Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
An external red team is brought into an organization to perform a penetration test of a new network-based application. The organization deploying the network application wants the red team to act like remote, external attackers, and instructs the team to use a black-box approach. Which of the following is the BEST methodology for the red team to follow?
(Multiple Choice)
4.9/5  (35)
(35)
A security engineer is working to secure an organization's VMs. While reviewing the workflow for creating VMs on demand, the engineer raises a concern about the integrity of the secure boot process of the VM guest. Which of the following would BEST address this concern?
(Multiple Choice)
4.8/5  (30)
(30)
A small firm's newly created website has several design flaws. The developer created the website to be fully compatible with ActiveX scripts in order to use various digital certificates and trusting certificate authorities. However, vulnerability testing indicates sandboxes were enabled, which restricts the code's access to resources within the user's computer. Which of the following is the MOST likely cause of the error?
(Multiple Choice)
4.9/5  (33)
(33)
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in a secure environment?
(Multiple Choice)
4.8/5  (26)
(26)
A software company is releasing a new mobile application to a broad set of external customers. Because the software company is rapidly releasing new features, it has built in an over-the-air software update process that can automatically update the application at launch time. Which of the following security controls should be recommended by the company's security architect to protect the integrity of the update process? (Choose two.)
(Multiple Choice)
4.7/5  (31)
(31)
An advanced threat emulation engineer is conducting testing against a client's network. The engineer conducts the testing in as realistic a manner as possible. Consequently, the engineer has been gradually ramping up the volume of attacks over a long period of time. Which of the following combinations of techniques would the engineer MOST likely use in this testing? (Choose three.)
(Multiple Choice)
4.7/5  (34)
(34)
A company that has been breached multiple times is looking to protect cardholder data. The previous undetected attacks all mimicked normal administrative-type behavior. The company must deploy a host solution to meet the following requirements: Detect administrative actions Block unwanted MD5 hashes Provide alerts Stop exfiltration of cardholder data Which of the following solutions would BEST meet these requirements? (Choose two.)
(Multiple Choice)
4.8/5  (30)
(30)
A security engineer is assisting a developer with input validation, and they are studying the following code block: 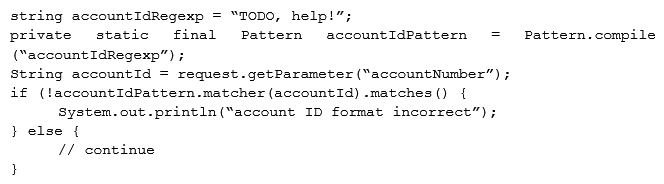 The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system. Which of the following would be the BEST advice for the security engineer to give to the developer?
The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system. Which of the following would be the BEST advice for the security engineer to give to the developer?
(Multiple Choice)
4.8/5  (34)
(34)
A recent assessment identified that several users' mobile devices are running outdated versions of endpoint security software that do not meet the company's security policy. Which of the following should be performed to ensure the users can access the network and meet the company's security requirements?
(Multiple Choice)
4.9/5  (32)
(32)
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically destroyed. Which of the following factors is the regulation intended to address?
(Multiple Choice)
4.7/5  (32)
(32)
A security analyst for a bank received an anonymous tip on the external banking website showing the following: Protocols supported - TLS 1.0 - SSL 3 - SSL 2 Cipher suites supported - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA-ECDH p256r1 - TLS_DHE_RSA_WITH_AES_256_CBC_SHA-DH 1024bit - TLS_RSA_WITH_RC4_128_SHA TLS_FALLBACK_SCSV non supported POODLE Weak PFS OCSP stapling supported Which of the following should the analyst use to reproduce these findings comprehensively?
(Multiple Choice)
5.0/5  (29)
(29)
A company has decided to lower costs by conducting an internal assessment on specific devices and various internal and external subnets. The assessment will be done during regular office hours, but it must not affect any production servers. Which of the following would MOST likely be used to complete the assessment? (Select two.)
(Multiple Choice)
4.8/5  (30)
(30)
A security analyst is inspecting pseudocode of the following multithreaded application:  Which of the following security concerns is evident in the above pseudocode?
Which of the following security concerns is evident in the above pseudocode?
(Multiple Choice)
4.7/5  (43)
(43)
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, "criticalValue" indicates if an emergency is underway:  Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
(Multiple Choice)
4.7/5  (31)
(31)
An agency has implemented a data retention policy that requires tagging data according to type before storing it in the data repository. The policy requires all business emails be automatically deleted after two years. During an open records investigation, information was found on an employee's work computer concerning a conversation that occurred three years prior and proved damaging to the agency's reputation. Which of the following MOST likely caused the data leak?
(Multiple Choice)
4.8/5  (31)
(31)
The Chief Financial Officer (CFO) of an organization wants the IT department to add the CFO's account to the domain administrator group. The IT department thinks this is risky and wants support from the security manager before proceeding. Which of the following BEST supports the argument against providing the CFO with domain administrator access?
(Multiple Choice)
4.9/5  (31)
(31)
An organization just merged with an organization in another legal jurisdiction and must improve its network security posture in ways that do not require additional resources to implement data isolation. One recommendation is to block communication between endpoint PCs. Which of the following would be the BEST solution?
(Multiple Choice)
4.7/5  (22)
(22)
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO's first task is to write a new, relevant risk assessment for the organization. Which of the following help to the CISO find relevant risks to the organization? (Choose two.)
(Multiple Choice)
4.8/5  (37)
(37)
A company is migrating systems from an on-premises facility to a third-party managed datacenter. For continuity of operations and business agility, remote access to all hardware platforms must be available at all times. Access controls need to be very robust and provide an audit trail. Which of the following security controls will meet the company's objectives? (Select two.)
(Multiple Choice)
4.9/5  (39)
(39)
An external red team member conducts a penetration test, attempting to gain physical access to a large organization's server room in a branch office. During reconnaissance, the red team member sees a clearly marked door to the server room, located next to the lobby, with a tumbler lock. Which of the following is BEST for the red team member to bring on site to open the locked door as quickly as possible without causing significant damage?
(Multiple Choice)
4.8/5  (35)
(35)
Showing 21 - 40 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)