Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which option is true about routing control while using routing protocols in a DMVPN network (or any GRE-over-IPsec network)?
(Multiple Choice)
4.8/5  (44)
(44)
Refer to the exhibit. In the DWDM network, a ring topology carries multiple services between two sites. Which option describes the employed protection design?
(Multiple Choice)
4.8/5  (34)
(34)
Among the design criteria for a network is the requirement that bandwidth capacity be managed proactively. Which two techniques should be used to effectively support the proactive management of network bandwidth capacity? (Choose two.)
(Multiple Choice)
4.8/5  (36)
(36)
With a multicast design, applications can send one copy of each packet and address it to the group of computers that want to receive it. This technique addresses packets to a group of receivers rather than to a single receiver, and it depends on the network to forward the packets to only the networks that need to receive them. Which two of these are characteristics of multicast routing?
(Multiple Choice)
4.9/5  (35)
(35)
WRED is short for Weighted Random Early Detection. Which two descriptions are correct concerning WRED? (Choose two.)
(Multiple Choice)
4.8/5  (44)
(44)
Which description is correct about connecting an IP multicast domain that is operating in PIM dense mode to a PIM sparse mode domain?
(Multiple Choice)
4.8/5  (42)
(42)
Internet Protocol version 6 (IPv6) is an Internet Layer protocol for packet- switched internetworks. Two islands of IPv6 networks are running IS-IS (IPv6 IGP). The routing protocol needs to operate over the tunnel over an IPv4 network. Which tunneling method can achieve this objective?
(Multiple Choice)
4.9/5  (38)
(38)
According to the following exhibit, company 1 contains two autonomous systems (AS1 and AS2) connected via ISP A, which has an AS number of 100. Router P4S-RB and Router P4S-RC are advertising an aggregate of X.X.X.0/23 so that AS1 is able to reach the two server farms. The two links from AS2 are not being used efficiently. How can AS2 use both of the links coming into it? 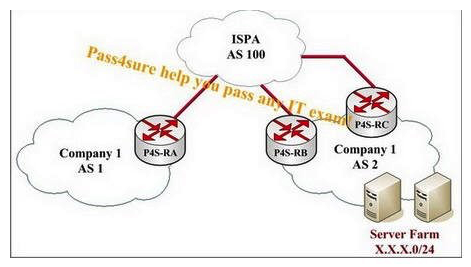
(Multiple Choice)
4.9/5  (31)
(31)
You have been asked to design a high-density wireless network for a university campus. Which three principles would you apply in order to maximize the wireless network capacity? (Choose three.)
(Multiple Choice)
4.8/5  (25)
(25)
You work as a network technician for the P4S Ltd. Study the exhibit carefully, router P4S-RA is the hub router in a Frame Relay hub-and-spoke deployment. Configure router P4S-RA's serial interface as a point-to-multipoint interface, and it is servicing three spoke routers. The link between Router P4S-RC and the frame provider experiences a service disruption, which causes the interface on Router P4S-RC to go down. How does Router P4S-RA learn of this failure in the network and how does it react? 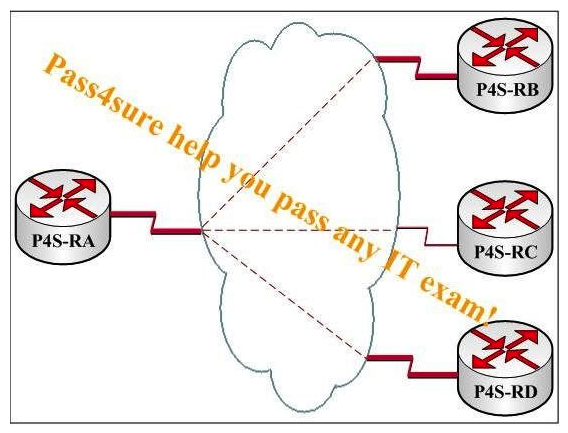
(Multiple Choice)
4.9/5  (32)
(32)
You have been asked to establish a design that will allow your company to migrate from a WAN service to a Layer 3 VPN service. In your design, you are keeping some WAN links between critical sites as a backup for this service. You plan to use OSPF as your IGP and BGP for the PE-CE protocol. When the Layer 3 VPN service is available, how will you prevent transit traffic over the backup links?
(Multiple Choice)
4.8/5  (38)
(38)
Which three characteristics of the Single Tier and the Dual Tier Headend Architectures for DMVPN designs are true? (Choose three.)
(Multiple Choice)
4.8/5  (31)
(31)
Which one of the following technologies could offer effective authentication and port-based access control in a wireless network by use of static WEP keys?
(Multiple Choice)
4.7/5  (36)
(36)
How many broadcast segments are contained in this network according to the exhibit? 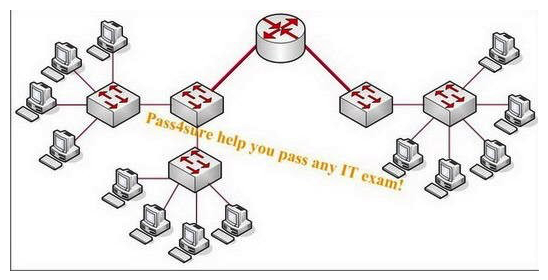
(Multiple Choice)
4.8/5  (38)
(38)
Intermediate system to intermediate system (IS-IS), is a protocol used by network devices (routers) to determine the best way to forward datagrams through a packet-switched network, a process called routing. A client has approached you about deploying very fast IS-IS hello timers across an intercontinental high speed SONET link. What's your option?
(Multiple Choice)
4.8/5  (28)
(28)
You are designing an optical network. Your goal is to ensure that your design contains the highest degree of resiliency. In which two ways will you leverage a wavelength-switched optical network solution in your network design? (Choose two.)
(Multiple Choice)
4.9/5  (30)
(30)
A network vulnerability scanner is part of which critical element of network and system security?
(Multiple Choice)
4.8/5  (35)
(35)
Refer to the exhibit. 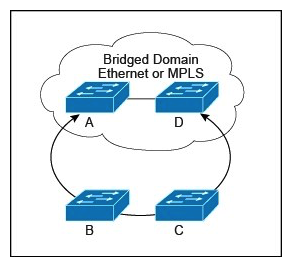 Which two options provide the best loop protection in this topology, regardless of a bridged domain configuration? (Choose two.)
Which two options provide the best loop protection in this topology, regardless of a bridged domain configuration? (Choose two.)
(Multiple Choice)
4.9/5  (29)
(29)
Which way can most effectively improve BGP convergence in the event that a point-to-point link, over which an EBGP session is running, fails?
(Multiple Choice)
4.8/5  (43)
(43)
Showing 201 - 220 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)