Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
An attacker has been compromising banking institution targets across a regional area. The Chief Information Security Officer (CISO) at a local bank wants to detect and prevent an attack before the bank becomes a victim. Which of the following actions should the CISO take?
(Multiple Choice)
5.0/5  (20)
(20)
An administrator is working with management to develop policies related to the use of the cloud-based resources that contain corporate data. Management plans to require some control over organizational data stored on personal devices, such as tablets. Which of the following controls would BEST support management's policy?
(Multiple Choice)
4.8/5  (31)
(31)
A government contracting company issues smartphones to employees to enable access to corporate resources. Several employees will need to travel to a foreign country for business purposes and will require access to their phones. However, the company recently received intelligence that its intellectual property is highly desired by the same country's government. Which of the following MDM configurations would BEST reduce the risk of compromise while on foreign soil?
(Multiple Choice)
4.7/5  (26)
(26)
Given the following output from a local PC: 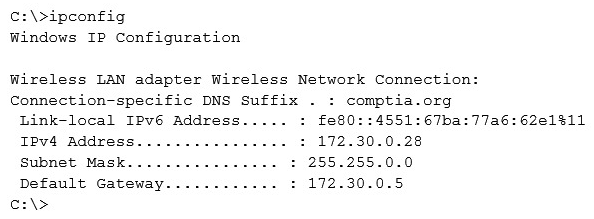 Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
(Multiple Choice)
4.8/5  (28)
(28)
An analyst is investigating anomalous behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the "compose" window. Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
(Multiple Choice)
4.8/5  (33)
(33)
The Chief Financial Officer (CFO) of a major hospital system has received a ransom letter that demands a large sum of cryptocurrency be transferred to an anonymous account. If the transfer does not take place within ten hours, the letter states that patient information will be released on the dark web. A partial listing of recent patients is included in the letter. This is the first indication that a breach took place. Which of the following steps should be done FIRST?
(Multiple Choice)
4.9/5  (38)
(38)
After investigating virus outbreaks that have cost the company $1000 per incident, the company's Chief Information Security Officer (CISO) has been researching new antivirus software solutions to use and be fully supported for the next two years. The CISO has narrowed down the potential solutions to four candidates that meet all the company's performance and capability requirements: 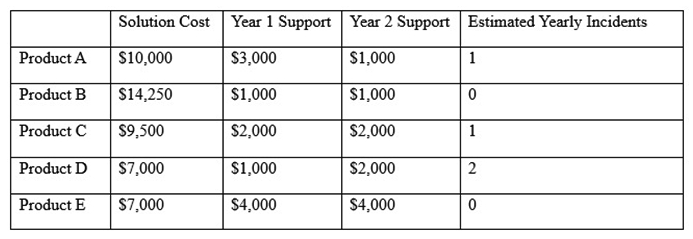 Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?
Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?
(Multiple Choice)
4.8/5  (35)
(35)
A Chief Information Security Officer (CISO) of a large financial institution undergoing an IT transformation program wants to embed security across the business rapidly and across as many layers of the business as possible to achieve quick wins and reduce risk to the organization. Which of the following business areas should the CISO target FIRST to best meet the objective?
(Multiple Choice)
4.8/5  (28)
(28)
An internal staff member logs into an ERP platform and clicks on a record. The browser URL changes to: URL: http://192.168.0.100/ERP/accountId=5&action=SELECT Which of the following is the MOST likely vulnerability in this ERP platform?
(Multiple Choice)
4.8/5  (39)
(39)
A software development team has spent the last 18 months developing a new web-based front-end that will allow clients to check the status of their orders as they proceed through manufacturing. The marketing team schedules a launch party to present the new application to the client base in two weeks. Before the launch, the security team discovers numerous flaws that may introduce dangerous vulnerabilities, allowing direct access to a database used by manufacturing. The development team did not plan to remediate these vulnerabilities during development. Which of the following SDLC best practices should the development team have followed?
(Multiple Choice)
4.8/5  (35)
(35)
An organization's Chief Financial Officer (CFO) was the target of several different social engineering attacks recently. The CFO has subsequently worked closely with the Chief Information Security Officer (CISO) to increase awareness of what attacks may look like. An unexpected email arrives in the CFO's inbox from a familiar name with an attachment. Which of the following should the CISO task a security analyst with to determine whether or not the attachment is safe?
(Multiple Choice)
4.7/5  (41)
(41)
A security manager recently categorized an information system. During the categorization effort, the manager determined the loss of integrity of a specific information type would impact business significantly. Based on this, the security manager recommends the implementation of several solutions. Which of the following, when combined, would BEST mitigate this risk? (Choose two.)
(Multiple Choice)
4.9/5  (35)
(35)
The finance department has started to use a new payment system that requires strict PII security restrictions on various network devices. The company decides to enforce the restrictions and configure all devices appropriately. Which of the following risk response strategies is being used?
(Multiple Choice)
4.8/5  (41)
(41)
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing using corporate-owned resources be monitored. Which of the following would allow the organization to meet its requirement? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be exploited so resources can be prioritized to migrate the most dangerous risks. The CISO wants the security engineer to act in the same manner as would an external threat, while using vulnerability scan results to prioritize any actions. Which of the following approaches is described?
(Multiple Choice)
4.9/5  (47)
(47)
Which of the following are the MOST likely vectors for the unauthorized or unintentional inclusion of vulnerable code in a software company's final software releases? (Choose two.)
(Multiple Choice)
4.8/5  (41)
(41)
A security architect is reviewing the code for a company's financial website. The architect suggests adding the following HTML element, along with a server-side function, to generate a random number on the page used to initiate a funds transfer: <input type="hidden" name="token" value=generateRandomNumber()> Which of the following attacks is the security architect attempting to prevent?
(Multiple Choice)
4.8/5  (36)
(36)
Developers are working on a new feature to add to a social media platform. The new feature involves users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned about various types of abuse that might occur due to this new feature. The DPO states the new feature cannot be released without addressing the physical safety concerns of the platform's users. Which of the following controls would BEST address the DPO's concerns?
(Multiple Choice)
4.9/5  (41)
(41)
A security architect is implementing security measures in response to an external audit that found vulnerabilities in the corporate collaboration tool suite. The report identified the lack of any mechanism to provide confidentiality for electronic correspondence between users and between users and group mailboxes. Which of the following controls would BEST mitigate the identified vulnerability?
(Multiple Choice)
4.7/5  (30)
(30)
Due to a recent acquisition, the security team must find a way to secure several legacy applications. During a review of the applications, the following issues are documented: The applications are considered mission-critical. The applications are written in code languages not currently supported by the development staff. Security updates and patches will not be made available for the applications. Username and passwords do not meet corporate standards. The data contained within the applications includes both PII and PHI. The applications communicate using TLS 1.0. Only internal users access the applications. Which of the following should be utilized to reduce the risk associated with these applications and their current architecture?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 301 - 320 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)