Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which two design considerations must be considered when introducing FCoE into an existing network? (Choose two.)
(Multiple Choice)
5.0/5  (36)
(36)
In a PIM sparse mode network, how to restore the flow of multicast traffic when a link fails along a branch of a multicast distribution tree?
(Multiple Choice)
4.8/5  (33)
(33)
A network designer is working with a company to improve convergence at the Layer 2 control plane and decides to use LACP. Which of these components does LACP use to create the system ID?
(Multiple Choice)
4.9/5  (38)
(38)
Refer to the exhibit. 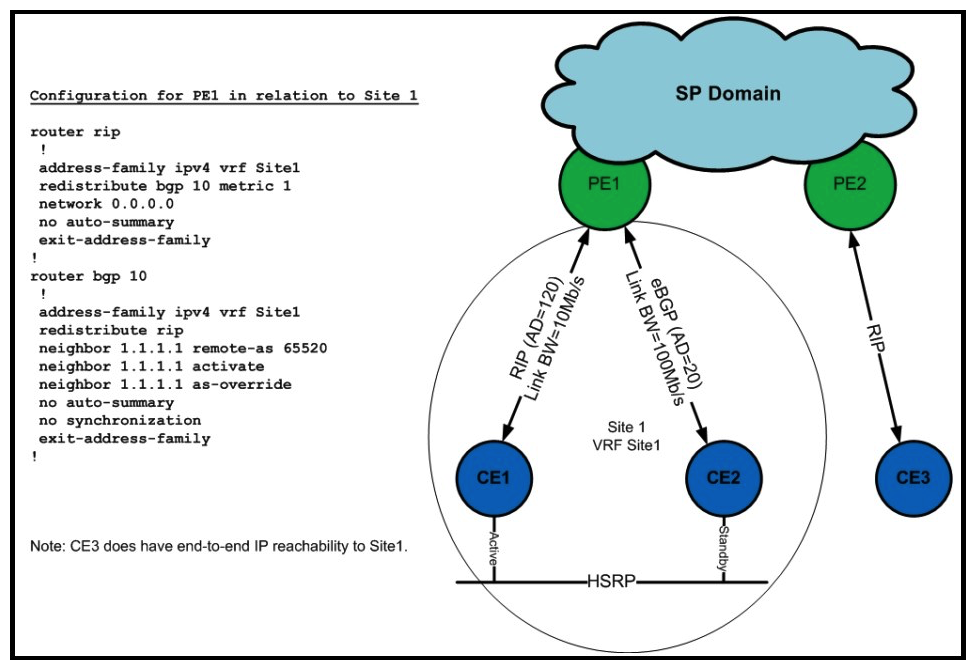 Your junior design engineer presents this configuration design. What is the next-hop router for "Pass Any Exam. Any Time." - www.actualtests.com 19 Cisco 352-001 Exam CE3, and why?
Your junior design engineer presents this configuration design. What is the next-hop router for "Pass Any Exam. Any Time." - www.actualtests.com 19 Cisco 352-001 Exam CE3, and why?
(Multiple Choice)
4.8/5  (41)
(41)
All network devices provided in the following exhibit are running IPv6. When host P4S-A is attached to this link, how will it discover the presence of routers P4S-RB and P4S-RC? 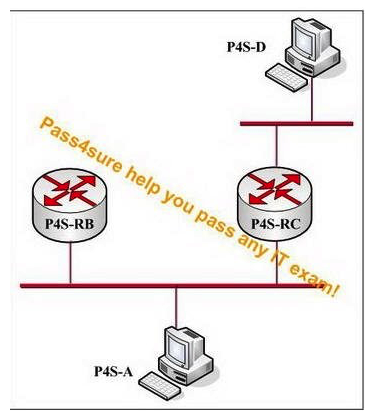
(Multiple Choice)
4.8/5  (40)
(40)
Refer to the exhibit. 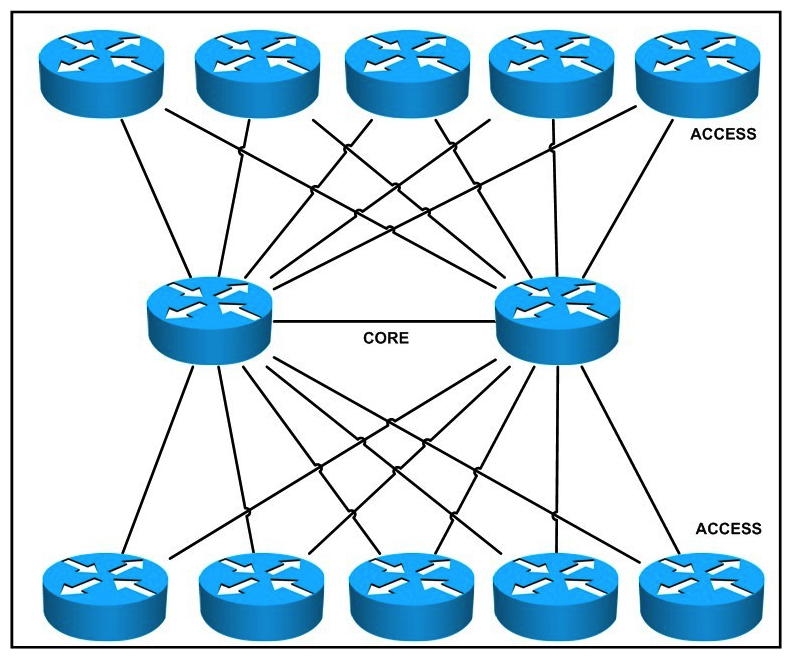 What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?
What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?
(Multiple Choice)
4.9/5  (37)
(37)
You are designing a WAN network solution with EIGRP based on VPLS. The interface speed is 10 Mb/s, but the access rate of the WAN connection is 256 Kb/s. What should you include in the network design, in order to avoid potential issues with EIGRP?
(Multiple Choice)
4.8/5  (39)
(39)
A company requests that you consult with them regarding the design of their production, development, and test environments. They indicate that the environments must communicate effectively, but they must be kept separate due to the inherent failures on the development network. What will be configured on the links between the networks to support their design requirements?
(Multiple Choice)
4.7/5  (35)
(35)
Refer to the exhibit. 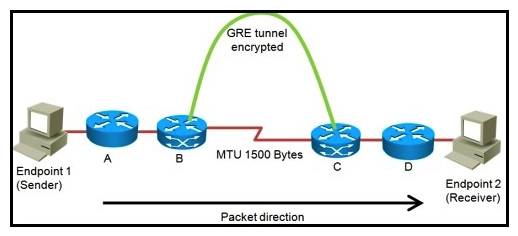 "Pass Any Exam. Any Time." - www.actualtests.com 53 Cisco 352-001 Exam You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
"Pass Any Exam. Any Time." - www.actualtests.com 53 Cisco 352-001 Exam You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
(Multiple Choice)
4.7/5  (36)
(36)
Which two descriptions are not correct about IS-IS? (Choose two.)
(Multiple Choice)
4.8/5  (38)
(38)
In an MPLS-VPN environment, what is the effect of configuring an identical set of route targets for a particular VRF, but then configuring nonidentical route distinguisher across multiple PE devices?
(Multiple Choice)
4.8/5  (35)
(35)
Refer to the exhibit. 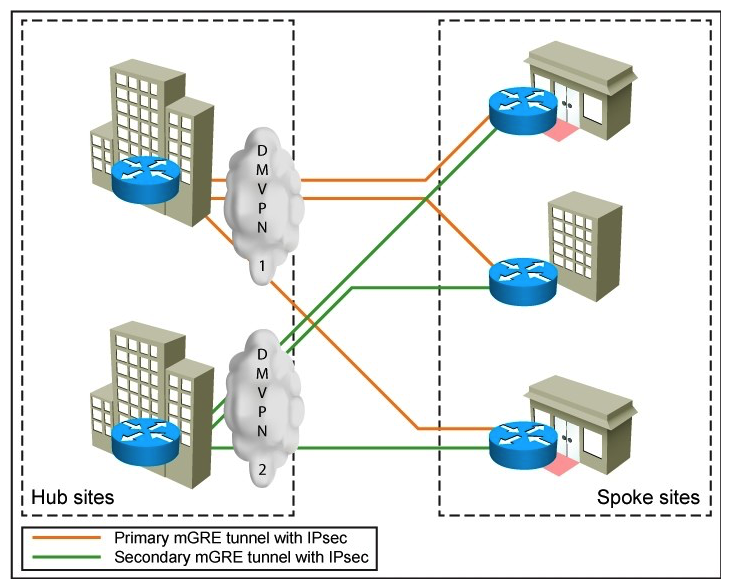 Which two options are two characteristics of the single-tier headend architecture for DMVPN designs? (Choose two.)
Which two options are two characteristics of the single-tier headend architecture for DMVPN designs? (Choose two.)
(Multiple Choice)
4.7/5  (28)
(28)
Which option describes a design benefit of Bridge Assurance?
(Multiple Choice)
4.9/5  (30)
(30)
Refer to the exhibit. 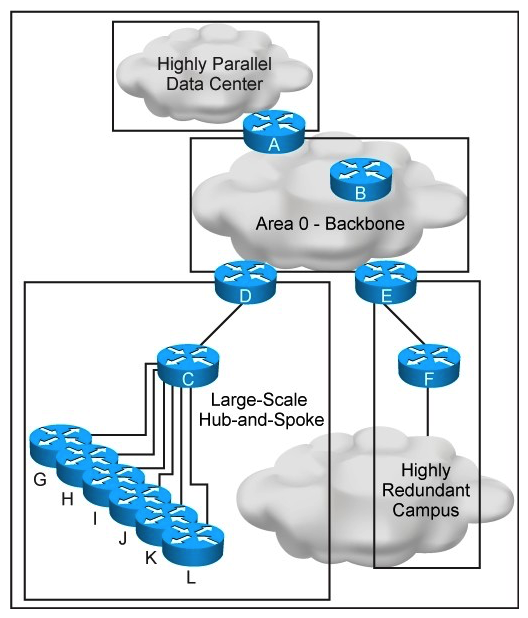 This new OSPF network has four areas, but the hub-and-spoke area experiences frequent flapping. You must fix this design failure. Which two mechanisms can you use to isolate the data center area from the hub-and-spoke area without losing IP connectivity? (Choose two.)
This new OSPF network has four areas, but the hub-and-spoke area experiences frequent flapping. You must fix this design failure. Which two mechanisms can you use to isolate the data center area from the hub-and-spoke area without losing IP connectivity? (Choose two.)
(Multiple Choice)
4.7/5  (37)
(37)
Refer to the exhibit. 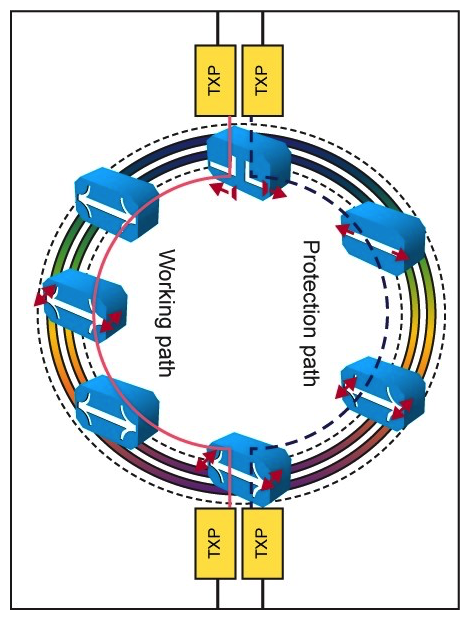 In the DWDM network, a ring topology carries multiple services between two sites. Which option describes the employed protection design?
In the DWDM network, a ring topology carries multiple services between two sites. Which option describes the employed protection design?
(Multiple Choice)
4.7/5  (39)
(39)
In the network presented in the following exhibit. Traffic destined for 10.1.3.1 arrives at P4S-R1. Which path will the traffic take from here and why? 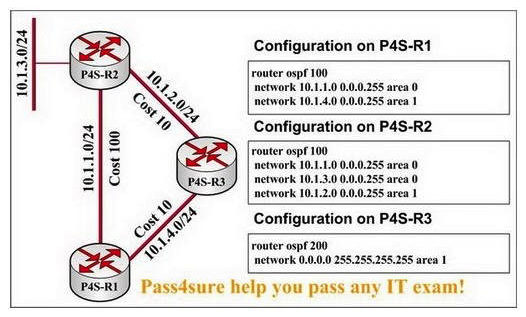
(Multiple Choice)
4.9/5  (34)
(34)
Which attack type may be indicated by unsolicited ACKs directed toward an unused portion of a network's IP address space?
(Multiple Choice)
4.9/5  (31)
(31)
The Internet Group Management Protocol (IGMP) is a communications protocol used to manage the membership of Internet Protocol multicast groups. IGMP is used by IP hosts and adjacent multicast routers to establish multicast group memberships .What is the purpose of IGMP in a multicast implementation?
(Multiple Choice)
4.9/5  (31)
(31)
Showing 101 - 120 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)