Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
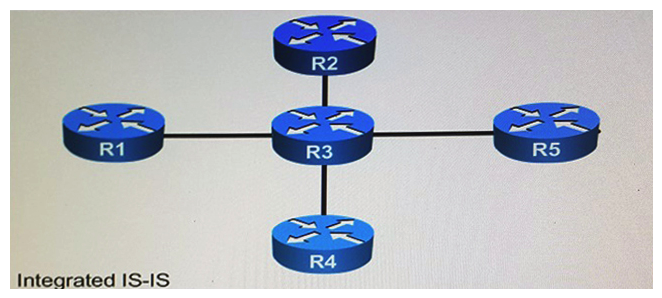 Refer to the exhibit. You designed an IPv6 migration plan, and now you need to determine the impact on the existing IPv4 network. Assume default IS-IS parameters. What is likely to happen when you enable IPv6 routing on the link between R3 and R2, starting at R3?
Refer to the exhibit. You designed an IPv6 migration plan, and now you need to determine the impact on the existing IPv4 network. Assume default IS-IS parameters. What is likely to happen when you enable IPv6 routing on the link between R3 and R2, starting at R3?
(Multiple Choice)
4.9/5  (32)
(32)
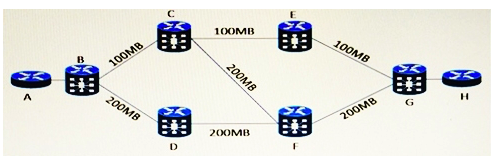 Refer to the exhibit. The customer uses Gigabit Ethernet on all router interfaces and gets point-to-point Layer 2 VPN connections from their Telco. This network runs IS-IS with default parameters. In which to circuits should you manually decrease the interface metric to allow bidirectional traffic to take the high-speed links between router A and router H? (Choose two.)
Refer to the exhibit. The customer uses Gigabit Ethernet on all router interfaces and gets point-to-point Layer 2 VPN connections from their Telco. This network runs IS-IS with default parameters. In which to circuits should you manually decrease the interface metric to allow bidirectional traffic to take the high-speed links between router A and router H? (Choose two.)
(Multiple Choice)
4.9/5  (30)
(30)
Which is a requirement for performing attack detection by use of anomaly detection technologies?
(Multiple Choice)
4.7/5  (31)
(31)
The headend router propagates which two resources for constrained based path computation with MPLS Traffic Engineering? (Choose two.)
(Multiple Choice)
4.9/5  (38)
(38)
Refer to the exhibit. "Pass Any Exam. Any Time." - www.actualtests.com 16 Cisco 352-001 Exam 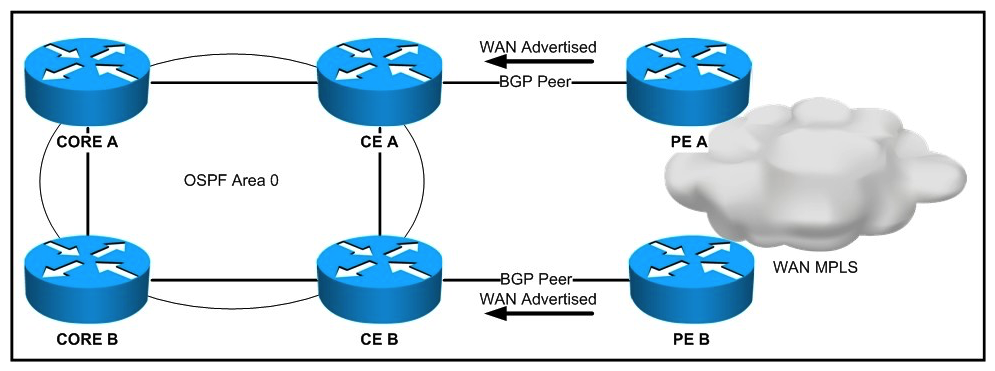 The design is being proposed for use within the network. The CE devices are OSPF graceful restart-capable, and the core devices are OSPF graceful restart-aware. The WAN advertisements received from BGP are redistributed into OSPF. A forwarding supervisor failure event takes place on CE A. During this event, how will the routes learned from the WAN be seen on the core devices?
The design is being proposed for use within the network. The CE devices are OSPF graceful restart-capable, and the core devices are OSPF graceful restart-aware. The WAN advertisements received from BGP are redistributed into OSPF. A forwarding supervisor failure event takes place on CE A. During this event, how will the routes learned from the WAN be seen on the core devices?
(Multiple Choice)
4.9/5  (29)
(29)
You work as a network engineer for the P4S company, study the exhibit carefully. For traffic from CE3 and destined for 10.1.1.1, what is the label at the bottom of the stack as the packet goes between ASBR2 and ASBR1? 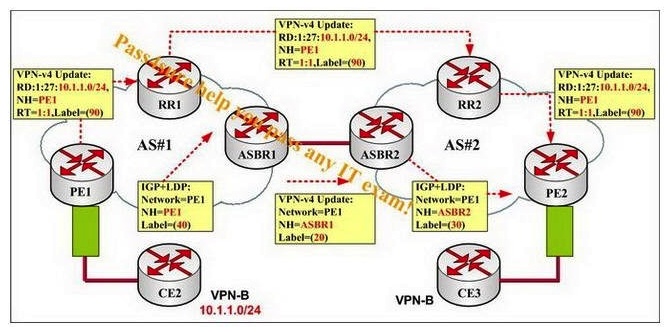
(Multiple Choice)
4.8/5  (43)
(43)
You are a network designer and have been asked to consult with your server operations team to further enhance the security of the network. The operations team provides you with these details about the network: A pool of servers is accessed by numerous data centers and remote sites. The servers are accessed via a cluster of firewalls. The firewalls are configured properly and are not dropping traffic. The firewalls occasionally cause asymmetric routing of traffic within the server data center. Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
(Multiple Choice)
4.9/5  (35)
(35)
In secure IP multicast, which protocol handles group key management?
(Multiple Choice)
4.9/5  (36)
(36)
Which design criteria drives the selection of G.8032 in an ISP network design?
(Multiple Choice)
4.8/5  (35)
(35)
Which content networking device allows bandwidth configuration settings so that streaming content will not interfere with other network traffic?
(Multiple Choice)
4.8/5  (42)
(42)
Company A has grown nationwide in the U.S., and each new remote branch has a Metro Ethernet circuit provisioned back to the data center at the headquarters on the West Coast. The operations team says that it cannot manage hundreds of circuits as the company continues to grow. You review the topology and notice that many of the branches are close to each other in geographical zones. How can you redesign this network to improve manageability and increase scalability?
(Multiple Choice)
4.9/5  (32)
(32)
Refer to the exhibit. 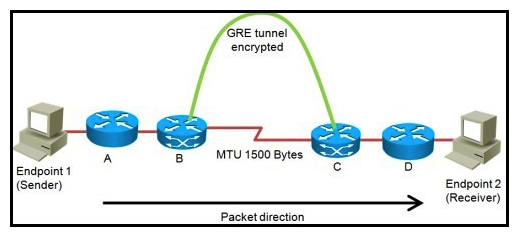 You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
(Multiple Choice)
4.8/5  (43)
(43)
Study the exhibit carefully. Routers P4S-RA, P4S-RB, P4S-RC, and P4S-RD are all performing OSPF within a single area and have OSPF graceful restart configured and running. 10.1.2.0/24 is being advertised only through BGP and the best path between routers P4S-RC and P4S-RD is through router P4S-RB. Configure BGP graceful restart on routers P4S-RB, P4S-RC, and P4S-RD, but not on router P4S-RA. What will happen to traffic from 10.1.1.0/24 to 10.1.2.0/24 after router P4S-RB performs a graceful restart? 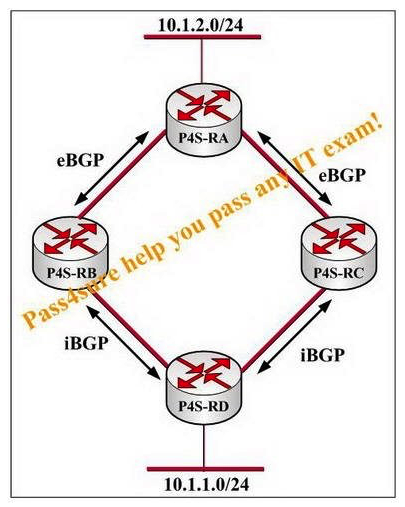
(Multiple Choice)
4.8/5  (33)
(33)
The VPN termination function provides the ability to connect two networks together securely over the internet. Which of these is true of IP addressing with regard to VPN termination?
(Multiple Choice)
4.8/5  (40)
(40)
In this network presented in the following exhibit, traffic destined for 10.1.3.1 arrives at P4S-R5. Which path will be taken by the traffic from here and why? 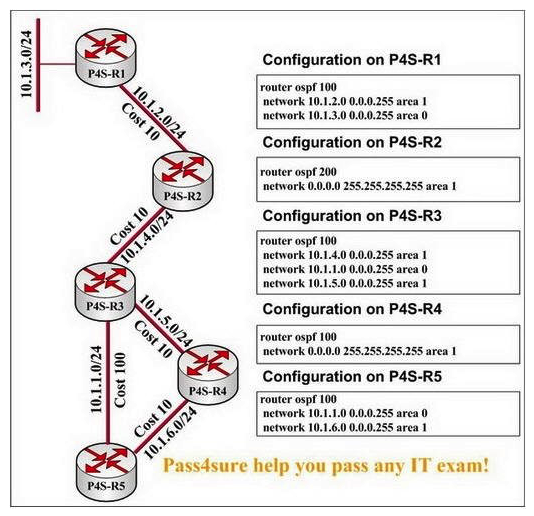
(Multiple Choice)
4.8/5  (36)
(36)
Senior management would like you to evaluate the risks to your network of offering VPWS, VPLS, GRE, or other tunneling services to your fiber-connected client base. Clients prefer to use Layer 2 switches as CEs. Which two tunneling services expose your network to minimal risk and satisfy the clients' requirements, including separation between providers and customer networks? (Choose two.)
(Multiple Choice)
4.7/5  (31)
(31)
What is the reason that IGP advertisements should be disabled on an access link where a host is attached?
(Multiple Choice)
4.8/5  (39)
(39)
Refer to the exhibit. 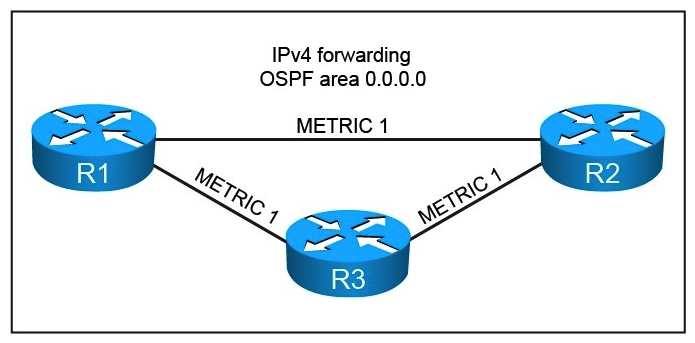 You are asked to design this OSPF network to converge within 60 ms for unicast packets after a topology change due to a single link failure. Which technology can be enabled while conforming to the design requirements?
You are asked to design this OSPF network to converge within 60 ms for unicast packets after a topology change due to a single link failure. Which technology can be enabled while conforming to the design requirements?
(Multiple Choice)
4.9/5  (33)
(33)
The following exhibit shows us that all the routers in this network are running EIGRP on all links. In Network 1, all links are the same cost. In Network 2, router P4S-RE prefers the path through P4S-RC, and does not have a feasible successor. Which network converges faster in the event of the failure of the link between router P4S-RA and 10.1.1.0/24? 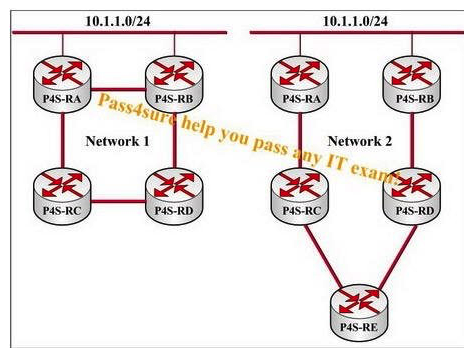
(Multiple Choice)
5.0/5  (37)
(37)
How should multiple OSPF areas be designed when deployed on a classic three-layer (core/distribution/access) network hierarchy?
(Multiple Choice)
4.8/5  (43)
(43)
Showing 461 - 480 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)