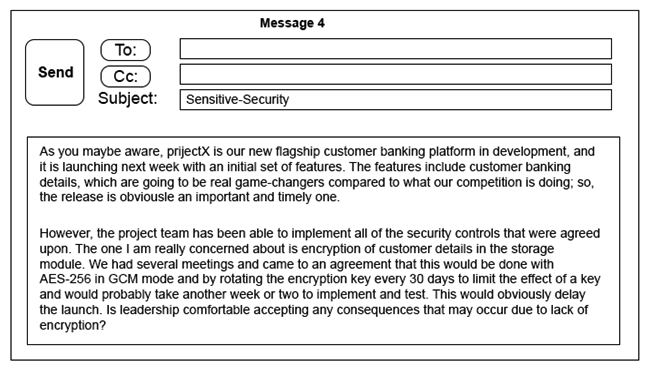 A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
(Multiple Choice)
4.8/5  (41)
(41)
A security appliance vendor is reviewing an RFP that is requesting solutions for the defense of a set of web-based applications. This RFP is from a financial institution with very strict performance requirements. The vendor would like to respond with its solutions. Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
(Multiple Choice)
4.9/5  (34)
(34)
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools. Additionally, sensitive information was compromised during a recent security breach of a remote access session from an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following: Secure messaging between internal users using digital signatures Secure sites for video-conferencing sessions Presence information for all office employees Restriction of certain types of messages to be allowed into the network. Which of the following applications must be configured to meet the new requirements? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
(Multiple Choice)
4.9/5  (32)
(32)
A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
(Multiple Choice)
4.9/5  (37)
(37)
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly. Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems. Which of the following should the project manager use to determine the source of the defined algorithm in use?
(Multiple Choice)
4.8/5  (37)
(37)
An organization is currently performing a market scan for managed security services and EDR capability. Which of the following business documents should be released to the prospective vendors in the first step of the process? (Select TWO).
(Multiple Choice)
4.8/5  (33)
(33)
Which of the following is the GREATEST security concern with respect to BYOD?
(Multiple Choice)
4.8/5  (22)
(22)
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company's web servers can be obtained publicly and is not proprietary in any way. The next day the company's website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website. Which of the following is the FIRST action the company should take?
(Multiple Choice)
4.8/5  (24)
(24)
An organization is struggling to differentiate threats from normal traffic and access to systems. A security engineer has been asked to recommend a system that will aggregate data and provide metrics that will assist in identifying malicious actors or other anomalous activity throughout the environment. Which of the following solutions should the engineer recommend?
(Multiple Choice)
4.9/5  (38)
(38)
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
(Multiple Choice)
4.9/5  (36)
(36)
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
(Multiple Choice)
4.9/5  (40)
(40)
Showing 101 - 120 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)