Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on the core MPLS network (P routers). The goal of the network design is to provide a complete CoS solution to all customers that purchase services such as dedicated Internet access, MPLS L3VPN, and L2VPN (pseudowire). Service Provider XYZ has these design requirements: - The network supports four service queues with equal treatment for delay, jitter, and packet loss. - Queues are numbered 0-3, where 0 is the default queue. - Three queues have one treatment. - One queue has either one or two treatments. If your design includes eight CoS queues on the Service Provider XYZ MPLS PE router ingress (CE facing) interface, how will customer traffic be classified as it enters the MLS P routers?
(Multiple Choice)
4.7/5  (31)
(31)
Refer to the exhibit. 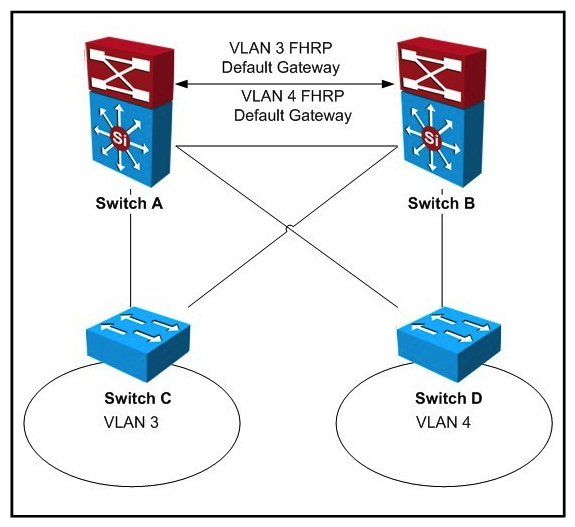 If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
(Multiple Choice)
4.9/5  (32)
(32)
Observe the following exhibit carefully. Router P4S-A receives a packet destined for loopback 10 on router P4S-D. Which path should this packet take on its way to the destination interface? 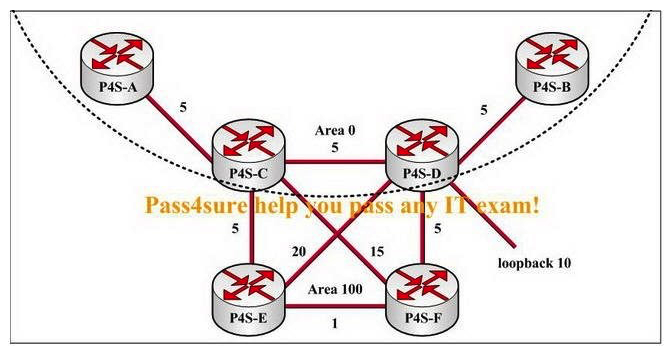
(Multiple Choice)
4.7/5  (27)
(27)
You are a network designer and have been asked to consult with your server operations team to further enhance the security of the network. The operations team provides you with these details about the network: - A pool of servers is accessed by numerous data centers and remote sites. - The servers are accessed via a cluster of firewalls. - The firewalls are configured properly and are not dropping traffic. - The firewalls occasionally cause asymmetric routing of traffic within the server data center. Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
(Multiple Choice)
4.8/5  (37)
(37)
Tesla Radio GmbH is going to build a new research lab network based on a set of switches that would connect to their existing enterprise network. They are considering a design that would guarantee loop- free behavior within the set of switches. The design would also allow the group of switches to seem like a single switch to the enterprise network, because it is owned by a separate administrative group. Which Spanning Tree Protocol should be used to support the design requirements?
(Multiple Choice)
4.8/5  (45)
(45)
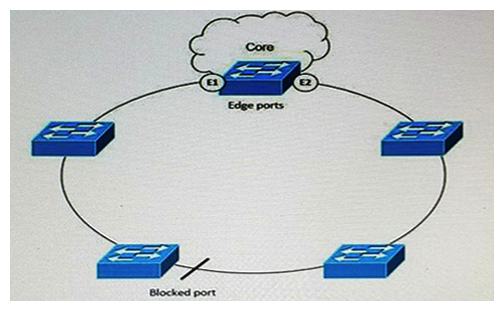 Refer to the exhibit. As the new network designer for a manufacturing company, you are designing this resilient Ethernet ring for the plant Ethernet network that is connected to the core, which does not use STP. Both edge ports are on the same switch in a ring segment. There is connectivity between the edge ports throughout the segment, so you create a redundant connection between any two switches in the ring. Which four options are characteristics of this design? (Choose four.)
Refer to the exhibit. As the new network designer for a manufacturing company, you are designing this resilient Ethernet ring for the plant Ethernet network that is connected to the core, which does not use STP. Both edge ports are on the same switch in a ring segment. There is connectivity between the edge ports throughout the segment, so you create a redundant connection between any two switches in the ring. Which four options are characteristics of this design? (Choose four.)
(Multiple Choice)
4.8/5  (46)
(46)
You are identifying performance management requirements for a VoIP migration. What three key performance indicators would you use to track media quality? (Choose three.)
(Multiple Choice)
4.8/5  (25)
(25)
A planned EBGP network will use OSPF to reach the EBGP peer addresses. Which of these conditions should be avoided in the design that could otherwise cause the peers to flap continuously?
(Multiple Choice)
4.8/5  (34)
(34)
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during TCN in a Layer 2 switched network with many VLANs?
(Multiple Choice)
4.9/5  (28)
(28)
Refer to the exhibit. 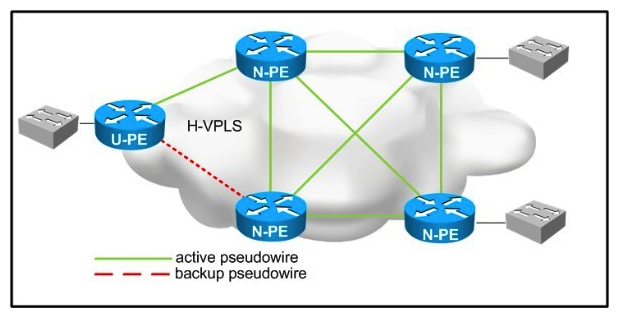 You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
(Multiple Choice)
4.9/5  (38)
(38)
While deploying IGP non-stop forwarding (NSF), which practice is the best for tuning routing protocol hello and dead timers?
(Multiple Choice)
4.8/5  (28)
(28)
When creating a network design, which one of these options provides for basic Layer 2 client isolation to prevent broadcast traffic exposure?
(Multiple Choice)
4.9/5  (33)
(33)
A company plans to use BFD between its routers to detect a connectivity problem inside the switched network. An IPS is transparently installed between the switches. Which packets should the IPS forward for BFD to work under all circumstances?
(Multiple Choice)
5.0/5  (42)
(42)
RSVP is short for Resource Reservation Protocol. Which statement is true about the RSVP protocol?
(Multiple Choice)
4.9/5  (33)
(33)
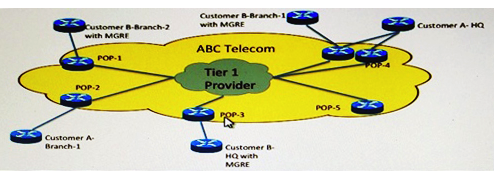 Refer to the exhibit. Company ABC is a Tier 3 service provider that offers Layer 2 and Layer 3 transport for small/medium enterprise customers in the US. Most of their network is built on Layer 2 MPLS circuits from a Tier 1 provider. Many Company ABC customers are using overlay VPN technologies and independent routing protocols, and they are affected with unacceptable convergence time after every major outage in the core of the Tier 1 provider. Which long-term redesign increases network availability?
Refer to the exhibit. Company ABC is a Tier 3 service provider that offers Layer 2 and Layer 3 transport for small/medium enterprise customers in the US. Most of their network is built on Layer 2 MPLS circuits from a Tier 1 provider. Many Company ABC customers are using overlay VPN technologies and independent routing protocols, and they are affected with unacceptable convergence time after every major outage in the core of the Tier 1 provider. Which long-term redesign increases network availability?
(Multiple Choice)
4.8/5  (26)
(26)
You have multiple MPLS LSP domains that you want to internetwork. Your provider's backbone is IP. How to internetwork without disrupting the outlying MPLS domains or the provider?
(Multiple Choice)
4.8/5  (38)
(38)
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on the core MPLS network (P routers). The goal of the network design is to provide a complete CoS solution to all customers that purchase services such as dedicated internet access, MPLS L3VPN, and L2VPN (pseudowire). Service Provider XYZ has these design requirements: How would you design your solution to map the DSCP value properly so that the traffic is assigned to the respective queues in the Service Provider XYZ MPLS core network?
(Multiple Choice)
4.7/5  (39)
(39)
You are designing a network that includes IP QoS. Which two architectures could be used to ensure that IP QoS is implemented properly? (Choose two.)
(Multiple Choice)
4.8/5  (41)
(41)
You are tasked with implementing a 1000-phone remote access solution, where phones will traverse a WAN edge router. Assuming all of the following features are supported in a hardware-assisted manner, which of the following will have the most detrimental impact on the delay of the packet?
(Multiple Choice)
4.9/5  (40)
(40)
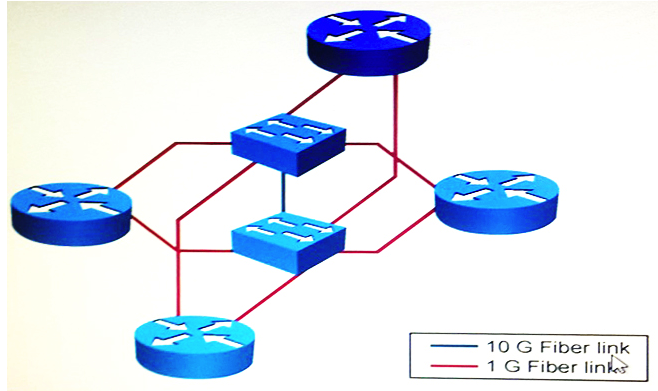 Refer to the exhibit. The two Ethernet switches are in close proximity to each other. Assuming that the IGP timers have already been tuned for fast convergence, which additional change provides for the fastest network convergence time?
Refer to the exhibit. The two Ethernet switches are in close proximity to each other. Assuming that the IGP timers have already been tuned for fast convergence, which additional change provides for the fastest network convergence time?
(Multiple Choice)
4.9/5  (46)
(46)
Showing 541 - 560 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)