Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
A service provider would like to maximize forwarding memory, routing memory, and CPU resources on PE devices for enterprise customers having very few sites (two to three) and a large number of prefixes (several thousand). Which service should be offered by the service provider to these customers?
(Multiple Choice)
4.8/5  (38)
(38)
A customer wants to understand the benefits of a proposed network design that utilizes SNMPv3. Which two network threats is SNMPv3 effective against? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
Virtual private LAN service (VPLS) is a way to provide Ethernet based multipoint to multipoint communication over IP/MPLS networks. Which three drawbacks are of VPLS? (Choose three.)
(Multiple Choice)
4.9/5  (30)
(30)
Which control plane problem can be prevented by implementing QoS, and how to eliminate the problem?
(Multiple Choice)
4.9/5  (31)
(31)
Your firm has been awarded a contract to design a Criminal Justice Information Services Version 5.0- compliant network utilizing advanced authentication policies. Which two methods could be utilized? (Choose two.)
(Multiple Choice)
4.8/5  (39)
(39)
Which description of the RPF check in the multicast forwarding traffic is true?
(Multiple Choice)
4.8/5  (37)
(37)
A multicast network is using bidirectional PIM. Which two actions, when combined, can achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two.)
(Multiple Choice)
4.8/5  (31)
(31)
What is the key design principle for the core layer when using a classic hierarchical network model?
(Multiple Choice)
4.8/5  (28)
(28)
What are two base components of both a source-based remotely triggered black hole and a destination-based remotely triggered black hole filtering solution? (Choose two.)
(Multiple Choice)
4.8/5  (42)
(42)
A company is planning to connect its 30 sites with a VPLS WAN backbone. A router at each site should establish neighborships with all other routers using the OSPF routing protocol. Which three points must be considered regarding DR and BDR when different router platforms are used? (Choose three.)
(Multiple Choice)
4.9/5  (36)
(36)
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during TCN in a Layer 2 switched network with many VLANs? "Pass Any Exam. Any Time." - www.actualtests.com 55 Cisco 352-001 Exam
(Multiple Choice)
4.8/5  (31)
(31)
The Customer X network consists of an MPLS core, IS-IS running as IGP, a pair of BGP route reflectors for route propagation, and a few dozens of MPLS-TE tunnels for specific tactical traffic engineering requirements. The customer engineering department has some questions about the use of the Overload Bit in the IS-IS networks and how it could be used to improve their current network design. Which three options about the Overload Bit are true? (Choose three.)
(Multiple Choice)
4.8/5  (43)
(43)
Your customer asks you to assist with their traffic policy design. They want to guarantee a minimum amount of bandwidth to certain traffic classes. Which technique would you advise them to implement?
(Multiple Choice)
5.0/5  (30)
(30)
Service provider XYZ plans to provide dedicated Internet access and MPLS L3VPN services to business customers. XYZ has these design specifications: In what two ways can the MP-BGP be removed from the MPLS P core routers and still provide dedicated Internet access and MPLS L3VPN services? (Choose two.)
(Multiple Choice)
4.9/5  (32)
(32)
Observe the following exhibit carefully. Assume that routers P4S-RJ, P4S-RK, P4S-RL, and P4S-RM are optimally aggregating towards routers P4S-RA, P4S-RB, P4S-RC, and P4S-RE. Which two links will be removed to improve fault isolation? 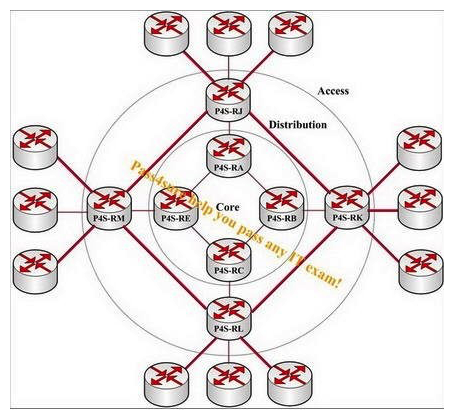
(Multiple Choice)
4.8/5  (39)
(39)
You work as a network designer for a company that is replacing their Frame Relay WAN with an MPLS VPN service, where the PE-to-CE routing protocol is BGP. The company has 3000 routes in their distribution routers, and they would like to advertise their access routers through the MPLS network. Their service provider, however, only supports 1000 prefixes per VRF. Which two design solutions can be applied to ensure that your access routers will be able to reach all devices in your network? (Choose two.)
(Multiple Choice)
4.7/5  (31)
(31)
Users at the Charleville Company began experiencing high network delays when Internet connectivity was enabled for all users. After investigating the traffic flow, you determine that peer-to-peer traffic from a music download site is consuming a large amount of bandwidth. Which QoS mechanism can you implement to improve the network response time?
(Multiple Choice)
4.9/5  (32)
(32)
When designing a network, which two security features should be added to the design to protect hosts from potential IPv6 neighbor discovery denial of service attacks at the access layer? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
A service provider is offering four classes of service, with each class mapped to a separate queue. Some customers complain about receiving out-of-order packets, which cause application degradation. Which QoS policy activity most likely causes these out-of-order packets?
(Multiple Choice)
4.8/5  (36)
(36)
Refer to the exhibit. 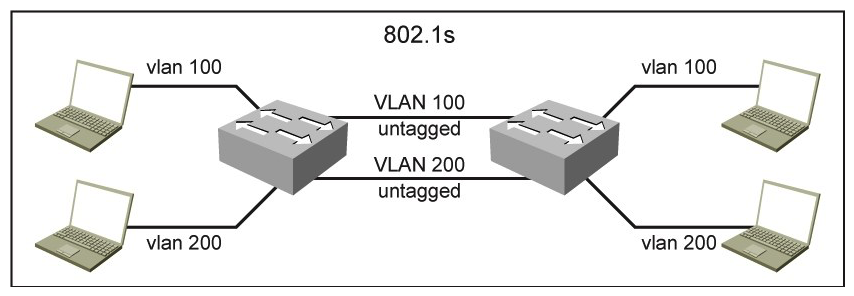 You are designing a network using the Multiple Spanning Tree Protocol for loop avoidance. VLAN trunking is not allowed due to security requirements. Which option describes how you can design this Layer 2 network while using untagged interfaces between both switches?
You are designing a network using the Multiple Spanning Tree Protocol for loop avoidance. VLAN trunking is not allowed due to security requirements. Which option describes how you can design this Layer 2 network while using untagged interfaces between both switches?
(Multiple Choice)
4.9/5  (34)
(34)
Showing 41 - 60 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)