Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
You have been asked to design a wireless network solution that will implement context-aware services on an existing network that was initially deployed for data traffic only. Which two design principles would you follow to increase the location accuracy with the least possible impact on the current setup? (Choose two.)
(Multiple Choice)
4.9/5  (30)
(30)
You are asked to provide a design that allows full dynamic routing updates between two networks: one network runs OSPF, and the other network runs EIGRP. Two links with an EIGRP neighbor relationship are provided to connect the networks and exchange routes. You are considering the use of routing loops. Which route-filtering method should you recommend, in order to prevent loops with the least amount of reconfiguration effort?
(Multiple Choice)
4.8/5  (32)
(32)
Refer to the exhibit. "Pass Any Exam. Any Time." - www.actualtests.com 3 Cisco 352-001 Exam 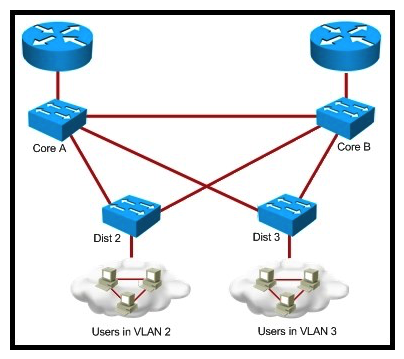 You are designing a spanning-tree network for a small campus. Which two of these options would result in a trouble-free spanning-tree network design? (Choose two.)
You are designing a spanning-tree network for a small campus. Which two of these options would result in a trouble-free spanning-tree network design? (Choose two.)
(Multiple Choice)
4.8/5  (42)
(42)
Configure routers P4S-RE and P4S-RF as route reflectors of router P4S-RA in this network presented in the following exhibit. When router P4S-RC transmits a route to router P4S-RA, which router or routers will router P4S-RA send an update to? 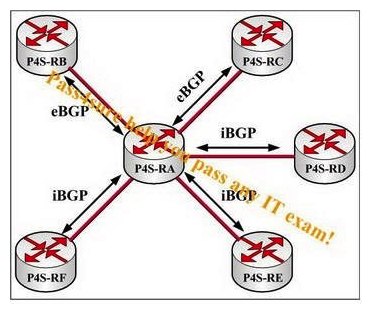
(Multiple Choice)
4.8/5  (31)
(31)
Refer to the exhibit. 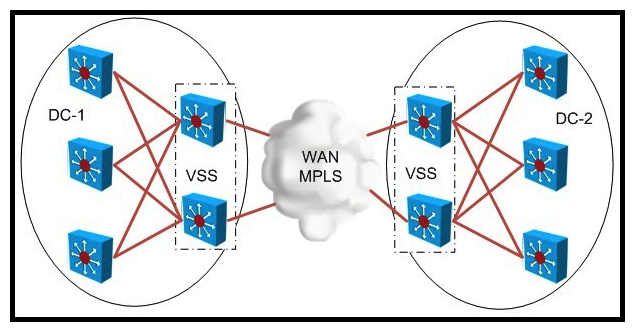 When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)
When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)
(Multiple Choice)
4.9/5  (41)
(41)
You are a network designer for the P4S company, study the exhibit carefully. You are asked to design a Layer 2 VPN. Now, 90% of traffic from the remote branches of P4S comes to HQ. There are hubs and old switches at remotes not having dot1q capability. But at the remote branches, P4S has not the budget to invest in new equipment. Other than converting the remote branches to Layer 2 VPN, P4S would like to connect all the branches to the HQ site to make sure that the branches have access to dot1q capability. How to meet this requirement, if not, why? 
(Multiple Choice)
4.9/5  (34)
(34)
What are two design advantages to using virtual port channel? (Choose two.)
(Multiple Choice)
4.8/5  (37)
(37)
A customer with a dedicated Frame Relay network is planning to move its circuits onto a service provider MPLS network. Instead of moving to Ethernet access links right away, the customer wants to tunnel the Frame Relay information across the MPLS network using AToM pseudowire. How is QoS information transmitted across an AToM pseudowire?
(Multiple Choice)
5.0/5  (26)
(26)
Refer to the exhibit. This new OSPF network has four areas, but the hub-and-spoke area experiences frequent flapping. You must fix this design failure. Which two mechanisms can you use to isolate the data center area from the hub-and-spoke area without losing IP connectivity? (Choose two.)
(Multiple Choice)
4.9/5  (28)
(28)
Refer to the exhibit. 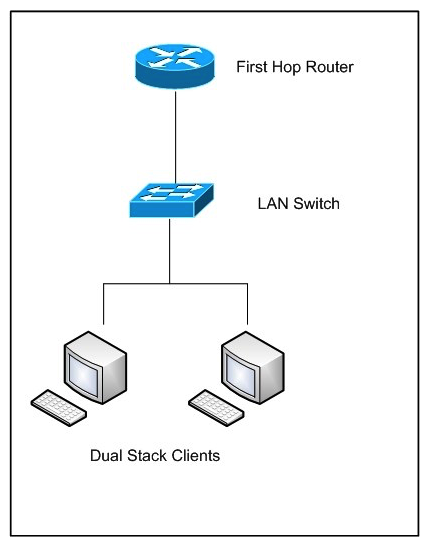 Acme Corporation hired you as a network designer to upgrade their network so that it supports IPv4 and IPv6 multicast. Which two protocols are needed on the LAN switch? (Choose two.)
Acme Corporation hired you as a network designer to upgrade their network so that it supports IPv4 and IPv6 multicast. Which two protocols are needed on the LAN switch? (Choose two.)
(Multiple Choice)
4.8/5  (45)
(45)
What are two considerations to using IP Multicast delivery? (Choose two.)
(Multiple Choice)
4.7/5  (36)
(36)
The P4S company has just merged with the VR company. However, they keep IGP and BGP independent of each other. A common ISP provides them with services for their Internet connectivity. During the merge, the P4S company and the VR company will provision a point-to-point link between the two networks. What is the simplest design option that will allow data to travel between A and B without passing through the ISP?
(Multiple Choice)
4.7/5  (34)
(34)
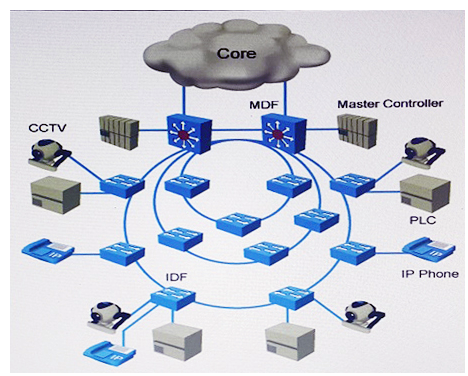 Refer to the exhibit. This smart city has decided to deploy a converged network for video surveillance and applications for utility services. These new applications are delay-sensitive and require strict convergence times of less than 50 milliseconds. The network is expected to have up to 50 intermediate distribution frames per ring. Which protocol provides less than 50 milliseconds convergence?
Refer to the exhibit. This smart city has decided to deploy a converged network for video surveillance and applications for utility services. These new applications are delay-sensitive and require strict convergence times of less than 50 milliseconds. The network is expected to have up to 50 intermediate distribution frames per ring. Which protocol provides less than 50 milliseconds convergence?
(Multiple Choice)
4.9/5  (34)
(34)
The P4S company's external routers BGP peer with multiple service providers and external organizations. In all situations, the external routers are peered with their BGP neighbors through directly-connected interfaces. How does GTSM provide additional security for your BGP speakers?
(Multiple Choice)
4.7/5  (37)
(37)
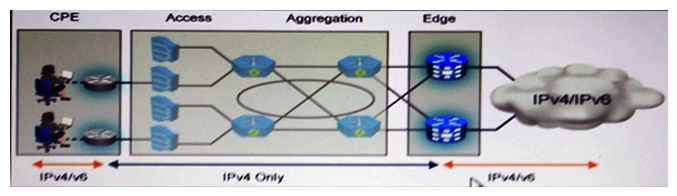 Refer to the exhibit. The service provider ACME wants to offer IPv6 services to their subscribers. However, their access and aggregation devices are IPv4-only and not capable of IPv6 transport without hardware upgrade. The CPE and edge equipment can be upgraded via software to support IPv6 services. Assume that all the listed technologies are available on the CPE and edge equipment. Which two technologies can be used to extend IPv6 services from edge to CPE? (Choose two.)
Refer to the exhibit. The service provider ACME wants to offer IPv6 services to their subscribers. However, their access and aggregation devices are IPv4-only and not capable of IPv6 transport without hardware upgrade. The CPE and edge equipment can be upgraded via software to support IPv6 services. Assume that all the listed technologies are available on the CPE and edge equipment. Which two technologies can be used to extend IPv6 services from edge to CPE? (Choose two.)
(Multiple Choice)
4.9/5  (28)
(28)
As part of the security protocol for your network design, you have designated that option 82 is enabled for DHCP snooping. When option 82 is enabled, which information will be added to the DHCP request?
(Multiple Choice)
4.9/5  (31)
(31)
Refer to the exhibit. You are designing a data center migration from one location to another, which requires all existing VLANs spanned to the new data center to maintain host IP addressing. Two temporary Gigabit Ethernet circuits are available to extend the VLANs at Layer 2 to the new location as trunk links between core switches in each location. Which solution provides maximum fault isolation between the two data centers to ensure that a Layer 2 issue in one data center does not affect the other during the migration? 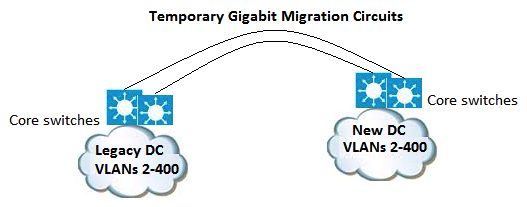
(Multiple Choice)
4.9/5  (32)
(32)
The packets discovered are considered part of an attack. What benefit can be obtained by using a packet scrubbing device to redirect them?
(Multiple Choice)
4.9/5  (34)
(34)
Which two IEEE standards are commonly used at the data link layer for an access network, in an IoT environment? (Choose two.)
(Multiple Choice)
4.8/5  (30)
(30)
According to the following exhibit, will traffic sourced from router P4S-RA and destined for a host on network 10.1.1.0/24 always take the optimal path to that host? 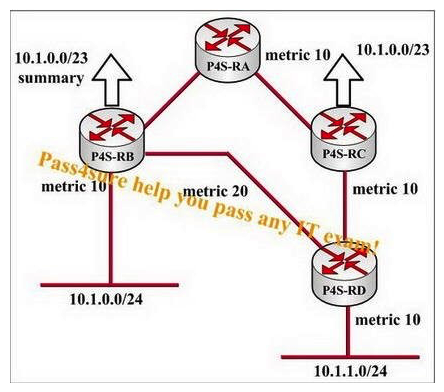
(Multiple Choice)
4.7/5  (30)
(30)
Showing 181 - 200 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)