Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
An organization is improving its web services to enable better customer engagement and self-service. The organization has a native mobile application and a rewards portal provided by a third party. The business wants to provide customers with the ability to log in once and have SSO between each of the applications. The integrity of the identity is important so it can be propagated through to back-end systems to maintain a consistent audit trail. Which of the following authentication and authorization types BEST meet the requirements? (Choose two.)
(Multiple Choice)
4.8/5  (31)
(31)
A development team releases updates to an application regularly. The application is compiled with several standard, open-source security products that require a minimum version for compatibility. During the security review portion of the development cycle, which of the following should be done to minimize possible application vulnerabilities?
(Multiple Choice)
4.9/5  (39)
(39)
While conducting a BIA for a proposed acquisition, the IT integration team found that both companies outsource CRM services to competing and incompatible third-party cloud services. The decision has been made to bring the CRM service in-house, and the IT team has chosen a future solution. With which of the following should the Chief Information Security Officer (CISO) be MOST concerned? (Choose two.)
(Multiple Choice)
5.0/5  (38)
(38)
Developers are working on a new feature to add to a social media platform. The new feature involves users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned about various types of abuse that might occur due to this new feature. The DPO state the new feature cannot be released without addressing the physical safety concerns of the platform's users. Which of the following controls would BEST address the DPO's concerns?
(Multiple Choice)
4.9/5  (35)
(35)
A security manager needed to protect a high-security data center, so the manager installed a mantrap that can detect an employee's heartbeat, weight, and badge. Which of the following did the security manager implement?
(Multiple Choice)
4.9/5  (45)
(45)
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data. 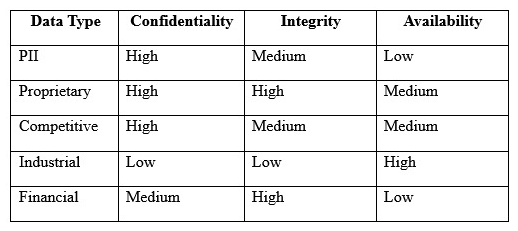 Based on the data classification table above, which of the following BEST describes the overall classification?
Based on the data classification table above, which of the following BEST describes the overall classification?
(Multiple Choice)
4.9/5  (36)
(36)
Designing a system in which only information that is essential for a particular job task is allowed to be viewed can be accomplished successfully by using:
(Multiple Choice)
4.7/5  (31)
(31)
Which of the following attacks can be mitigated by proper data retention policies?
(Multiple Choice)
4.9/5  (34)
(34)
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following: 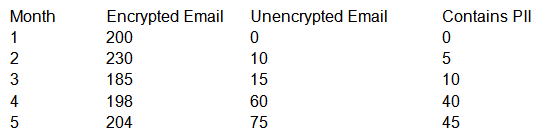 Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?
(Multiple Choice)
4.9/5  (35)
(35)
A security consultant was hired to audit a company's password are account policy. The company implements the following controls: Minimum password length: 16 Maximum password age: 0 Minimum password age: 0 Password complexity: disabled Store passwords in plain text: disabled Failed attempts lockout: 3 Lockout timeout: 1 hour The password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest number of plain text passwords in the shortest amount of time?
(Multiple Choice)
4.8/5  (30)
(30)
Following a recent and very large corporate merger, the number of log files an SOC needs to review has approximately tripled. The Chief Information Security Officer (CISO) has not been allowed to hire any more staff for the SOC, but is looking for other ways to automate the log review process so the SOC receives less noise. Which of the following would BEST reduce log noise for the SOC?
(Multiple Choice)
4.7/5  (46)
(46)
The Chief Information Security Officer (CISO) for an organization wants to develop custom IDS rulesets faster, prior to new rules being released by IDS vendors. Which of the following BEST meets this objective?
(Multiple Choice)
4.7/5  (35)
(35)
An internal staff member logs into an ERP platform and clicks on a record. The browser URL changes to: URL: http://192.168.0.100/ERP/accountId=5&action=SELECT Which of the following is the MOST likely vulnerability in this ERP platform?
(Multiple Choice)
4.9/5  (35)
(35)
A company has adopted and established a continuous-monitoring capability, which has proven to be effective in vulnerability management, diagnostics, and mitigation. The company wants to increase the likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle. Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
(Multiple Choice)
4.7/5  (36)
(36)
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data. The consultant reviews the following information: 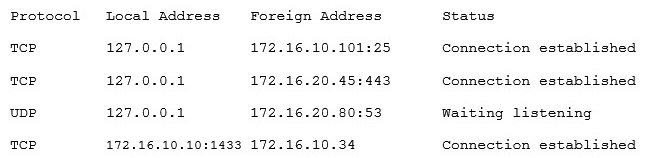 Which of the following commands would have provided this output?
Which of the following commands would have provided this output?
(Multiple Choice)
4.9/5  (31)
(31)
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded. Which of the following should be used to identify weak processes and other vulnerabilities?
(Multiple Choice)
4.9/5  (37)
(37)
To meet a SLA, which of the following document should be drafted, defining the company's internal interdependent unit responsibilities and delivery timelines.
(Multiple Choice)
4.9/5  (34)
(34)
A penetration test is being scoped for a set of web services with API endpoints. The APIs will be hosted on existing web application servers. Some of the new APIs will be available to unauthenticated users, but some will only be available to authenticated users. Which of the following tools or activities would the penetration tester MOST likely use or do during the engagement? (Select TWO.)
(Multiple Choice)
4.9/5  (28)
(28)
A bank is initiating the process of acquiring another smaller bank. Before negotiations happen between the organizations, which of the following business documents would be used as the FIRST step in the process?
(Multiple Choice)
4.8/5  (23)
(23)
Developers are working on anew feature to add to a social media platform. Thew new feature involves users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned about various types of abuse that might occur due to this new feature. The DPO state the new feature cannot be released without addressing the physical safety concerns of the platform's users. Which of the following controls would BEST address the DPO's concerns?
(Multiple Choice)
4.8/5  (28)
(28)
Showing 61 - 80 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)