Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which two components are of effective change management planning? (Choose two.)
(Multiple Choice)
4.7/5  (43)
(43)
You are a network technician for the P4S company, study the exhibit carefully. P4S-R1 is redistributing 10.1.5.0/24 into Area 1 in this network. Which LSA containing 10.1.5.0/24 will P4S-R6 have in its database? 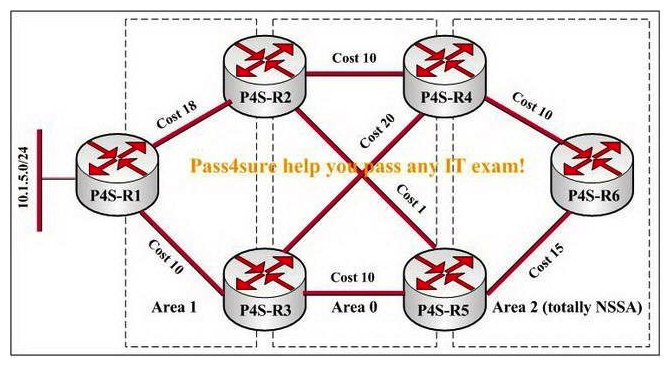
(Multiple Choice)
4.7/5  (25)
(25)
Company X will be integrating an IPv6 application into their network and wants to develop a test environment to evaluate application performance across the network. This application will require both unicast and multicast communications. The company can do this implementation only in certain areas of its existing IPv4-only network, but wants all areas to communicate with each other. When developing the design to provide connectivity between these testing locations, what tunneling technology would work in this scenario?
(Multiple Choice)
4.9/5  (41)
(41)
Refer to the exhibit. "Pass Any Exam. Any Time." - www.actualtests.com 5 Cisco 352-001 Exam 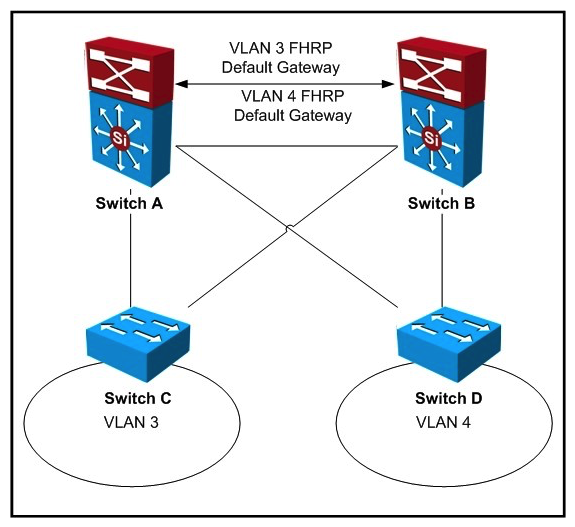 If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
(Multiple Choice)
4.8/5  (38)
(38)
In a network, all routers deploy FIFO queuing. The primary application running on the network is data backup by use of FTP. At certain times, users experience cyclical performance degradation. Which two items can mitigate this problem and help ensure bandwidth is used effectively in the network? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
Which design concern should be accounted for in all Layer 3 virtualization technologies?
(Multiple Choice)
4.9/5  (41)
(41)
The Sender Policy Framework (SPF) is an open standard specifying a technical method to prevent sender address forgery. When configuring the SPF exponential backoff timer, which one of the following items is among the primary issues to consider?
(Multiple Choice)
4.7/5  (34)
(34)
Connecting four routers running IS-IS to a single Ethernet link. Then, a fifth router is connected, the priority of this router is higher than that of the other four. What will happen?
(Multiple Choice)
4.8/5  (35)
(35)
A network designer decides to connect two labs together to test multicast features interoperability. Before the networks are connected together, the network administrator mentions that overlapping multicast IP addresses between the two labs will cause issues because all the routers on the network are provisioned for Source-Specific Multicast using IGMPv3. Which statement about the connectivity of both multicast domains is true?
(Multiple Choice)
4.7/5  (34)
(34)
Refer to the exhibit. 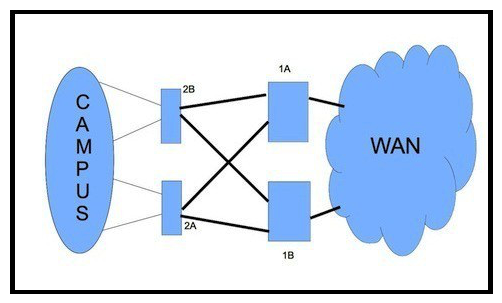 How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
(Multiple Choice)
4.9/5  (29)
(29)
Which two actions are performed at the distribution layer of the three-layer hierarchical network design model?
(Multiple Choice)
4.7/5  (35)
(35)
What is a key design aspect to be considered when designing an IP network that will be carrying real-time VoIP traffic?
(Multiple Choice)
4.9/5  (27)
(27)
You are deploying a nationwide intranet solution for a company with 4 data centers and 400 remote branches connected via a provider-based solution. As part of the network design, you must ensure efficient content distribution of training material to remote sites. Which VPN technology leverages replication in the network core and provides for efficient bandwidth optimization?
(Multiple Choice)
4.7/5  (38)
(38)
Which three processes are part of the ITILv3 Service Operation? (Choose three.)
(Multiple Choice)
4.9/5  (37)
(37)
Which two statements about QoS marking are true? (Choose two.)
(Multiple Choice)
4.8/5  (37)
(37)
You are designing a solution to eliminate the risk of high CPU utilization on a core network composed of CRS-1 devices. Which option would eliminate the risk of high CPU utilization across the network?
(Multiple Choice)
4.7/5  (28)
(28)
You work as a network technician, study the exhibit carefully. In an MPLS-enabled network, a service provider has three N-PEs and three U-PEs. The VPLS and H-VPLS services are MPLS-enabled. Two customers have subscribed to this Layer 2 service. In order to provide full connectivity between the customer sites, how many LDP sessions must be created between the PE devices? 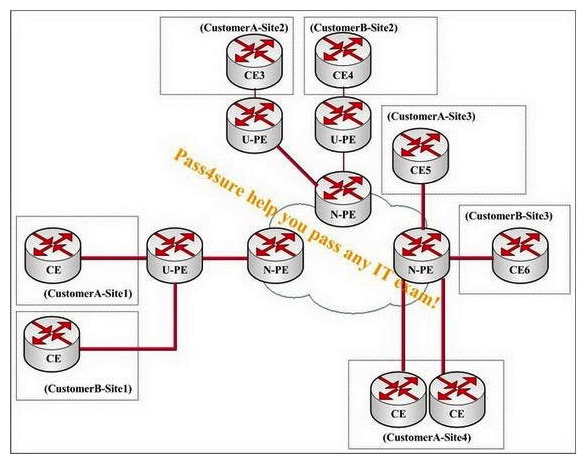
(Multiple Choice)
4.8/5  (34)
(34)
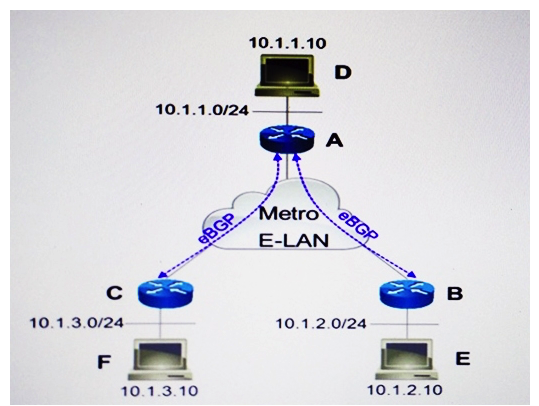 Refer to the exhibit. Company A migrated from Frame Relay WAN to Metro-Ethernet E-LAN service. Router B and C have only eBGP neighbor adjacency with router A using their Metro-Ethernet IP addresses. What happens when host E sends a packet to host F?
Refer to the exhibit. Company A migrated from Frame Relay WAN to Metro-Ethernet E-LAN service. Router B and C have only eBGP neighbor adjacency with router A using their Metro-Ethernet IP addresses. What happens when host E sends a packet to host F?
(Multiple Choice)
4.9/5  (32)
(32)
Which two benefits can be obtained by protecting the control plane of a network device? (Choose two.)
(Multiple Choice)
4.9/5  (36)
(36)
As part of a new network design, you are helping the Network Management Team to develop a proactive report to identify places in the network where problems may happen. The network management tool can poll the network devices only via SNMP GET operations. Which two threshold- crossing metrics should you include in this report? (Choose two.)
(Multiple Choice)
4.8/5  (41)
(41)
Showing 21 - 40 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)