Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A software development company lost customers recently because of a large number of software issues. These issues were related to integrity and availability defects, including buffer overflows, pointer dereferences, and others. Which of the following should the company implement to improve code quality? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data: 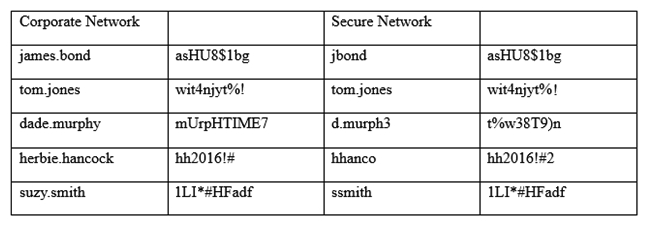 Which of the following tools was used to gather this information from the hashed values in the file?
Which of the following tools was used to gather this information from the hashed values in the file?
(Multiple Choice)
4.8/5  (30)
(30)
A company is not familiar with the risks associated with IPv6. The systems administrator wants to isolate IPv4 from IPv6 traffic between two different network segments. Which of the following should the company implement? (Select TWO)
(Multiple Choice)
4.9/5  (29)
(29)
A user asks a security practitioner for recommendations on securing a home network. The user recently purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some of the IoT devices are wearables, and other are installed in the user's automobiles. The current home network is configured as a single flat network behind an ISP-supplied router. The router has a single IP address, and the router performs NAT on incoming traffic to route it to individual devices. Which of the following security controls would address the user's privacy concerns and provide the BEST level of security for the home network?
(Multiple Choice)
4.8/5  (36)
(36)
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements: Support server, laptop, and desktop infrastructure Due to limited security resources, implement active protection capabilities Provide users with the ability to self-service classify information and apply policies Protect data-at-rest and data-in-use Which of the following endpoint capabilities would BEST meet the above requirements? (Choose two.)
(Multiple Choice)
4.9/5  (36)
(36)
A company has decided to replace all the T-1 uplinks at each regional office and move away from using the existing MPLS network. All regional sites will use high-speed connections and VPNs to connect back to the main campus. Which of the following devices would MOST likely be added at each location?
(Multiple Choice)
4.9/5  (36)
(36)
A firewall specialist has been newly assigned to participate in red team exercises and needs to ensure the skills represent real-world threats. Which of the following would be the BEST choice to help the new team member learn bleeding-edge techniques?
(Multiple Choice)
4.8/5  (29)
(29)
A technician is configuring security options on the mobile device manager for users who often utilize public Internet connections while travelling. After ensuring that full disk encryption is enabled, which of the following security measures should the technician take? (Choose two.)
(Multiple Choice)
4.9/5  (39)
(39)
A security analyst is reviewing the following company requirements prior to selecting the appropriate technical control configuration and parameter: RTO: 2 days RPO: 36 hours MTTR: 24 hours MTBF: 60 days Which of the following solutions will address the RPO requirements?
(Multiple Choice)
4.9/5  (31)
(31)
A technician is reviewing the following log: 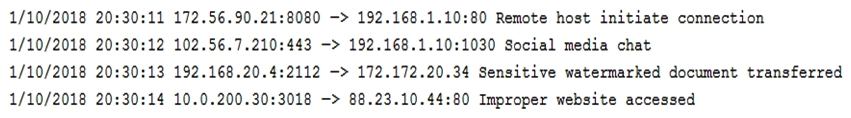 Which of the following tools should the organization implement to reduce the highest risk identified in this log?
Which of the following tools should the organization implement to reduce the highest risk identified in this log?
(Multiple Choice)
4.7/5  (32)
(32)
A software development team is conducting functional and user acceptance testing of internally developed web applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise directory to authenticate to each application. The solution stores the username in plain text and the corresponding password as an encoded string in a script within a file, located on a globally accessible network share. The account credentials used belong to the development team lead. To reduce the risks associated with this scenario while minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
(Multiple Choice)
4.9/5  (37)
(37)
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following: High-impact controls implemented: 6 out of 10 Medium-impact controls implemented: 409 out of 472 Low-impact controls implemented: 97 out of 1000 The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information: Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000 Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000 Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
(Multiple Choice)
4.8/5  (27)
(27)
A government contractor was the victim of a malicious attack that resulted in the theft of sensitive information. An analyst's subsequent investigation of sensitive systems led to the following discoveries: There was no indication of the data owner's or user's accounts being compromised. No database activity outside of previous baselines was discovered. All workstations and servers were fully patched for all known vulnerabilities at the time of the attack. It was likely not an insider threat, as all employees passed polygraph tests. Given this scenario, which of the following is the MOST likely attack that occurred?
(Multiple Choice)
4.8/5  (33)
(33)
A systems analyst is concerned that the current authentication system may not provide the appropriate level of security. The company has integrated WAYF within its federation system and implemented a mandatory two-step authentication system. Some accounts are still becoming compromised via phishing attacks that redirect users to a fake portal, which is automatically collecting and replaying the stolen credentials. Which of the following is a technical solution that would BEST reduce the risk of similar compromises?
(Multiple Choice)
4.8/5  (29)
(29)
A hospital's security team recently determined its network was breached and patient data was accessed by an external entity. The Chief Information Security Officer (CISO) of the hospital approaches the executive management team with this information, reports the vulnerability that led to the breach has already been remediated, and explains the team is continuing to follow the appropriate incident response plan. The executive team is concerned about the hospital's brand reputation and asks the CISO when the incident should be disclosed to the affected patients. Which of the following is the MOST appropriate response?
(Multiple Choice)
4.9/5  (38)
(38)
Company.org has requested a black-box security assessment be performed on key cyber terrain. One area of concern is the company's SMTP services. The security assessor wants to run reconnaissance before taking any additional action and wishes to determine which SMTP server is Internet-facing. Which of the following commands should the assessor use to determine this information?
(Multiple Choice)
4.8/5  (37)
(37)
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly. Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems. Which of the following should the project manager use to determine the source of the defined algorithm in use?
(Multiple Choice)
4.8/5  (34)
(34)
A company has made it a spending priority to implement security architectures that will be resilient during an attack. Recent incidents have involved attackers leveraging latent vulnerabilities in cryptographic implementations and VPN concentrators to be able to compromise sensitive information. Patches have been slowly released for these emergent vulnerabilities, leaving weeks to months of exposed and vulnerable attack surface. Which of the following approaches would be BEST to increase enterprise resilience during similar future attacks?
(Multiple Choice)
4.7/5  (34)
(34)
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
(Multiple Choice)
5.0/5  (42)
(42)
A company is not familiar with the risks associated with IPv6. The systems administrator wants to isolate IPv4 from IPv6 traffic between two different network segments. Which of the following should the company implement? (Choose two.)
(Multiple Choice)
4.8/5  (43)
(43)
Showing 161 - 180 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)